SOC · 4 MIN READ · BEN NAHORNEY AND MATT JASTRAM · MAR 12, 2025 · TAGS: Vulnerability management
TL;DR
- Starting this month, we’ll be spotlighting a vulnerability we’ve seen used in actual incidents.
- This month’s Patch Tuesday includes six vulnerabilities that are being actively exploited.
- We take a look at an Adobe ColdFusion vulnerability recently used in an attack.
In this month’s Patch Tuesday blog we’re introducing something new. Along with an overview of the most critical, newly patched vulnerabilities from Microsoft, we’re going to begin including coverage that showcases a particular vulnerability our SOC analysts have actually encountered.
Sometimes we’ll look at something seen in the last month; other times it’ll be a trend that we’ve seen over time. And in circumstances involving a vulnerability in widespread use, we can dive into how attackers leverage it.
And what better way to highlight this activity than by sharing real stories surrounding these vulnerabilities’ usage?
Patch Tuesday: March 11, 2025
But before we get into this new monthly feature, let’s talk about Patch Tuesday. This month’s release includes 57 Microsoft fixes, six of which are being actively exploited, leading CISA to add them to their Known Exploited Vulnerabilities (KEV) catalog. We recommend addressing each of these immediately.
- Windows NTFS Remote Code Execution Vulnerability (CVE-2025-24993)
- Windows NTFS Information Disclosure Vulnerability (CVE-2025-24991)
- Windows Fast FAT File System Driver Remote Code Execution Vulnerability (CVE-2025-24985)
These three vulnerabilities can be executed using a similar attack tactic. According to Microsoft, an attacker could exploit the vulnerability if they trick a local user into mounting a specially crafted virtual hard disk (VHD). For CVE-2025-24993 and CVE-2025-24991, this leads to arbitrary code execution, while CVE-2025-24991 allows them to read portions of heap memory. Tricking someone into loading a VHD sounds far-fetched, but we’ve seen it before. Attackers generally disguise the file to look like another file type.
- Microsoft Management Console Security Feature Bypass Vulnerability (CVE-2025-26633): This vulnerability allows an attacker to bypass some security features so their attack gets less scrutiny from the system than it should. To pull it off, they’ll still need to trick a user into running a file or clicking a link on the targeted device (or do it themselves).
- Windows Win32 Kernel Subsystem Elevation of Privilege Vulnerability (CVE-2025-24983): This vulnerability leverages a race condition to gain SYSTEM privileges on the compromised system. This isn’t always easy to do, but Microsoft has evidence that someone has found a way to do it.
- Windows NTFS Information Disclosure Vulnerability (CVE-2025-24984): If an attacker manages to plug a malicious USB drive into a vulnerable system or gets someone else to do so, they can use it to read portions of heap memory from the device, allowing them to steal sensitive data.
Exploit tales: ColdFusion
This month, we’re going to look at vulnerabilities in Adobe ColdFusion. At first glance, this might seem like an obscure choice, as it only makes up a small percentage of the overall web application servers in use today. However, ColdFusion is still in active development and is used across a wide range of industries.
We’ve seen several incidents involving CVE-2023-26360, which was disclosed back in March 2023 and can lead to arbitrary code execution. The vulnerability can be exploited by using a specially crafted HTTP request, meaning that if a vulnerable server is public-facing, it can be easily targeted.
In one incident, our SOC received several alerts about possible exploitation of public-facing ColdFusion servers. It turned out that bad actors had managed to write class files to several servers using the vulnerability. In all, 20 ColdFusion servers were compromised.
Many ColdFusion servers currently in use are running older releases that no longer receive patches, making them easy targets for attackers. In this incident, our analysts noted that the ColdFusion servers were running version 11, which is no longer supported by Adobe. Our analysts suggested updating to the newest version of ColdFusion to mitigate this vulnerability.
This is just one example of a ColdFusion vulnerability that’s been used in attacks, but it’s not the only one. Currently, there are 15 ColdFusion vulnerabilities listed in CISA’s KEV catalog, three of which are known to be used in ransomware campaigns. According to data from GreyNoise Intelligence, there are currently malicious IP addresses actively leveraging two-thirds of these CVEs.
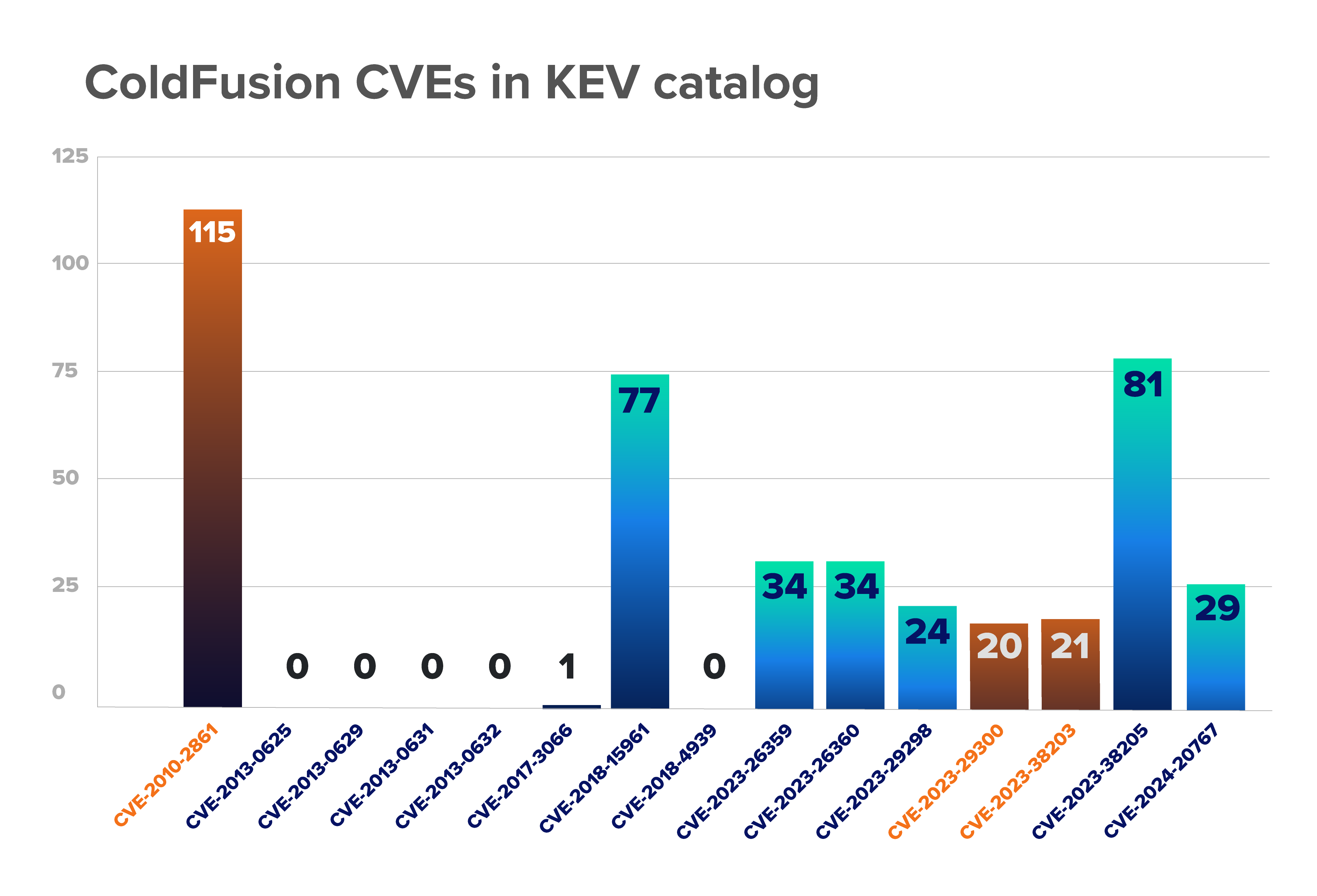
Our SOC has managed other incidents involving ColdFusion. In another recent incident, our SOC analysts were alerted to the presence of malware on two ColdFusion servers within an organization’s environment. It appeared as though the attackers could have uploaded files using an unrestricted file upload vulnerability (CVE-2018-15961). Analysis determined that webshells that had been uploaded to these servers, but had been detected before the attacker could use them to execute malicious commands.
However, while addressing the incident, the organization confirmed that they were running a supported version of ColdFusion and were fully patched, meaning they were not susceptible to exploitation using this vulnerability. Instead, these files were likely uploaded through a web form that lacked strict controls over the file types it allowed.
While it turned out that this vulnerability wasn’t involved in this particular incident, CVE-2018-15961 is frequently used by attackers. Even though it was disclosed close to seven years ago, 77 IP addresses are currently using this exploit to attempt to compromise vulnerable servers.
This highlights an important aspect of vulnerability management—just because a vulnerability is old, doesn’t mean that it’s not in an attacker’s rotation of exploits. The fact is, much of the malicious activity seen at the network perimeter these days is automated. Attackers throw a wide variety of exploits at public-facing systems just to see what will stick—including older vulnerabilities that have a proven history of successful exploitation.
It’s also worth stressing the importance of patching public-facing servers. Given their location on the network perimeter, they’re a regular target of malicious actors. In addition, it’s essential to disable, or at least limit, the use of connect protocols like SMB and RDP on public-facing servers. Doing so may limit an attacker’s ability to connect and carry out attacks.
That wraps up this month. If you have any questions about the vulnerabilities talked about here (or others on the Patch Tuesday list)—or if you’re interested in learning how Expel Vulnerability Prioritization can give you context for your own environment—get in touch with us.






