Threat intel · 4 MIN READ · KIM MAHONEY · OCT 27, 2025
TL;DR
- Expel has evolved its security approach to augment our best-in-class alert management to bolster proactive, intelligence-driven defense, built on unique insights gathered across our customer base and external sources.
- Expel’s proprietary internal intelligence enables us to develop highly precise detections, conduct active threat hunting, and identify emerging attacker behaviors before they escalate into major incidents.
- This means fewer false positives, faster investigation workflows, and catching threats before they become your problem—based on what we’re seeing across hundreds of customer environments.
The problem we’re actually solving
If you’re working in a SOC, you know the reality: catching threats after they trigger an alert is table stakes. The real challenge is identifying attack patterns before they show up as critical incidents in your queue at 3am.
In the very beginning of Expel, we focused on what most MDRs do (and are still doing)—managing alerts and responding to known threats. But here’s what we learned pretty early: public threat feeds and signature-based detections only get you so far. Sophisticated attackers don’t wait for their tactics to show up in threat feeds. They evolve faster than public intelligence can keep up. We understood very quickly that true security requires moving beyond pure reaction to embracing a proactive, intelligence-driven defense.
What changed in our approach
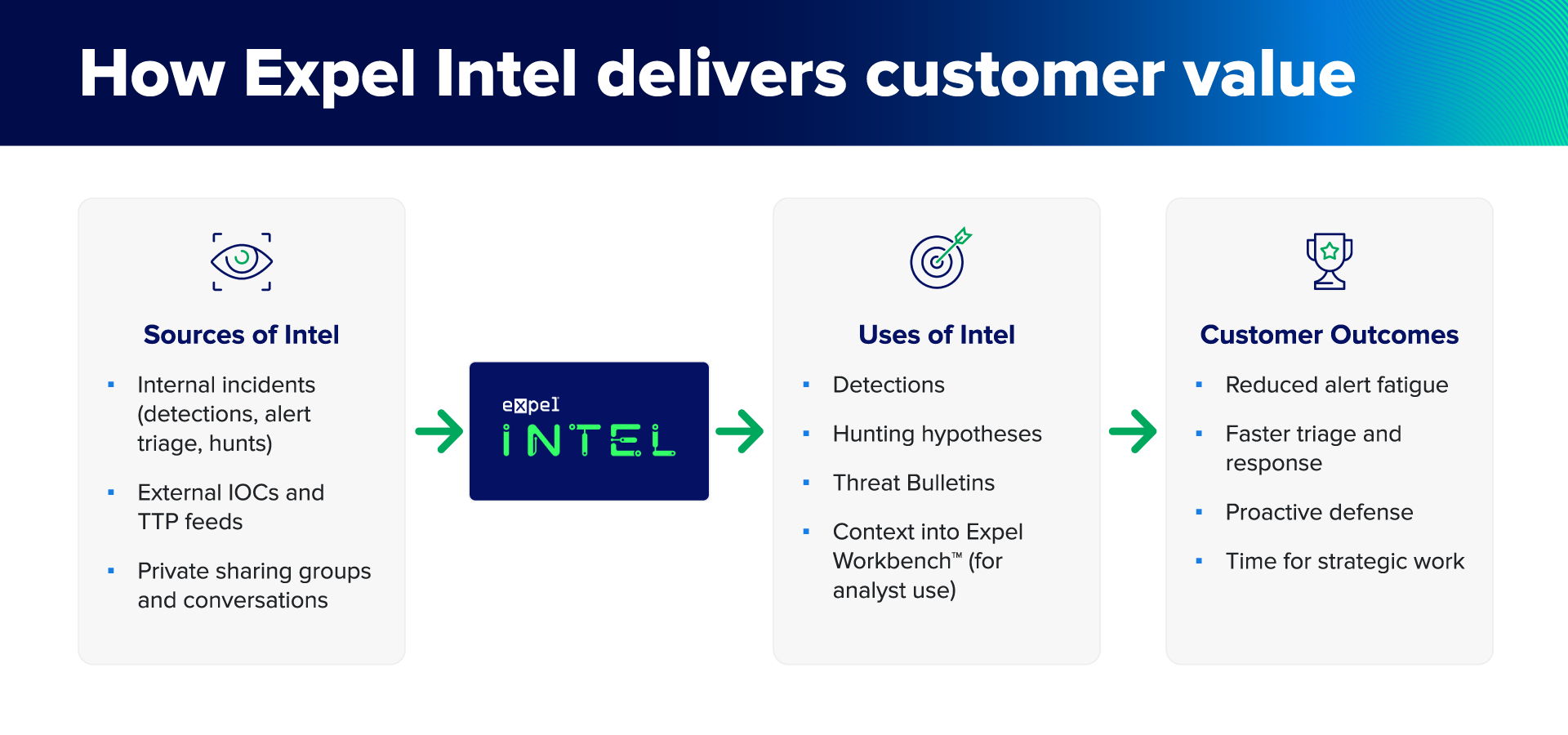
By observing attack patterns across our diverse customer base, we gained unique, real-time insights into emerging threats. When we see an attack technique hit three financial services companies in the same week, that’s signal. When we notice a specific malicious user agent attempting authentication across multiple Azure tenants, that’s actionable intelligence. Over time we evolved and expanded our threat intelligence capabilities to make them more actionable and valuable to our SOC and our customers.
So we built a dedicated threat intelligence function—not as a marketing checkbox, but as an operational capability that directly feeds our detection engineering and threat hunting workflows.
Here’s what this actually looks like in practice:
Detection engineering gets better inputs. We create catch-all detections for known malicious atomic indicators, mapped to MITRE ATT&CK (of course). But then we tune those rules for better precision by using the patterns we’ve observed across customer environments. Instead of generic “suspicious PowerShell execution” alerts, we’re creating detections for specific behavioral patterns tied to active threat campaigns.
Proactive hunting becomes targeted. When we identify a concerning pattern in one environment, our SOC analysts actively hunt for early indicators in other customer environments. We’re looking for threats before they mature into incidents.
You get actionable Threat Bulletins. When we identify critical threats, we send Threat Bulletins with specific guidance—not generic “increase monitoring” advice, but concrete steps based on what we’re actually seeing in the wild, along with any associated IOCs.
We develop deep expertise in high-risk areas. Patterns across our customer base help us build specialized knowledge in areas like identity attacks in Microsoft cloud environments.
Recent expansions
We’ve made some investments to scale these capabilities:
- Hired James Shank as Director of Threat Operations to manage our Expel Intel team, focusing on threat intelligence, vulnerability intelligence, and hunting operations. He’s got extensive industry experience with ransomware, DDoS, proxy abuse, and malware task forces.
- Brought on Marcus Hutchins as Senior Threat Intelligence Analyst. He’ll regularly contribute intelligence focused on ransomware, reverse engineering, and threat hunting.
- Expanded our Threat Bulletins in Expel Workbench™ with a dedicated threats page. It shows zero-day and emerging attacks, known IOCs, and results from hunts we’ve run across customer environments.
We’re also working on additional technology investments to continually scale our threat intelligence operations. More details coming as we finalize these capabilities.
What this means for your day-to-day
Let’s use a concrete example. Recently, an attacker used an obscure, newly discovered method to authenticate into a customer’s Azure environment. Because we’d already flagged this specific malicious user agent from incidents in other environments, our intelligence-driven Workbench detection fired immediately (but not even a peep from other technology monitoring tools in the environment).
Our analysts confirmed the activity and contained the threat—disabling the compromised account before the attacker could pivot or exfiltrate data. The customer’s internal team never saw the alert queue blow up. They got a summary of what happened and what we did about it (before even knowing there was a threat present).
For your SOC operations, this translates to:
Reduced alert fatigue. Better precision means fewer false positives clogging your queue. We actively update our detections to tune out noise and focus on actual threats—so you know when Expel flags an alert, it’s one you actually need to focus on.
Faster triage and response. When an alert fires, we’ve often already validated the threat pattern across other environments. You’re not starting from zero on every investigation.
Proactive defense that actually works. Threat hunting based on real attack patterns means we’re looking for threats in your environment before they trigger traditional detections. When your CISO asks “are we exposed to this new attack?” you’ll have an answer ready.
Time for strategic work. Less time firefighting generic alerts means more time for the security initiatives that actually improve your posture—like building playbooks, addressing systemic gaps, and whatever else is on your to-do list.
The bottom line
Threat intelligence isn’t a product you buy and deploy. It’s an operational discipline that requires continuous investment, analysis, and adaptation. We’re committed to maintaining visibility across the evolving threat landscape and feeding that intelligence back into our detection engineering, SOC operations, and hunting workflows.
This isn’t marketing spin—it’s how we’re working to make your job easier and your defenses more effective. The goal is simple: catch threats before they become your next 2am incident, using insights we’ve gained from observing attacks across hundreds of environments.
Have questions about how threat intelligence fits into your security operations? Want to know more about specific threat bulletins or hunting capabilities? Reach out—we’re happy to talk shop.