Data & research · 5 MIN READ · MATT JASTRAM · AUG 20, 2024 · TAGS: Get technical / vulnerability prioritization
TL;DR
- What our MDR data is showing us about common vulnerabilities and exposures (CVE) trends this year
- How we use the Exploit Prediction Scoring System (EPSS) scores and the Cybersecurity & Infrastructure Security Agency (CISA) catalog to inform our remediation strategy
- Insights from our data so far (and what’s coming next)
Our Expel Managed Detection and Response™ (MDR) customers continue to be inundated by threat actors attempting—and sometimes succeeding—in leveraging vulnerability exploits. Since the start of the year, we’ve identified 42 common vulnerabilities and exposures (CVEs) associated with MDR incidents, which is on pace to surpass the 2023 exploitation numbers.
But an increase in CVEs isn’t as bad as it can look at a glance. Many CVEs have similar functions, and the increase in exploitation attempts is beneficial to our SOC after the incident is resolved. It gives us more data to use to create defensive strategies, and makes our approaches more nuanced (and more successful). Monitoring CVE trends within our SOC also gives us a historic view to help predict upcoming trends, which is something we like to do around here.
This blog provides an overview of the data we use to build our remediation plans, offers resources you can use to track CVEs, and highlights the current trends we’re seeing (and what they mean). It’s also the first in our latest MDR insights series, where we’ll take a deeper look at issues we’ve highlighted in our latest quarterly threat report (QTR) blog series. Let’s dive in.
Common CVEs our SOC has seen so far in 2024
Expel’s Vulnerability Prioritization™ reviews all MDR customer incidents to identify vulnerabilities attackers use. So far this year, we’ve reviewed over 1,600 incidents and have identified a CVE for 2.6% of those incidents. Of the 42 CVEs our SOC has seen in 2024, the table below highlights the frequency of the specific vulnerability targeted, what it is, and how it’s resolved:
| CVEs | Incident frequency | Impacted product(s) | Vulnerability summary | Recommended solution |
|---|---|---|---|---|
| CVE-2023-23397 | +5 | Microsoft Outlook elevation of privilege (EoP) | We see attackers gain and elevate privilege by crafting emails directing victims to attacker-designated untrusted hosts, so the attacker can relay to another service and authenticate as the victim. | Install applicable security updates that resolve the risk. For example, Microsoft provided multiple security updates that addressed this issue. |
| CVE-2022-41082 | +3 | Microsoft Exchange remote code execution (RCE) vulnerability | Externally-facing servers are hot targets for this vulnerability. When the attackers access Microsoft Exchange PowerShell, an RCE is leveraged. | Install applicable security updates. See Microsoft’s customer guidance for this vulnerability. |
| CVE-2021-34523 | +2 | Ability to write an arbitrary file to achieve RCE on multiple Microsoft Exchange servers | This exploits a vulnerability on multiple Microsoft Exchange Servers (2013, 2016 & 2019), that allows an attacker to bypass the authentication (CVE-2021-31207) by
impersonating an arbitrary user (CVE-2021-34523). Then bad actors write an arbitrary file (CVE-2021-34473) to achieve the RCE. |
Install applicable security updates. See Microsoft’s customer guidance for this vulnerability. |
| CVE-2021-44228 | +2 | Apache Log4j2 issue where JNDI features don’t protect against RCE | Multiple ransomware groups have leveraged this vulnerability. The affected Apache Log4j2 JNDI features don’t protect against attacker-controlled JNDI-related endpoints, allowing RCE. | There’s a variety of 21 vendor-specific product patches available. We recommend verifying if you have this vulnerability in your environment. |
| CVE-2022-41040 | +2 | Microsoft Exchange Server allows for server-side request forgery | The privileges acquired by the attacker allow them to run PowerShell in the context of the system. | Install applicable security updates. See Microsoft’s customer guidance for this vulnerability. Also, here’s their vulnerability-specific security update. |
| CVE-2024-3400 | +2 | Palo Alto Networks operating system (PAN-OS) command injection vulnerability | This command injection vulnerability allows for arbitrary file creation in the GlobalProtect feature of specific versions of Palo Alto Networks PAN-OS software. | Palo Alto provided a patch for multiple versions. |
How Expel uses the Exploit Prediction Scoring System (EPSS)
Expel continues to see the industry rely more on the Exploit Prediction Scoring System (EPSS). The score is based on vulnerability exploitation attempts spotted from multiple sources. Recently, vulnerability scanning technologies have adopted EPSS scores in their user interfaces because it enhances exploit evidence and helps industry SMEs prioritize risk.
Expel Vulnerability Prioritization ™ monitors percentage increases in EPSS scores to accurately inform our customers. Here are the top 10 fluctuations from last quarter:
| Increase date | CVE | Old EPSS score (April) | New EPSS score (June) | EPSS total increase | |
|---|---|---|---|---|---|
| 1 | 2024-06-20 | CVE-2024-29973 | 0.09% | 93.66% | +93.57 |
| 2 | 2024-06-01 | CVE-2024-24919 | 1.85% | 94.50% | +92.65 |
| 3 | 2024-04-21 | CVE-2024-3400 | 2.22% | 93.18% | +90.96 |
| 4 | 2024-06-28 | CVE-2023-52251 | 2.65% | 93.57% | +90.92 |
| 5 | 2024-05-24 | CVE-2023-4542 | 0.07% | 90.98% | +90.91 |
| 6 | 2024-05-24 | CVE-2024-0195 | 0.11% | 89.85% | +89.74 |
| 7 | 2024-05-06 | CVE-2024-4040 | 1.60% | 90.74% | +89.14 |
| 8 | 2024-06-15 | CVE-2024-4358 | 5.03% | 93.84% | +88.81 |
| 9 | 2024-04-24 | CVE-2023-50386 | 0.13% | 87.24% | +87.11 |
| 10 | 2024-06-29 | CVE-2019-7193 | 12.43% | 95.64% | +83.22 |
Expel recommends evaluating your infrastructure for these vulnerabilities, and taking quick action to remediate your infrastructure. If the exploitation risk rapidly increases, then so should your remediation action efforts!
Expel’s CVE remediation strategy, based on the CISA catalog
The Cybersecurity & Infrastructure Security Agency (CISA) remains the authority on exploited vulnerabilities. The CISA Known Exploited Vulnerability Catalog currently contains 1,139 CVEs. CISA frequently adds to their catalog, including CVE descriptions, known use in ransomware, actions to take, date added, and a suggested due date.
Balancing vulnerability remediation with CISA’s catalog addition continues to overwhelm our customer’s responsible remediation parties. Attempting to keep up with every new vulnerability burns up resources, but Expel can help with that. We programmatically evaluate each CISA catalog update to weigh risk and identify and prioritize remediation. We approach risk prioritization by starting with the highest risk and strategically chipping away by remediating with CISA’s recommendations. We’re also sure to consider asset accessibility, EPSS scoring, GitHub repos, and other reports of threat actor behavior. Here’s how Expel categorically recommends remediation based on the CISA database:
| Category | Total | Critical | High | Medium | Low |
|---|---|---|---|---|---|
| CISA CVE categorization | 1,139 | 2 | 494 | 107 | *537 |
| Ransomware use in CVEs | 228 | 1 | 107 | 15 | 105 |
| Ransomware use percentage (of total CVEs) | 20% | 50% | 22% | 14% | 20% |
| Expel recommendation | Fix within one week | Fix within one to two weeks | Fix within the next patching cycle | Continue to monitor exploit risk |
While there are 105 ransomware CVEs categorized as “Low” risk, that doesn’t mean you should just ignore them. The likelihood of exploitation for these CVEs is lower than that of those ranked with higher risk values. But, it’s important to keep watching the CVE for any changes in the risk level, or if a fix is released.
The “Low” categorization is determined by multiple factors, including the exploit code maturity, EPSS score, and repositories with the exploit code available.
Trends in CVEs based on true positive incidents in our SOC
With Expel’s Managed Detection and Response™ (MDR), we see multiple vendor alerts associated with true positive incidents. These alerts can also show us the loudest CVE signals from true positive incidents, which is helpful as we continue to monitor these trends into the next quarter. As we continue to track CVEs tied to true positive incidents, we’ll be able to account for trends and why we think they’re changing.
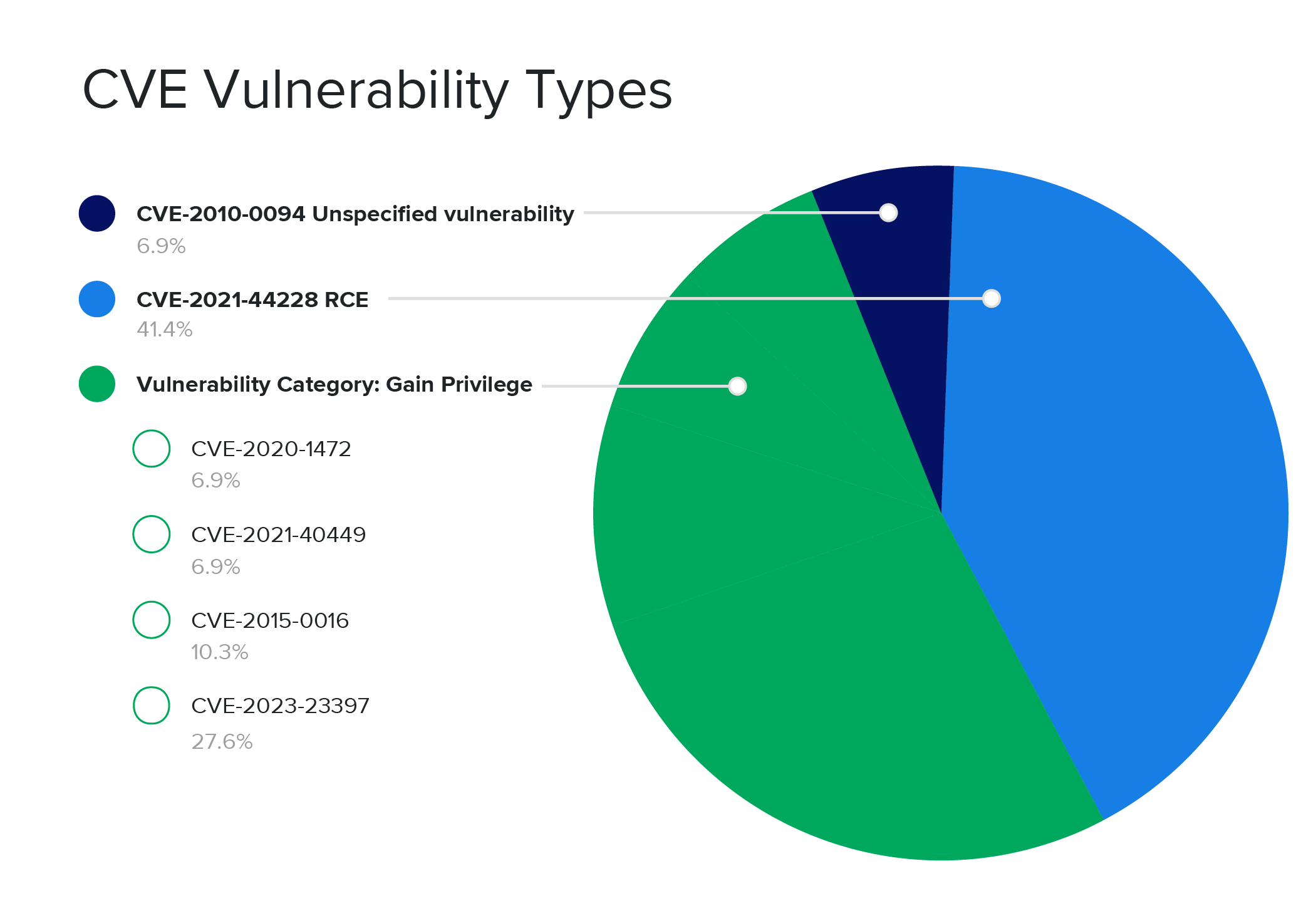
In the table below, you’ll see a breakdown of the CVE-related alerts we saw tied to a true positive incident last quarter:
| CVE | Frequency | Tool alert descriptions |
|---|---|---|
| CVE-2021-44228 | 12 | Log4j search |
| CVE-2023-23397 | 8 | Possible target of NTLM credential theft |
| CVE-2015-0016 | 3 | Meterpreter post-exploitation tool |
| CVE-2021-40449 | 2 | [Malware] CallBckHel hacktool was prevented |
| CVE-2020-1472 | 2 | Netlogon privilege elevation attempt |
| CVE-2010-0094 | 2 | ‘Metasploit’ was prevented |
What we’ve learned so far: focusing on specific vulnerabilities is beneficial
Tracking the true positive incident vendor signals has already made one trend clear: there are two main attack approaches for CVEs. The biggest vulnerability types bad actors target are to gain privileges and establish RCE. Our SOC data makes it clear that while there’s a variety of ways to attempt to gain privileges, the end goal of bad actors is still the same.
If your vulnerability remediation efforts focus on these types of vulnerabilities, you’re using a security strategy that will help proactively reduce risk. And that’s one of the best ways to keep your environment resilient.
Alerting to incidents based on CVE type can also reduce alert fatigue.
Alerting to incidents based on CVE type can also reduce alert fatigue. Cybersecurity tools are noisy by nature, and focusing alerts to capture signals related to CVEs specific to gaining privileges and RCE can help turn down the noise. 52% of the true positive incidents we saw last quarter were for CVEs looking to gain privilege, and 41% were for RCE. This means that focusing on alerting to and remediating these specific types of CVEs can have a positive impact on proactive security and alert fatigue.
Stay tuned for more on CVE trends in our SOC as Expel continues to evaluate cybersecurity tool signals associated with vulnerability types, and what that could mean for you.