Threat intel · 4 MIN READ · BEN NAHORNEY, MATT JASTRAM AND AARON WALTON · AUG 13, 2025 · TAGS: vulnerability prioritization
TL;DR
- Microsoft released 111 new CVEs for Patch Tuesday
- You can use this blog as a guide for determining which vulnerabilities to patch ASAP
- We’re talking more about SharePoint vulnerabilities in light of the emergency patch last month
Welcome to the August Patch Tuesday blog! If you missed the news, Microsoft released an emergency patch last month for the Microsoft SharePoint Server Remote Code Execution Vulnerability (CVE-2025-53770). We published a blog on this vulnerability at the time, so this month we’ll take a wider look at these SharePoint vulnerabilities.
But first, we have a whole bushel of new vulnerabilities to discuss from this month’s Patch Tuesday harvest. Let’s jump in!
Patch Tuesday: August 12, 2025
This month, Microsoft disclosed 111 CVEs, 13 of which have been marked as critical. This release includes one zero-day vulnerability, originally disclosed back in May, and 35 remote code execution (RCE) vulnerabilities.
We took a look through the list of vulnerabilities published this month and have determined that the following four vulnerabilities should be addressed first:
- Windows Kerberos Elevation of Privilege Vulnerability (CVE-2025-53779): This zero-day vulnerability in Windows Server 2025 was originally disclosed in May. A successful attack using this vulnerability could allow a bad actor to take over any account in Active Directory. To carry out this attack, a bad actor would need access to attributes associated with the delegated Managed Service Account (dMSA) in Windows Server 2025. By modifying these attributes, they could elevate the permissions of any user they choose. This means they could take an arbitrary account and grant it Domain Administrator privileges.
- Microsoft Exchange Server Hybrid Deployment Elevation of Privilege Vulnerability (CVE-2025-53786): This vulnerability could provide attackers who have compromised an on-premises Exchange Server with an opportunity to pivot to an organization’s cloud environment. This could be useful for an attacker who’s attempting to move laterally into the cloud.
- Critical Windows NTLM Elevation of Privilege Vulnerability (CVE-2025-53778): Windows New Technology LAN Manager (NTLM) is a deprecated authentication protocol that can be used to provide authentication to users on Windows networks. According to Microsoft, an attacker exploiting this vulnerability could gain SYSTEM privileges on the targeted system. This would allow them to take control of the machine. We recommend verifying whether or not NTLM is still in use after patching.
- Critical Microsoft Message Queuing (MSMQ) Remote Code Execution Vulnerability (CVE-2025-50177): This use-after-free vulnerability takes advantage of a flaw in the Windows Message Queue where the application continues to access memory after it has officially released it. An attacker could send specially crafted MSMQ packets over the network to a MSMQ server. If the attack is successful, the attacker could run arbitrary code on the targeted system.
Exploit Tales: SharePoint targeting
July’s critical SharePoint vulnerability—CVE-2025-53700—caught everyone off-guard, but wasn’t ever alone as it comes to vulnerabilities in SharePoint targeted by attackers. Last patch Tuesday, Microsoft patched critical vulnerabilities they were aware of (CVE-2025-49704 and CVE-2025-49706), but it turned out that adversaries were also privy to the vulnerabilities, and also aware of additional related vulnerabilities (CVE-2025-53700 and CVE-2025-53701), allowing them to bypass the patch and requiring an emergency patch from Microsoft.
Here at Expel, we saw enough activity early on and published a blog covering how it works and how to defend against it. We encourage reviewing the blog for more details about that vulnerability, as this blog will focus more broadly on SharePoint exploitation.
SharePoint is a prime target for attackers. Due to its placement on the network perimeter, it can provide a foothold into an organization’s network. And CVE-2025-53770 isn’t the only vulnerability that has seen attacker activity. In fact, there are currently seven in the Known Exploited Vulnerability (KEV) catalog. And according to data from GreyNoise Intelligence, this new vulnerability isn’t even the most common Sharepoint vulnerability currently leveraged by malicious IP addresses.
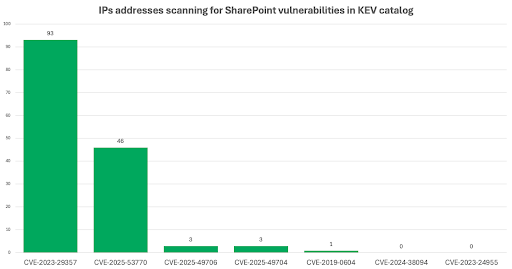
The most commonly seen exploit comes from 2023, when a researcher discovered that two SharePoint vulnerabilities (CVE-2023-29357 and CVE-2023-24955) could be chained together by an attacker to gain RCE during a Pwn2Own competition. While the code released following the contest didn’t provide the full code to complete the chain, CVE-2023-29357 was added to the KEV catalog shortly thereafter. However, it wasn’t until March 2024 that the second vulnerability was added to the catalog, indicating it was being used in attacks.
Interestingly, the SharePoint vulnerabilities discovered earlier this year were also disclosed at a Pwn2Own event. These SharePoint CVEs are also in the KEV catalog—CVE-2025-49704 and CVE-2025-49706. However, CVE-2025-53770 is considered a variant of the vulnerability outlined in CVE-2025-49704, just as the security bypass vulnerability CVE-2025-53771 is a variant of CVE-2025-49706.
Another RCE vulnerability (CVE-2024-38094), disclosed in July 2024, was added to the KEV catalog in November 2024. Reports soon surfaced that the vulnerability was being used to gain access to networks, after which the attackers moved laterally and compromised the domain.
Fortunately, when it comes to RCE attacks like this, they still need to follow well-known execution paths, which present plenty of opportunities to detect and respond, provided that processes on the server are being monitored. For instance, we were made aware of many of the incidents involving this latest SharePoint vulnerability thanks to EDR tools monitoring for behaviors consistent with web exploitation. Web exploitation normally results in expected processes spawning from the service running the website: most often a terminal, script interpreter, or PowerShell.
The criticality of these vulnerabilities makes active monitoring a necessity. We recommend tools like EDR agents installed on both servers and user endpoints. These can alert on or even mitigate exploitation of even the newest vulnerabilities. However, they also require monitoring and action. Once exploitation is observed, it’s important to investigate and identify other means to secure the device (such as any patches that may be required).
That’s a wrap for this month. If you have any questions about the vulnerabilities talked about here (or others on the Patch Tuesday list) get in touch with us.






