Threat intel · 10 MIN READ · AARON WALTON · AUG 22, 2025
TL;DR
- In this blog, we’ll discuss our findings from investigating a specific trojan malware and how it gets onto a system.
- You can find the first tidbits of information we shared about this on LinkedIn, X, or Reddit
- We’ll continue to expand this blog as we continue our investigation
We’ve recently witnessed new activity in the realm of potentially unwanted programs (PUPs). While PUPs have traditionally displayed advertisements or collected personal information, we’re seeing activity where PUPs are dropping highly suspicious files, executing unexpected commands, and turning hosts into residential proxies. In our opinion, this activity pushes the line as to what should be considered PUP.
But as we began to dig deeper, we’ve uncovered several interesting aspects leading us to believe that the scope is larger and more complex than it initially seemed.
First sighting
Finding a scheduled task (more details below) was our initial lead. An alert triggered when a Windows service attempted to run code using Microsoft HTML Application Host (MSHTA), which Windows uses to run HTML files that can contain code such as JavaScript.
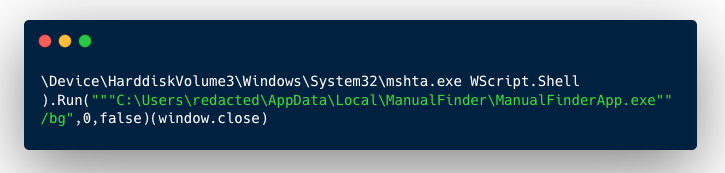
The script is configured to run “ManualFinderApp.exe” in the background (“/bg”). Wscript is also set to run hidden (using the 0 argument, and “false”, meaning the script isn’t supposed to wait once it’s been triggered). The Wscript window is also set to close immediately (window.close).
So what’s ManualFinder? If you run it in a sandbox on its own, it appears to be an app that helps you find manuals—just as its name suggests—and it actually does a pretty good job.
But is that all it does?
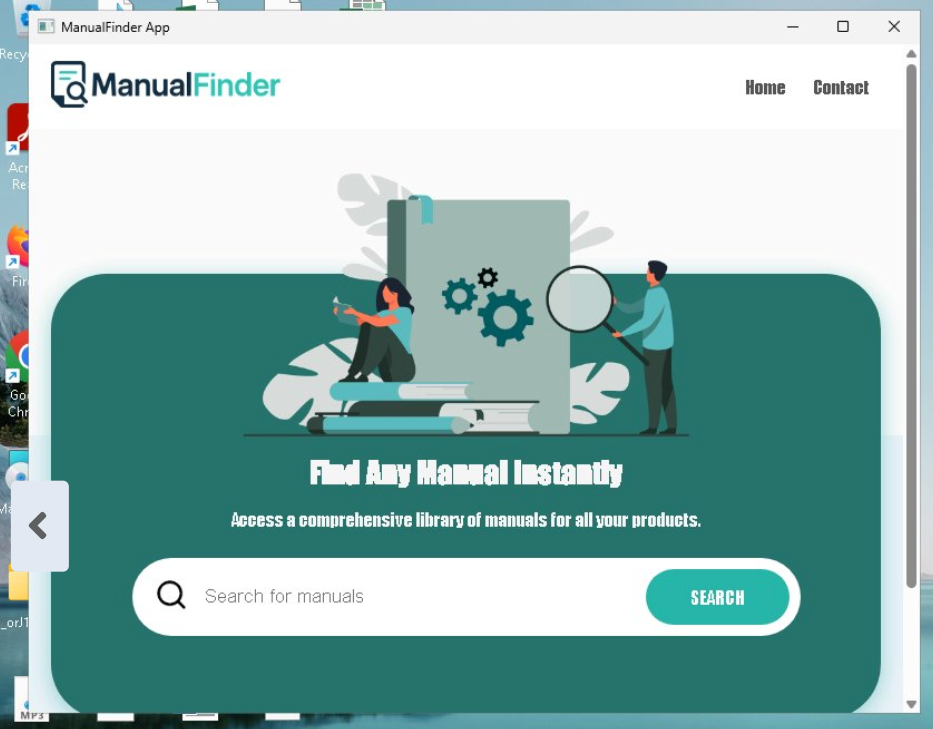
The problem is, the manual search capability appears to just be a decoy, meant to distract from the program’s actual malicious behavior.
In the last year, the infosec community has started seeing an increase in convincing decoy apps. Karsten Hahn (with G-Data) talked about some recent examples, such as JustAskJacky (a semi-reliable desktop assistant) and RecipeLister (a recipe app that can store hidden information in recipes using invisible characters). ManualFinder is another example of a decoy app for malware.
The source
Whenever we’re investigating malware at Expel, we want to understand where the malware came from. In this instance, logs show ManualFinder.msi written to the host just before it was executed. The file was downloaded by a scheduled task, which ran a JavaScript file from the user’s temporary directory. The file was written to the host and immediately executed with this command:
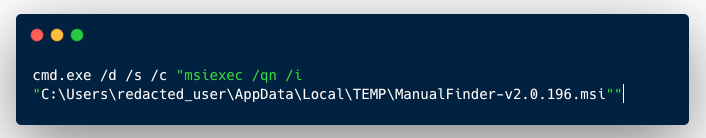
In this command, cmd is being instructed with the following command line arguments:
- /d – disable autorun (keeps commands that run by default from running)
- /s – changes the settings for how quotes in the command will be handled
- /c – executes the command following it; namely, executing MsiExec with the quiet settings (/q) with no UI (/n) and set to install (/i)
When looking at the EDR logs, we find that the parent process is node.exe executing the JS file from the user’s temporary directory.
EDR log:
Process: C:\Windows\System32\cmd.exe
Process Command Line: cmd.exe /d /s /c “msiexec /qn /i “C:\Users\redacted_user\AppData\Local\TEMP\ManualFinder-v2.0.196.msi””
PID: 23988
Integrity Level: Medium
User LoginID:
Process SHA256: 5b5c99020325d9cc02053ac31c74e0dabf1c5339f8d0465e96b0afd91ade3c3f
Parent Process: c:\users\redacted_user\appdata\local\programs\node\node.exe
Parent Command Line: “node.exe” “C:\Users\redacted_user\AppData\Local\TEMP\[redacted guid]of.js”
PPID: 13540
Parent SHA256: 8468f81ef779568e6c9f03f582ac90ce4d68364f8a01839457c0b05b8cdf1bef
Parent Integrity: Medium
Parent Created: 2025-08-18 20:28:03.9132752 +0000 UTC
Parent User: redacted_org\redacted_user
Parent User LoginID: 2120839
When reviewing the origin of the node.exe and js file, we found it executes from a scheduled task: the parent process was from SvcHost running with the commandline “-k netsvcs -p -s Schedule” as is standard with schedule tasks.
EDR log:
Process: C:\Windows\System32\cmd.exe
Process Command Line: “cmd.exe” /c start “” /min “C:\Users\redacted_user\AppData\Local\Programs\node\node.exe” “C:\Users\redacted_user\AppData\Local\TEMP\[redacted guid]or.js”
PID: 9340
Integrity Level: Medium
User LoginID:
Process SHA256: 5b5c99020325d9cc02053ac31c74e0dabf1c5339f8d0465e96b0afd91ade3c3f
Parent Process: c:\windows\system32\svchost.exe
Parent Command Line: svchost.exe -k netsvcs -p -s Schedule
PPID: 3760
Parent SHA256: 949bfb5b4c7d58d92f3f9c5f8ec7ca4ceaffd10ec5f0020f0a987c472d61c54b
Parent Integrity: System
Parent Created: 2025-08-18 11:24:10.7387179 +0000 UTC
Parent User: nt authority\system
Parent User LoginID: 0
Reviewing EDR logs indicated the scheduled task had executed on a schedule for more than a month. At the time of the detection, we observed the JavaScript reached out to the domain mka3e8[.]com, which had previously been associated with OneStart Browser. We were unable to confirm via EDR that the scheduled task was created by OneStart, but we observed OneStart installed on the host and received feedback from others in the community that OneStart was a common denominator in terms of software installed on impacted hosts.
This conclusion comes from the network connection to mka3e8[.]com, which was seen on the system and reported by the community, as seen in the comments on the VirusTotal entry. The Relations page on VirusTotal also shows more than 70 JavaScript files have been uploaded to VirusTotal that reach out to this domain.
Investigating the “apps”
When we looked into the “apps” themselves, their websites were anomalous. The ManualFinder app itself reaches out to the website “ManualFinder.app”. Investigating the webpage shows a site that looks nice, and has consistent branding with the ManualFinder app. However, it’s anomalous in that when we access the website, we could not find a way to download the app.
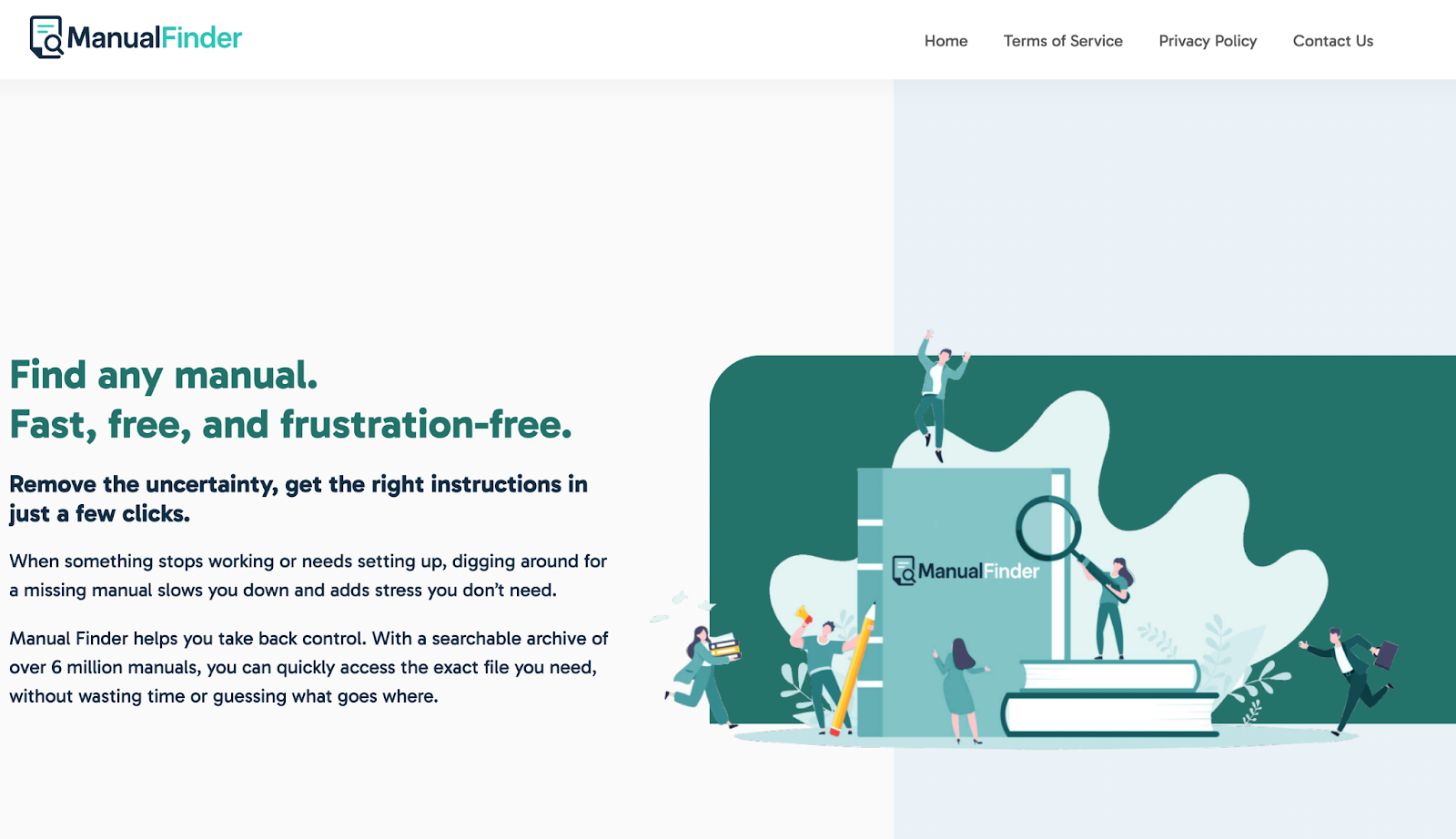
The terms of service on the site don’t help either. It only mentions “ManualFinder Inc”, which doesn’t seem to be mentioned anywhere outside of their website. We also couldn’t learn anything else about this supposed company from the “Contact Us” page, because no information is listed.
Who exactly made this software?
We also reviewed the executable and found a code-signing certificate was used to sign the software. In this case, the code-signing certificate is signed by “GLINT SOFTWARE SDN. BHD.” Glint Software has a website at glintsoftware[.]com, and its domain was registered last year (2024-09-05T09:36:19Z), similar to “ManualFinder.app”.
GlintSoftware’s website is similar to ManualFinder. There’s no information about the company or their products on the website. From the code-signing certificate itself, we learn that Glint Software is a business registered in Skudai, Johor, Malaysia, with the registration number 202401011747, but not much more was easily found regarding the business.
Using VirusTotal, we identified other files with the same code-signing signature using the query “signature:’GLINT SOFTWARE SDN. BHD.’”. At the time of this blog publication, the query returns nine other files, including “PDFEditor”. Running PDFEditor in a sandbox shows it installs a program called “Fast PDF Pro” which is connected to the website “fastpdf[.]pro”, and during the time of analysis, we couldn’t find a way to download the software from the website itself.
We observe that “PDF Editor” and “AppSuite-PDF” use many different code-signing certificates. For most software, we expect a match between the metadata of the file, the code-signing certificate, and legal information about the application itself; however, with these apps, we don’t observe this consistency. The use of multiple code-signing certificates and lack of internet presence for these companies helps re-inforce our conclusion that they’re inauthentic.
AppSuite-PDF has also been observed using the certificate “ECHO INFINI SDN. BHD.” for another company located in the same city in Malaysia, and “Summit Nexus Holdings LLC”, a company registered in Sheriden, Wyoming that uses an address known by Sheridan locals as regularly being abused in scams.
OneStart has a similar sketchy use of code-signing certificates. In 2023 and 2024, they used a code-signing certificate for “Apollo Technologies Inc”, issued to a company in Panama, then a certificate issued to “Caerus Media LLC”, a US-based company, and then finally a code-signing certificate for “OneStart Technologies LLC” for the US.
The certificate signing process is meant to help consumers know who the software provider is. In this case, the pattern of usage doesn’t point toward legitimate usage.
Getting it in the hands of victims
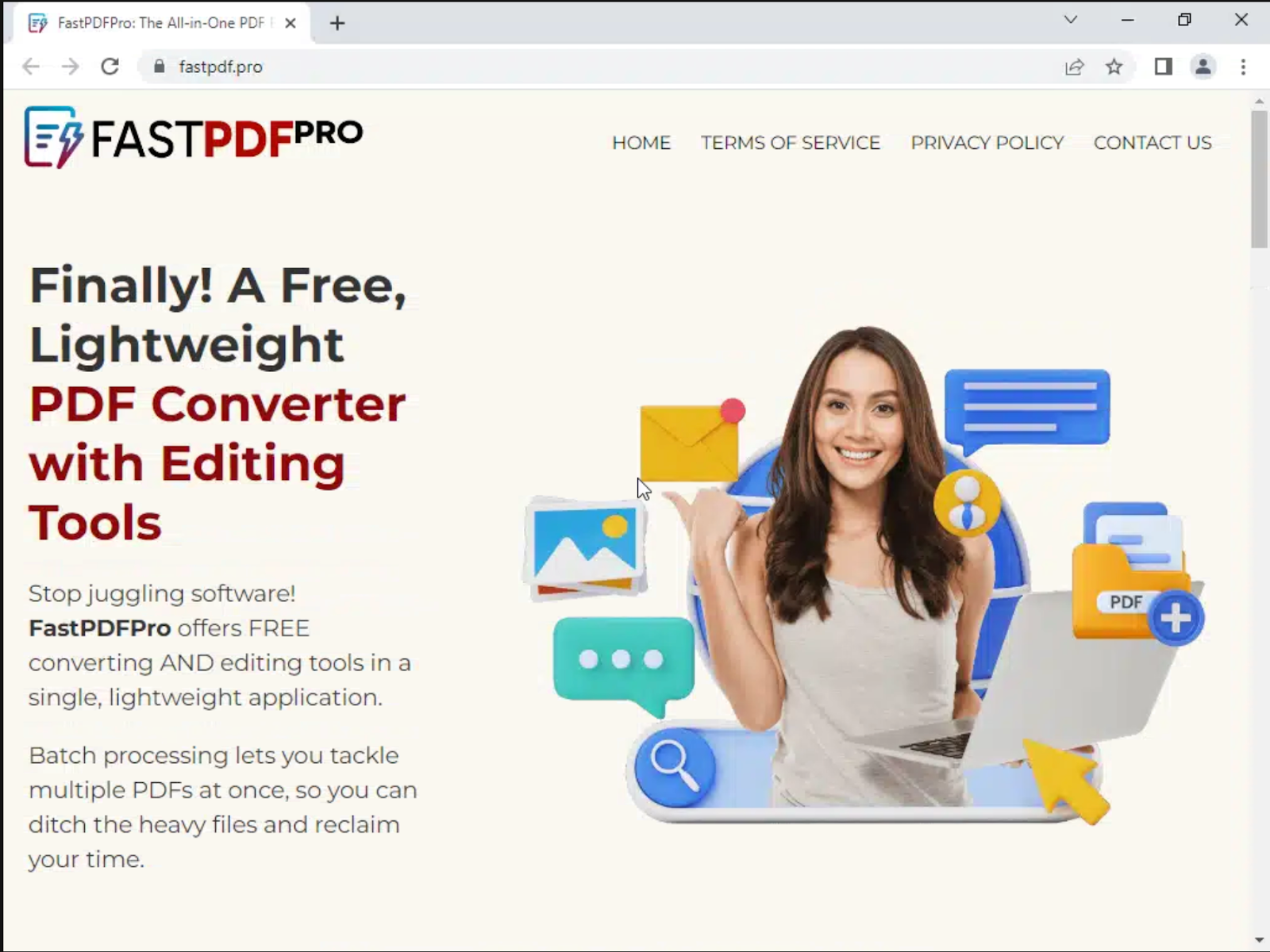
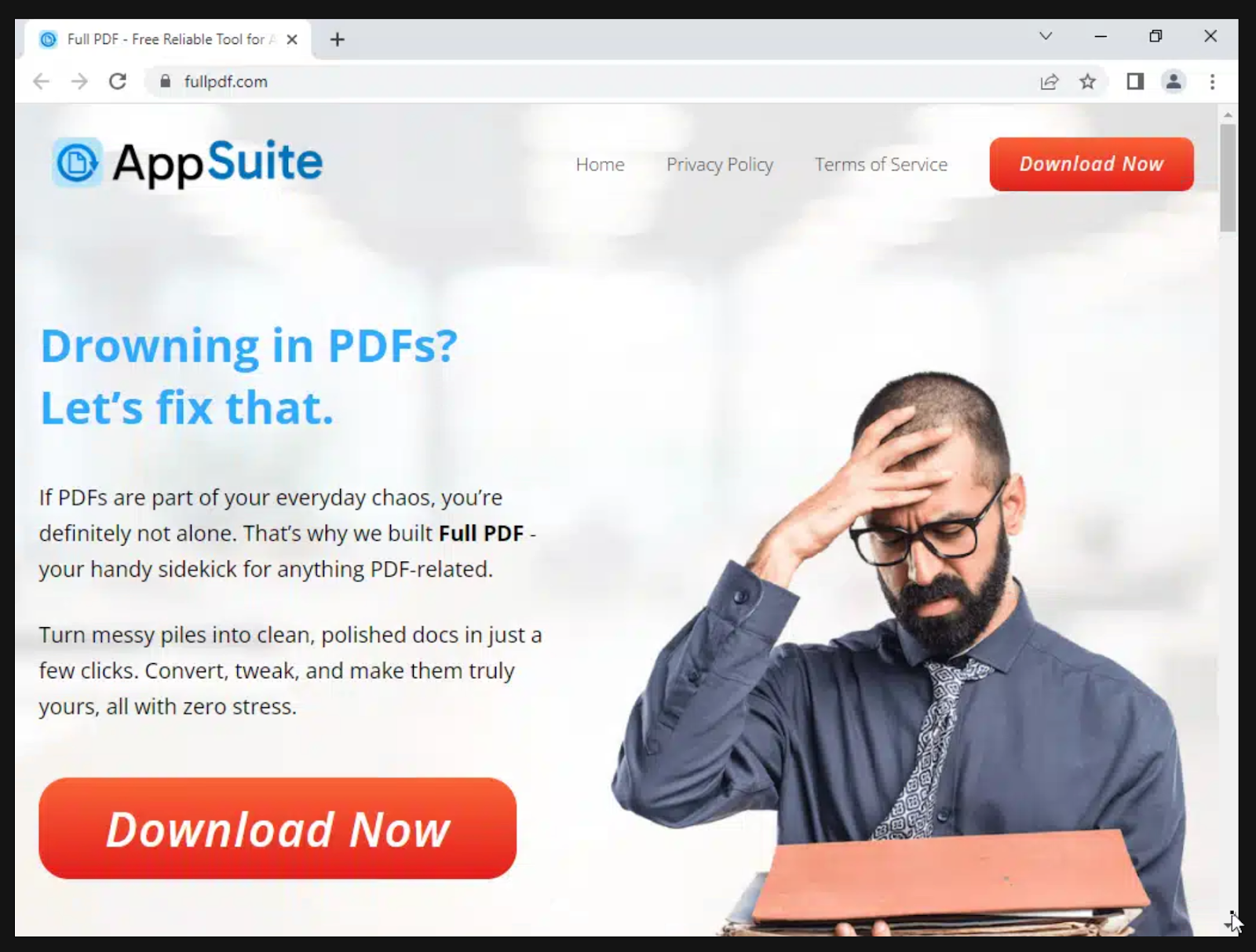
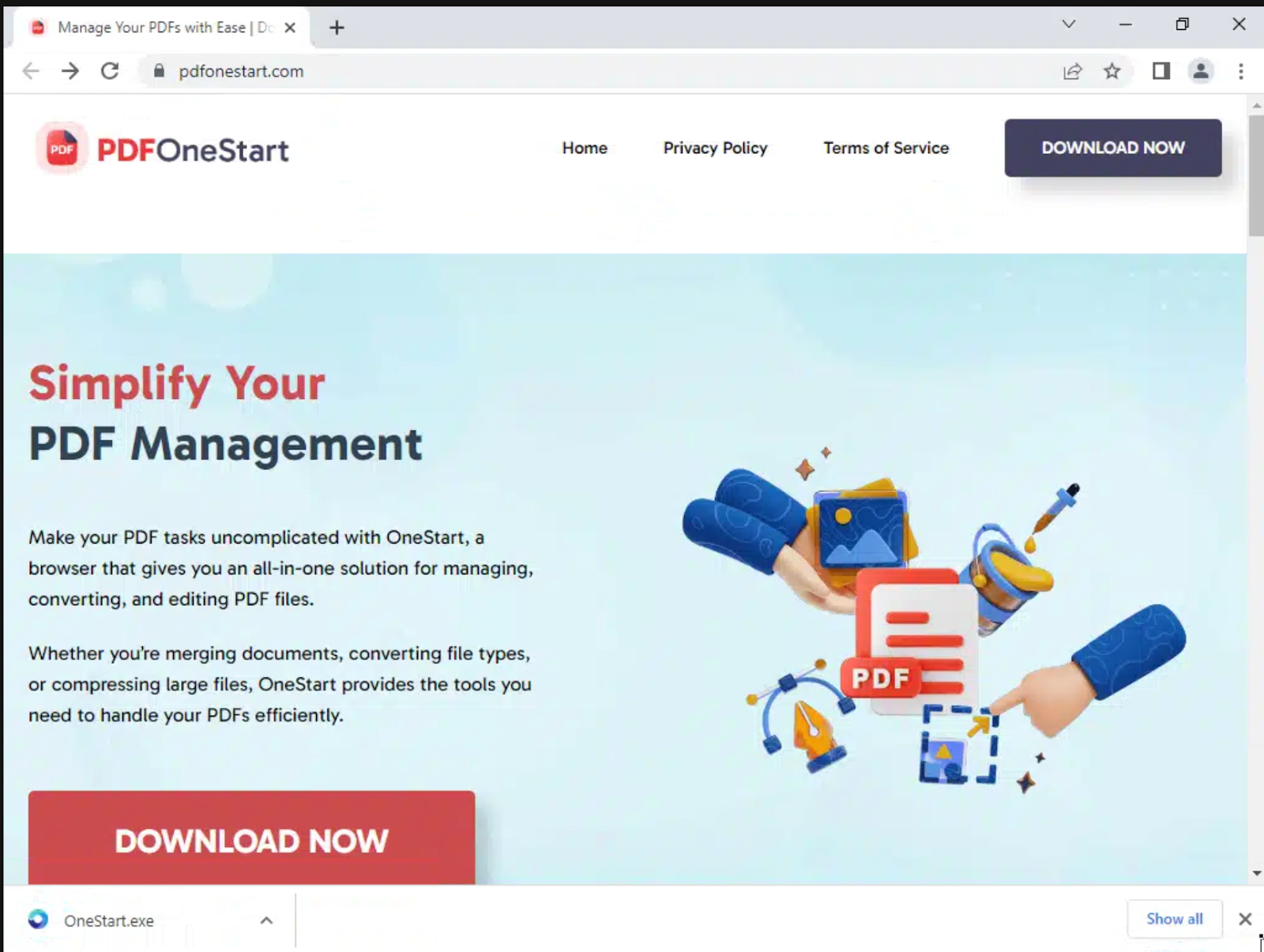
The initial downloads for OneStart, AppSuite-PDF, and PDF Editor are being distributed by a large ad campaign advertising PDFs and PDF editors. These ads direct users to one of many websites offering downloads of AppSuite-PDF, PDF Editor, and OneStart, as shown below. (We reported 44 domains to the domain registrar.)
The risk of “free”
To clarify, OneStart can download AppSuite-PDF. AppSuite-PDF normally downloads PDF Editor. OneStart and PDF Editor can download Manual Finder. We’re working to fully understand the threats of the individual software, and will include analysis of these in a follow-up blog. However, the following are some of our initial findings.
We found that in some cases, running a copy of “PDF Editor” on its own results in a message asking for the user’s consent to use their device as a residential proxy in return for using the free PDF Editing tool.
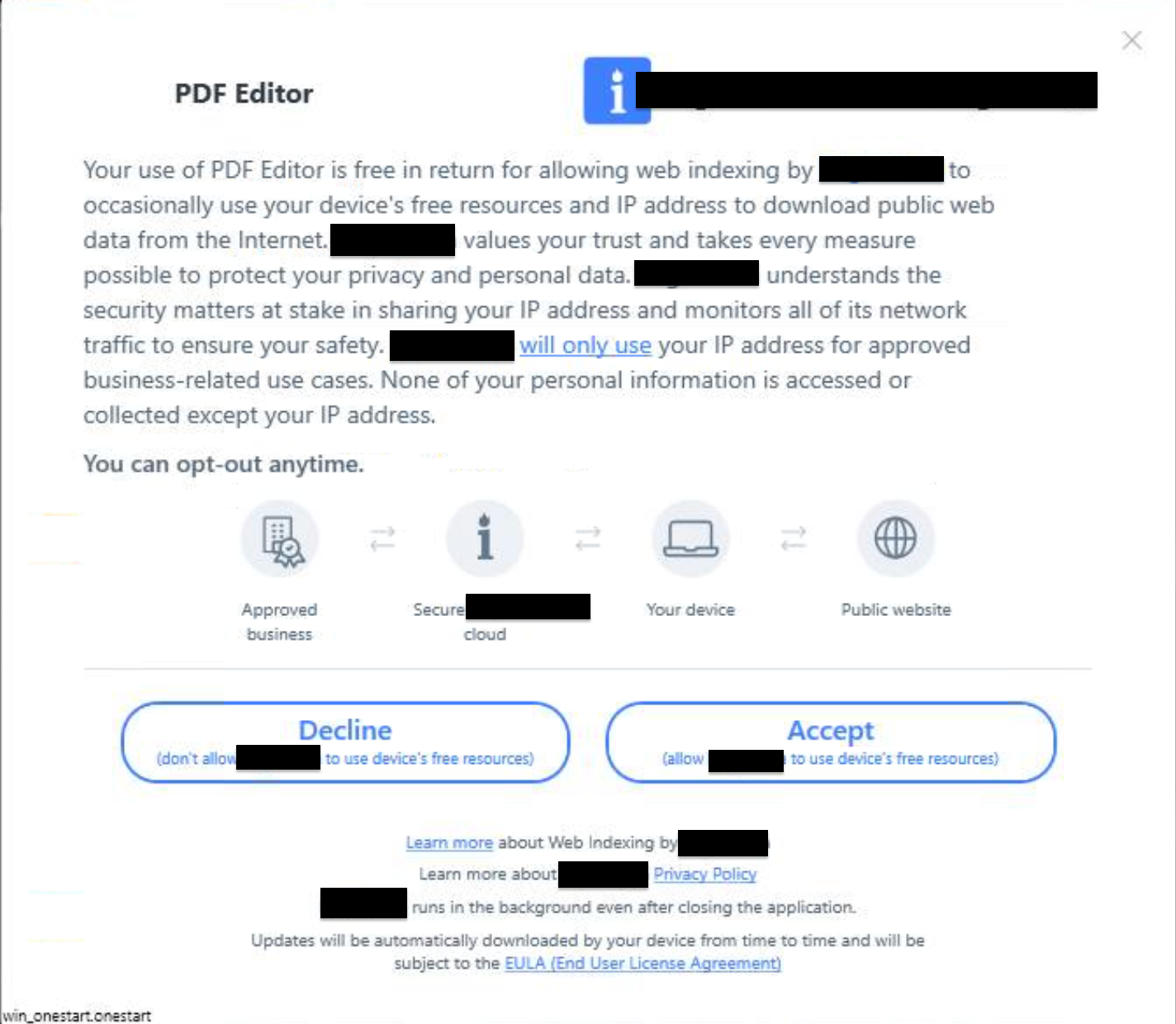
The name of the provider was redacted from the image, as in this particular case, we don’t have reason to believe that the provider is a part of the PDF Editor distribution. It’s likely that those behind AppSuite-PDF and PDF Editor are affiliates making money from installing a residential proxy.
It’s currently unknown whether this residential proxy is installed in all instances where PDF Editor is installed, or only in copies where this dialog is presented.
In other cases, we’ve observed evidence of PDF Editor interacting with a user’s browser files. We’re still investigating to understand the full extent of PDF Editor’s interactions.
What to do
We recommend removing software from these certificate signers from your systems. We’ve reported the code-signing certificates to the certificate providers, and the certificates have been revoked. The revocation can prevent some new installations, however, existing installations must be removed as well.
Utilize available endpoint logging via your SIEM or EDR tools, and scope for evidence of these certificate signers. Investigate scheduled tasks that execute JavaScript and remove them. Scope for evidence of the provided IOCs across your environment.
We also recommend blocking the associated files using EDR, and blocking the domains that are being used. We’ve provided a list of these domains at the end of this blog for reference.
Hunting
We also recommend removing the scheduled task from infected systems.
Reddit user FREAKJAM_ shared the following Defender XDR hunting query to find the JavaScript files associated with this campaign:
DeviceNetworkEvents
| where Timestamp > ago(30d)
| where ActionType == “ConnectionSuccess”
| where InitiatingProcessFileName =~ “node.exe”
| where InitiatingProcessCommandLine matches regex @”.*\\AppData\\Local\\TEMP\\[a-f0-9]{8}-[a-f0-9]{4}-[a-f0-9]{4}-[a-f0-9]{4}-[a-f0-9]{12}.*\.js”
| extend Username = extract(@”\\Users\\([^\\]+)\\”, 1, InitiatingProcessCommandLine)
| summarize
FirstSeen = min(Timestamp),
LastSeen = max(Timestamp),
TotalConnections = count(),
UniqueRemoteIPs = dcount(RemoteIP),
UniqueRemotePorts = dcount(RemotePort),
Usernames = make_set(Username),
RemoteIPs = make_set(RemoteIP, 5),
RemotePorts = make_set(RemotePort, 5),
RemoteUrls = make_set(RemoteUrl, 5),
SampleCommandLines = make_set(InitiatingProcessCommandLine, 3)
by DeviceName
| sort by TotalConnections desc;
IOC
The following is a representative list of file hashes as a part of this campaign. The JavaScript files may be unique by infection.
| File type | File hash | Context |
|---|---|---|
|
ManualFinderApp.exe |
71edb9f9f757616fe62a49f2d5b55441f91618904517337abd9d0725b07c2a51 | Files signed by “GLINT SOFTWARE SDN. BHD.” |
|
ManualFinder-v2.0.196.msi |
ed797beb927738d68378cd718ea0dc74e605df0e66bd5670f557217720fb2871 | Files signed by “GLINT SOFTWARE SDN. BHD.” |
| PDFEditor-1.0.0.8.exe | 9dc1b05b8fc53c84839164e82200c5d484b65eeba25b246777fa324869487140 | Files signed by “GLINT SOFTWARE SDN. BHD.” |
| PDFEditor.exe | 2e224a7a7bc6e85f8d16ae4258ee5f88a5bcc104148c0612250e6c2faf37a187 | Files signed by “GLINT SOFTWARE SDN. BHD.” |
| PDFEditor-1.0.0.8.ms | 66bfdce8dfc1e55f26fe41059cdcdf00178265a3c7045e608db6d428a13bd291 | Files signed by “GLINT SOFTWARE SDN. BHD.” |
| viewer.exe | 4fa75264d257ebef5d837150fec58994682335dd351356d302f12777f7156769 | Files signed by “GLINT SOFTWARE SDN. BHD.” |
| MainEXE | 0c1e64a631985dad7008c87958d1312d8bf75b4f41ff2901f479c7f716035042 | Files signed by “GLINT SOFTWARE SDN. BHD.” |
| ManualFinder (1).msi | d0838244e7ebd0b4bd7d7486745346af6b9b3509e9a79b2526dcfea9d83c6b74 | Files signed by “GLINT SOFTWARE SDN. BHD.” |
| MainEXE | 28c39ba950d2fb48b9733ce1ae590f763718ba9ede4619dc5261295f1c47ef20 | Files signed by “GLINT SOFTWARE SDN. BHD.” |
| 046bcdd6-c6e3-f8e1-f0d0-c571f9e41ab1b8abor.js | 5a925624ae4d0ecbad35415f8526e409cd724bb008077eaa3ef8b9fe25878c88 | JavaScript persistence |
| 9b9797f4-274c-fbb9-81ae-3b4f33b7010adb13or.js | ce49a3b1e4161fb1869d013f198a1f05888735f9cc31c357449a7ebdfd12af71 | JavaScript persistence |
| 847ded15-ec7d-ffca-8820-540cc25a975fd0f1or.js | 3a3f3834de56df0c6f360d07e67373db9606627c2cbb3adf2d6892ac25b9b5a9 | JavaScript persistence |
| 5793edeb-573d-4bda-9586-0db0fad02922ro.js | 785e6a82ff8e1f87af0de6870ffa84446aa8cda1fc5cf323a3d9a0a4f36a561b | JavaScript persistence |
| f939828b-2912-f5e5-8db0-c879c72067ef5e68or.js | 87867c63806735bf8906621291ee87a2a6f593009899fe96258e741606820e92 | JavaScript persistence |
| 4f168a73-06ba-ff25-f772-fc94db2880878395or.js | 3c00f83c095e8a84d9fb0dc47374a2434a056803c1bb2321ecf9882eea237c78 | JavaScript persistence |
| 598e5241-f2bb-42fe-8111-55029f6cfc13ro.js | 96deb9504cd93f2f8cba14238af4bcacf8135c64c54a8e8c5c1658d0aaac5a2a | JavaScript persistence |
| 1ed2c93b-597a-f072-8e8e-9c49024879882c28or.js | 73616f5e4ba6d21948339a2c4aa340000a729f4a62f15f39f7fcc2dac4a227a9 | JavaScript persistence |
| AppSuites-PDF-1.0.33.exe | 83efb5f2688207a7ccf49ddb81cb094543c2fef5bf73f01342cc39b0af68e72b | AppSuite-PDF signed by Summit Nexus Holdings LLC. |
| AppSuites-PDF-1.0.25.0.msi | 08ea829d5c97aab089abe19686d274f829aa1cee3670d2819885e33f39a4d602 | AppSuite-PDF signed by Echo Infini Sdn Bhd. |
| OneStart.exe | 7ae44a0606e74fa34cde274a0ed05b899992a9cda60124e8c60403774c7206bc | OneStart signed by Apollo Technologies Inc. |
Domains identified being used for pulling down additional files by the JavaScript persistence include:
- y2iax5.com
- 5b7crp.com
- mka3e8.com
- 5b7crp[.]com
Free PDF domains appear to be part of the advertising and delivery. We recommend blocking these domains to prevent download of these applications. These domains were reported to their registrar:
- allpdflive.com
- apdft.com
- appsuites.ai
- businesspdf.com
- convertpdfplus.com
- easyonestartpdf.com
- easypdfbox.com
- fastonestartpdf.com
- fullpdf.com
- getonestart.co
- getonestartpdf.com
- getpdfonestart.com
- getsmartpdf.com
- gopdfhub.com
- gopdfmanuals.com
- itpdf.com
- justpdflab.com
- manualsbyonestart.com
- mypdfonestart.com
- onestartbrowser.com
- onestartpdfdirect.com
- pdf-central.com
- pdf-kiosk.com
- pdfadmin.com
- pdfappsuite.com
- pdfartisan.com
- pdfdoccentral.com
- pdfeditorplus.com
- pdfmeta.com
- pdfonestart.com
- pdfonestarthub.com
- pdfonestartlive.com
- pdfonestarttoday.com
- pdforsmartminds.com
- pdfreplace.com
- printwithonestart.com
- proonestarthub.com
- proonestartpdf.com
- quickfastpdf.com
- quickpdfmanuals.com
- smarteasypdf.com
- smartmanualspdf.com
- smartonestartpdf.com
- smartviewpdf.com
- thepdfbox.com






