Product · 3 MIN READ · MATT PETERS AND PETER SILBERMAN · DEC 3, 2019 · TAGS: Get technical / Guidance / tech stack
Amazon Web Services (AWS) has rolled out some really nifty security capabilities over the last couple of years. Amazon Detective is AWS’ latest innovation.
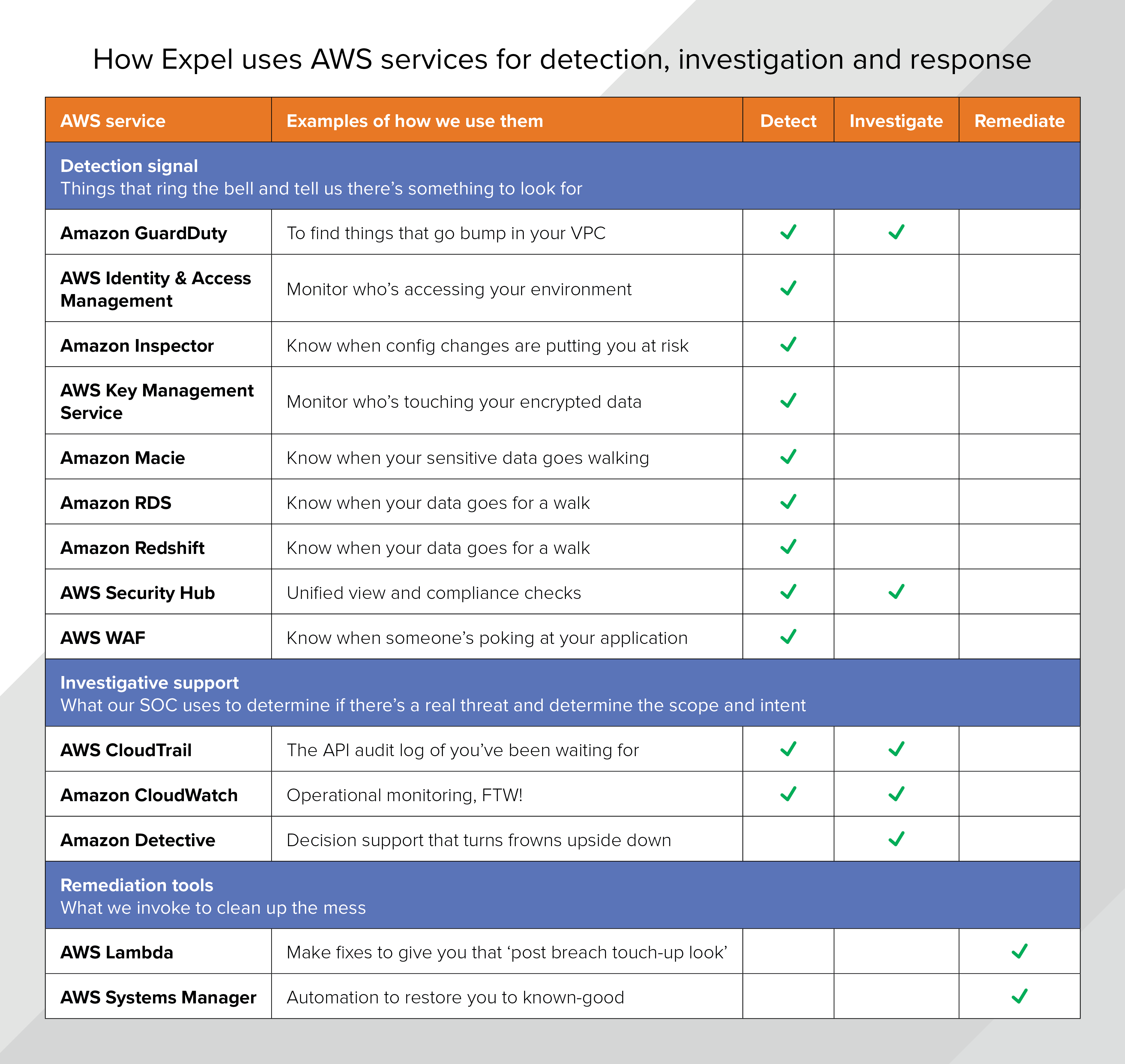
If you run workloads on AWS, then you’re probably already familiar with some of the other AWS-native security tools like Amazon GuardDuty, AWS Security Hub and Amazon Macie.
So where does Amazon Detective fit into this puzzle?
What is Amazon Detective?
Think of Amazon Detective as investigative support for AWS GuardDuty alerts. AWS announced the public preview program for Amazon Detective at re:Invent 2019 and Expel is one of the first managed detection and response (MDR) providers to support it. We’re thrilled to be an early service partner for Amazon Detective!
In practice, Amazon Detective makes it easier for AWS customers and their MDR providers to analyze, investigate and quickly identify the root cause of security findings or suspicious activities. The service automatically extracts, distills and organizes data from VPC Flow Logs, AWS CloudTrail and Amazon GuardDuty, and creates an interactive view with contextual information that summarizes resource behaviors and interactions observed across your AWS environment.
Amazon Detective can help speed up investigations for supported GuardDuty findings. For example, if you receive a GuardDuty finding of suspicious VPC flow activity, Amazon Detective will now present you with relevant information about the IPs involved in that GuardDuty finding. This speeds up the time to triage an alert (and likely cuts response time too).
Amazon Detective might also prompt you (or your security analysts) with questions you should be thinking about answering. This fits nicely with how Expel thinks about the analyst mindset, and how we train our analysts to answer questions instead of following specific pre-set run books.
Where does Amazon Detective fit in your AWS security strategy?
If you’re new to AWS and are looking for a simple this-tool-does-that primer, then here’s a good place to start.
At Expel, many of our customers run workloads on AWS and our analysts work with alerts from these environments on a regular basis to investigate suspicious activity. We’ve published several how-to’s for popular AWS security tools, along with some tutorials on fixing common cloud security issues.
Be sure to check out:
- Making sense of Amazon GuardDuty alerts
- Following the CloudTrail: Generating strong AWS security signals with Sumo Logic
- How to find Amazon S3 bucket misconfigurations and fix them ASAP
When it comes to securing the cloud, Amazon provides a panoply of solutions which can be a bit dazzling (and different from what you’d find in a traditional on-prem security stack). We’ve found that by mapping these to a set of jobs that our analysts do, it provides a helpful framework for thinking about them. Broadly, we bucket the AWS offerings into three categories.
Why we’re excited about Amazon Detective
Amazon Detective is helpful addition to AWS’ suite of security tools. At Expel, we believe that quality forensic investigations require context and decision support, and that’s exactly what Amazon Detective provides.
A security alert alone doesn’t tell you much, but the context surrounding it is essential to figuring out whether you’ve got a false positive or a legitimate issue on your hands. The right historical details and the right behavior analytics are what turns any old alert into the lead that cracks the case. For example, if it’s 2am and you’re looking at an anomalous login, the context around that user’s login is helpful — is this a real problem, or is Pat on sabbatical in Spain?
Put your cloud security skills to the test
Whether or not Amazon Detective has a place in your security strategy right now, it’s easy to test out the AWS security tools you’re already using in staged environments.
Once you’re feeling confident using the AWS-native security tools, put your team’s detection skills to the test by creating a threat emulation exercise for AWS. This is something we do often at Expel. Simulating realistic attacks in cloud environments helps our analysts build muscle memory and prepares them to act quickly and correctly when something bad happens.
Like this idea but not sure how to get started with creating your own? We’ve got an entire post that walks you through the process of creating a cloud-based threat emulation exercise. We even threw in a sample scenario for you, complete with instructions on how to simulate the attack in your AWS environment. Enjoy!