Table of Contents
Selecting the right managed detection and response (MDR) provider is one of the most consequential decisions security leaders make. The wrong choice can leave critical gaps in your defenses, waste resources, and erode trust with stakeholders. The right partner becomes an extension of your team—strengthening your security posture, freeing internal resources for strategic work, and providing genuine peace of mind. But with dozens of vendors claiming to offer “best-in-class” MDR services, how do you separate marketing noise from meaningful capabilities? This guide breaks down the essential criteria that matter, the questions you must ask, and the red flags that should send you looking elsewhere.
How do I compare MDR providers?
Comparing MDR providers requires moving beyond surface-level marketing claims to evaluate real capabilities, proven results, and cultural fit. Gartner advises MDR buyers to focus on the ability to provide context-driven insights that will directly impact business objectives, as wide-scale collection of telemetry and automated analysis are insufficient when facing advanced cyber threats.
When evaluating MDR service providers, understanding what constitutes “good response” can make the difference between a security partnership that strengthens your organization and one that leaves critical gaps in your defense strategy. Effective response centers on four fundamental qualities: speed, clarity, precision, and partnership.
Speed represents the cornerstone of effective MDR response. Cyber attacks unfold rapidly, often within minutes or hours of initial compromise. The time between detection and response directly determines how much damage an attacker can inflict. Industry-leading providers achieve mean time to respond (MTTR) measured in minutes—Expel delivers a 17-minute MTTR on high and critical incidents—rather than the hours or days common with traditional security services.
Clarity means receiving actionable intelligence rather than technical jargon. MDR providers should deliver clear answers about what happened, why it matters, and what to do about it. According to Forrester, providers who combine human delivery with software-enabled platforms create transparency, helping security teams understand incidents and make informed decisions.
Precision ensures you receive high-fidelity alerts representing genuine threats, not false positives that waste your team’s time. Quality MDR services dramatically reduce alert noise—customers report decreases in false positive rates from over 99% down to below 10%.
Partnership distinguishes transactional vendors from true collaborators. The best MDR providers function as extensions of your team, understanding your business context, adapting to your needs, and helping you strengthen overall security posture rather than just responding to incidents.
Create a structured comparison framework
Rather than getting overwhelmed by vendor feature lists, organize your evaluation criteria around four key categories:
- Technology & coverage: What attack surfaces, platforms, and integrations does the provider support?
- People & expertise: What caliber of security professionals will be monitoring your environment?
- Process & methodology: How does the provider detect, investigate, and respond to threats?
- Price & business terms: What’s the true total cost of ownership, including hidden fees and contractual flexibility?
What are good MDR vendor selection criteria?
Effective vendor assessment and selection requires evaluating both technical capabilities and operational factors. Here’s a comprehensive checklist of criteria organized by category:
Technology coverage & integration
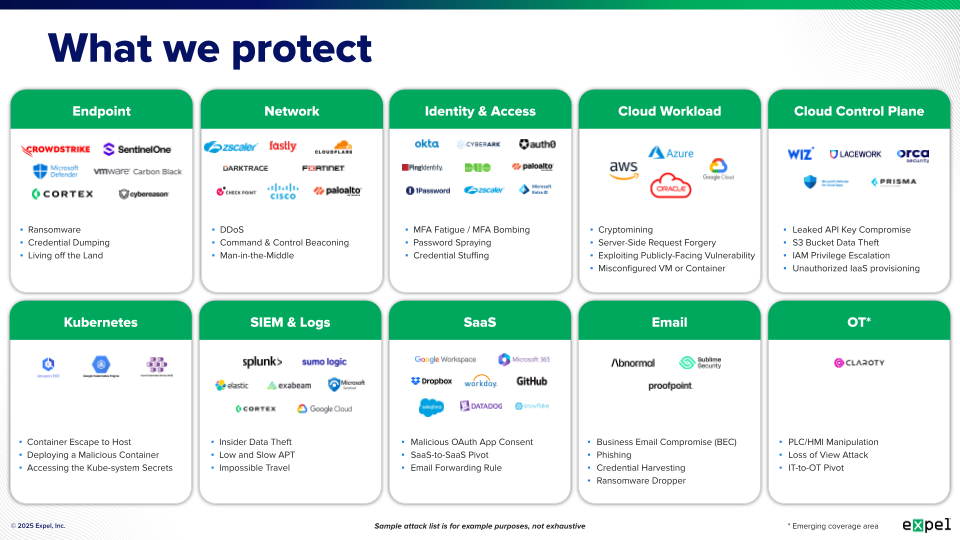
Attack surface coverage:
- Endpoint protection: Support for Windows, macOS, Linux endpoints
- Cloud environment monitoring: AWS, Azure, Google Cloud, Oracle coverage
- Kubernetes & container security: Cloud-native application protection
- SaaS application monitoring: Office 365, Google Workspace, Salesforce, etc.
- Network traffic analysis: East-west and north-south traffic visibility
- Email security integration: Phishing detection and response
- Identity & access management: Authentication, privilege escalation detection
Integration capabilities:
- Bring-your-own-tech (BYOT) approach: Works with existing security tools
- API-based connectivity: No agents required, rapid onboarding
- SIEM enhancement: Enriches existing SIEM investments
- Custom detection support: Ability to create tailored detection rules
- Tool flexibility: Can swap technologies without service disruption
- Data normalization: Ingests and correlates data from disparate sources
- Evidence preservation: Maintains forensic data for investigations
Expel’s approach provides 130+ integrations across attack surfaces with native, enriched, high-fidelity alerts, allowing customers to maximize their existing security investments rather than forcing tool replacements.
Detection & response capabilities
- Advanced threat detection: Behavioral analytics, anomaly detection, threat intelligence integration
- Custom detection engineering: Expel-written detections aligned to MITRE ATT&CK framework
- False positive reduction: AI-driven filtering to surface only genuine threats
- Hypothesis-based threat hunting: Proactive search for hidden adversaries
- Mean time to detect (MTTD): Industry-leading detection speed
- Mean time to respond (MTTR): Rapid containment and remediation
- Active response capabilities: Direct execution of response actions, not just recommendations
- Automated remediation: Immediate containment for critical threats
- Incident investigation depth: Root cause analysis and full attack timeline reconstruction
- Context enrichment: Additional intelligence layered onto alerts
- Cross-environment correlation: Connecting related events across different systems
- Continuous detection improvement: Regular tuning and optimization based on threat landscape
According to Forrester, active response capabilities have become table stakes for MDR service providers, though depth and scope vary significantly across the industry.
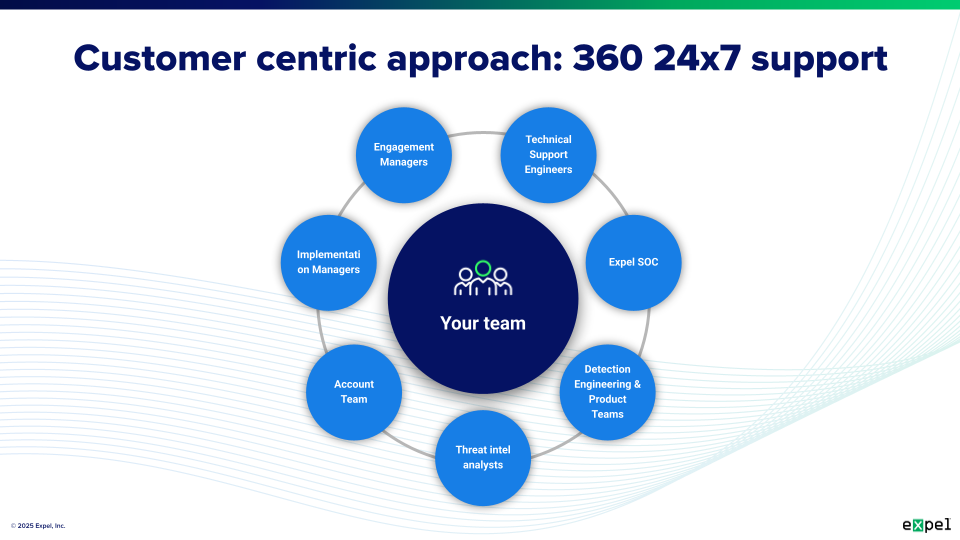
Analyst expertise & team quality
- 24×7 coverage: Round-the-clock monitoring with consistent quality
- Experienced security analysts: Seasoned professionals, not junior staff
- Specialization depth: Expertise in cloud security, identity threats, ransomware, etc.
- Analyst-to-customer ratio: Sufficient resources to provide quality service
- Direct SOC access: Ability to communicate directly with analysts investigating incidents
- Dedicated customer success: Named contacts who understand your environment
- Continuous analyst training: Ongoing education on emerging threats and techniques
- Quality control processes: Peer review, performance metrics, error tracking
- Incident response coordination: Experienced IR specialists for major incidents
- Business context understanding: Analysts who learn your organization’s unique needs
Transparency & visibility
- Real-time investigation visibility: Watch investigations unfold as they happen
- Full audit trail access: Complete record of all actions taken
- Comprehensive reporting: Incident details, trends, metrics dashboards
- Event search capabilities: Query historical events and understand triage decisions
- Metrics transparency: MTTD, MTTR, false positive rates, coverage statistics
- Detection logic visibility: Understand what triggers alerts in your environment
- Product roadmap access: See what capabilities are coming
- Direct platform access: Use the same tools as the MDR provider, with platform transparency as well
- Collaboration features: Real-time communication within investigation platform
- Alert contextualization: Understanding why specific events were/weren’t escalated
- Performance benchmarking: Compare your results to industry standards
- Quality metrics: Visibility into provider accuracy and error rates
Expel’s transparency approach provides customers with Event Search capabilities, allowing them to search standardized fields in the evidence database and see why events were or weren’t surfaced as alerts—a level of visibility uncommon in the MDR industry.
Operational excellence
- Onboarding speed: Time from contract to active monitoring
- Onboarding support: Dedicated resources to ensure smooth implementation
- Service customization: Ability to tailor service to specific needs
- SLA terms: Clear commitments with realistic targets
- Escalation procedures: Defined paths for urgent issues
- Change management: Handling environment changes without service disruption
- Documentation quality: Clear, comprehensive incident reports
- Knowledge transfer: Helping internal team learn from incidents
- Resilience recommendations: Proactive guidance for security improvements
- Industry certifications: SOC 2, ISO certifications, compliance support
- Reference accounts: Verifiable customer success stories
Forrester notes Expel’s rapid onboarding and unmatched transparency confirm the provider remains plugged into what MDR customers need.
What questions should I ask an MDR vendor?
Predictable RFP criteria and questions generate predictable answers, leaving one provider sounding like the rest. Here are revealing questions to make vendors stop and think:
Technology & integration questions
“Do I need to buy specific security tools to work with you?”
Red flag answer: “Yes, we require you to use XYZ tools for our service to work.”
Good answer: “We work with your existing technology. Without certain capabilities like EDR, our investigation and hunting abilities will be limited, but we can guide you in selecting appropriate tools if needed.”
A service provider should use the technology you already have and operationalize it—ingesting data your security products already produce and delivering answers about what matters. Quality providers should not force you to rip and replace your security stack.
“How do you handle cloud security differently than on-premises?”
This question separates providers who “speak cloud” from those who simply extend traditional approaches. Look for answers that acknowledge the unique security considerations of elastic infrastructure, ephemeral resources, IAM complexity, and cloud-native attack techniques.
“Can you show me actual examples of detections you’ve written for my industry?”
Generic threat detection rarely catches sophisticated attacks. Ask to see industry-specific detections, custom rules they’ve developed, and examples of how they adapt to unique customer environments.
People & process questions
“Will I work with the same analysts consistently, or random people from a pool?”
Relationship continuity matters. Some providers assign dedicated teams who learn your environment, while others route alerts to whoever’s available. Understanding this helps set expectations for service quality and business context awareness.
“How do you ensure analyst quality doesn’t decline as you scale?”
Ask about hiring standards, training programs, quality control processes, and how they measure analyst performance. Expel’s approach includes building technology and processes ensuring analysts aren’t burning out as the company grows and customers don’t see service decline.
“What happens when you make a mistake? Can you share an example?”
How a provider handles errors reveals their integrity and commitment to improvement. Look for transparency about mistakes, clear processes for acknowledging and correcting issues, and evidence of continuous improvement.
Response & performance questions
“What’s your actual mean time to respond, not just what your SLA promises?”
SLAs often represent minimum commitments rather than typical performance. Ask for real metrics from existing customers. Industry-leading providers deliver 20-minute MTTR or better, while mediocre services take hours.
“Do you provide recommendations, or do you take action in my environment?”
The distinction between “little r” and “big R” response matters. According to industry analysis, historically some providers would only identify threats and suggest actions, while others execute responses directly. Active response should now be table stakes.
“How do you measure false positive rates, and what’s yours?”
If a provider can’t articulate their false positive rate or doesn’t measure it, it’s concerning. Quality providers obsess over reducing noise—customers should see dramatic decreases from 99%+ false positives down to single digits.
Transparency & trust questions
“Can I watch your analysts work in real-time during an investigation?”
Full transparency differentiates genuine partners from black-box services. Can you see exactly what analysts are doing, when, and why? Expel’s Workbench platform provides complete visibility into investigations as they unfold.
“How will you adapt your service as my business changes?”
Your industry, geography, company, strategy, and team all evolve. How will the provider tune their service so it remains effective as you change? Look for evidence of customization, business context awareness, and flexibility.
“What metrics will you provide me, and how often?”
Comprehensive metrics should include MTTD, MTTR, alert volumes, false positive rates, threat trends, MITRE ATT&CK coverage, and improvement recommendations. Expel provides copious industry-standard metrics through Workbench, plus access to benchmarks helping customers compare themselves to industry standards.
Business & contractual questions
“What’s included in your base price, and what costs extra?”
Per-endpoint MDR pricing seems straightforward but can hide significant costs. Scrutinize “free” offers, understand what happens as you grow, and factor in integration, training, and operational adjustments required. Lack of pricing clarity can be an easy red flag to spot up front.
“How difficult is it to leave if things don’t work out?”
Consider extraction costs. How difficult and expensive would it be to transition to another provider if necessary? Flexible contracts with reasonable termination terms indicate provider confidence.
What are red flags in MDR vendors?
Certain warning signs should prompt serious concerns or disqualify vendors entirely from consideration:
Technology red flags
❌ Forced technology purchases: Requires you to buy specific tools as a condition of service
❌ Agent-based only approach: Can’t work with cloud services or modern SaaS applications
❌ Limited integration support: Supports fewer than 20-30 security platforms
❌ No BYOT flexibility: Inflexible about working with your existing investments
❌ Unclear detection methodology: Can’t explain how they identify threats
❌ Proprietary black-box systems: No visibility into detection logic or investigation process
Service delivery red flags
❌ Vague or slow response commitments: SLAs measured in hours rather than minutes
❌ “Little r” recommendations only: Won’t take direct action in your environment
❌ Offshore-only operations: May create communication barriers and quality concerns
❌ High analyst turnover: Constantly working with new, unfamiliar faces
❌ No direct analyst access: Communication filtered through account managers
❌ Inconsistent service quality: Performance varies significantly over time
Transparency red flags
❌ No platform access: Can’t see what they’re doing or how they’re working
❌ Limited reporting: Only monthly summaries without detail or metrics
❌ No visibility into investigations: Can’t watch investigations or understand analyst decisions
❌ Refuses to share performance metrics: Won’t disclose MTTD, MTTR, or false positive rates
❌ Can’t provide references: No verifiable customer success stories
❌ Overpromises capabilities: Claims to be perfect or never make mistakes
Business practice red flags
❌ Aggressive sales tactics: High-pressure, fear-based selling
❌ Unclear pricing: Hidden fees, confusing tiers, surprise costs
❌ Rigid contracts: No flexibility for business changes, punitive termination clauses
❌ Poor cultural fit: Doesn’t align with your organization’s values and operating style
❌ Limited industry experience: No proven track record in your sector
❌ Defensive about weaknesses: Can’t acknowledge limitations or areas for improvement
What makes a good MDR provider?
Beyond avoiding red flags, truly excellent MDR providers exhibit specific characteristics that create exceptional outcomes.
Look for MDR service providers who maintain industry certifications, participate in threat intelligence sharing communities, and demonstrate cybersecurity thought leadership. Independent research firm Forrester named Expel a Leader in The Forrester Wave™: Managed Detection and Response Services, Q1 2025, with five-out-of-five scores in 15 out of 21 criteria.
The best providers combine automation and AI with experienced analysts. Expel’s philosophy is AI makes SOC analysts better, not obsolete. Technology handles high-volume triage and evidence gathering, while expert humans provide context, business understanding, and complex decision-making.
Quality providers help you maximize existing investments, free your team for strategic work, and improve your security posture continuously—not just react to incidents.
Effective MDR service providers must continuously enhance response capabilities, including adopting new technologies, developing specialized expertise in emerging threat vectors, and maintaining agility to adapt services to changing client needs.
Should I do an MDR proof of concept?
Proof of concepts (POCs) can provide valuable hands-on experience with a provider, but they come with important considerations:
POCs are valuable when:
- You’re choosing between two finalists with similar capabilities on paper
- You have specific, complex requirements that need validation
- You want to test integration with unusual or proprietary technology
- You need to demonstrate value to skeptical stakeholders
- Your environment has unique characteristics that might affect service delivery
Gartner recommends investigating whether the MDR provider’s service can align with your business-driven requirements by using RFPs and proofs of concept, particularly when validating core, must-have requirements such as data residency.
Be aware POCs have limitations:
- Short timeframes may not reveal true service quality over months
- Vendors often assign their best resources to POCs, which may not reflect ongoing service
- POC environments may not reflect the complexity of production deployments
- Limited time window means you might not encounter diverse threat scenarios
- Setup and teardown consume significant internal resources
Consider these alternatives to traditional POCs:
- Customer reference calls: Speak with existing customers about their experiences
- Live demo with your data: See the platform working with your actual security tools
- Pilot program: Start with limited scope and expand if successful
- Trial period: Negotiate a shorter initial contract term with favorable exit terms
Many leading providers can demonstrate capabilities effectively through comprehensive demos and detailed reference discussions without requiring extensive POC investments.
What references should I check?
Speaking with existing customers provides insights you can’t get from vendor presentations. Structure your reference checks strategically:
Types of references to request
Ask for references matching your profile:
- Similar company size and industry
- Comparable technology stack and cloud maturity
- Same geographic region (if relevant for data residency)
- Organizations at similar security maturity levels
Also request references from customers who:
- Have been with the provider for 2+ years (to assess long-term satisfaction)
- Recently onboarded (to understand current implementation experience)
- Expanded their service over time (to gauge scalability)
- Have experienced major incidents (to validate response capabilities)
Essential questions for references
Service quality:
- How does actual performance compare to what was promised during sales?
- Has service quality remained consistent, improved, or declined over time?
- How responsive is the provider when you have questions or issues?
- Do you feel like a valued partner or just another account?
Technical capabilities:
- How effective is threat detection in your environment?
- What’s the false positive rate you’re experiencing?
- How quickly does the provider typically respond to incidents?
- Has the provider caught threats your internal team or other tools missed?
Business relationship:
- How well does the provider understand your business context?
- How has the provider helped improve your security posture beyond incident response?
- What’s communication like during incidents? After hours?
- How transparent is the provider about their work and your results?
Value delivery:
- Has the provider delivered measurable ROI?
- How much time has the service freed up for your internal team?
- Would you choose this provider again if you were starting over?
- What would you change about the service if you could?
Honest assessment:
- What are the provider’s actual weaknesses?
- What surprised you (positively or negatively) after going live?
- What should I know that won’t come up in vendor presentations?
Beyond official references
Supplement vendor-provided references with:
- Peer network inquiries: Ask your professional network about their experiences
- Online reviews: Check Gartner Peer Insights, G2, TrustRadius for broader feedback
- Industry analyst reports: Review Forrester Wave, Gartner Market Guide assessments
- Conference interactions: Speak with users at industry events
- LinkedIn research: Review what customers post about their providers
The bottom line
Choosing an MDR provider is a high-stakes decision impacting your organization’s security posture, operational efficiency, and strategic capability. The right provider becomes a trusted partner who strengthens your defenses, frees your team to focus on strategic initiatives, and helps you build genuine cyber resilience.
Use this comprehensive framework to evaluate providers systematically:
- Assess the four pillars: speed, clarity, precision, and partnership
- Evaluate against 60+ selection criteria across technology, people, process, and price
- Ask revealing questions beyond predictable RFP responses
- Watch for red flags indicating poor fit or capability gaps
- Conduct thorough reference checks with multiple customer profiles
- Validate critical requirements through demos, pilots, or limited POCs
According to Gartner, successful MDR service providers offer a focus on high-fidelity threat detection, investigation, and mitigative response with meaningful and human-interpretable reporting aligned to business-focused risks. Look for providers who demonstrate these qualities consistently through their technology, people, processes, and customer relationships.
The evaluation process requires investment, but choosing the right partner delivers compounding returns—reducing risk, improving efficiency, and building the security resilience your organization needs to thrive in an increasingly hostile threat landscape.