Network coverage
24x7 monitoring for a secure company network
Your firewall is great, but what about the traffic inside? We monitor to secure your network 24x7, finding the tactics that signal an attack.
Our difference
Find the signal in your network static
Our detection strategy gets more from your network security tools, focusing on attacker behavior to secure your company network from advanced threats.
Network security approach
How we secure your company network infrastructure
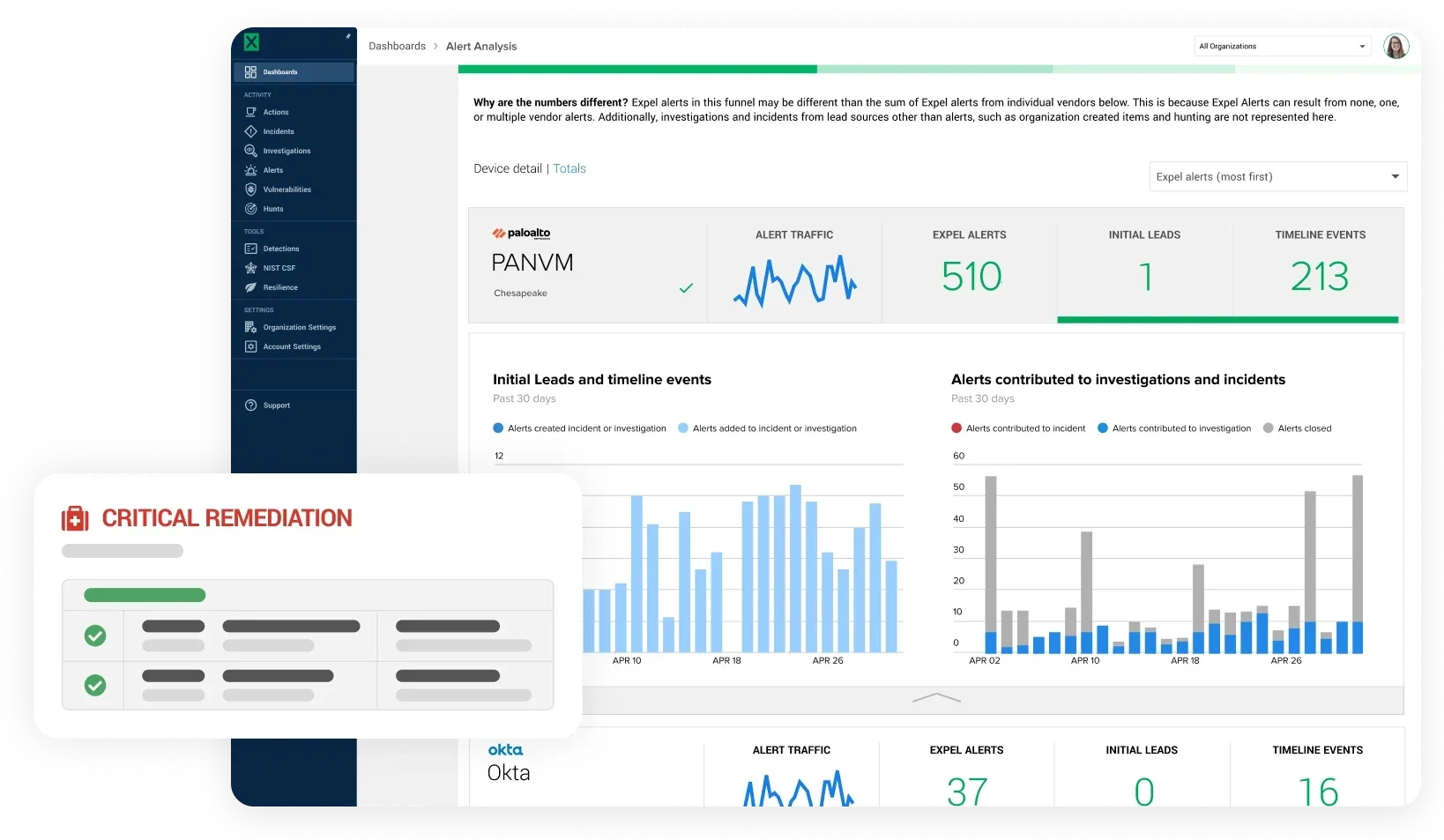
We pull the most useful signals from your existing network security stack—Palo Alto Networks, Zscaler, Darktrace, and more—ingesting traffic flow data and content. Our detection logic then helps spot unusual activity that indicates compromise. Alerts are enriched with IP/domain tracking to identify malicious patterns and see which assets or users are involved, providing critical context for any investigation.
Trusted to secure company networks worldwide












MDR Benefits
Why Expel for network security?
It’s not just about network alerts. We turn that visibility into a strategic advantage for your entire security operation.

Get more from your network security investment
We don’t just forward alerts. We build layered, high-fidelity detections on top of your tools to deliver powerful outcomes.
Fewer false positives, less chasing ghosts
Our detection engine filters out the noise. Your team spends less time chasing down phantom threats and more time focused on what’s real.
Connect the dots between attack surfaces
Our team gets the full story. We use network data to enrich other alerts, like seeing the C2 traffic behind a suspicious login.
Get answers, not just another alert stream
You get clear findings with plain-English explanations and step-by-step instructions so you can act fast, and with confidence.
Continuously updated detection logic
Our detection logic is continually refined based on real-world threats, keeping your company network secure against the latest attacker tactics.