Product · 3 MIN READ • KIM MAHONEY · AUG 20, 2025 · TAGS: Announcement
TL;DR
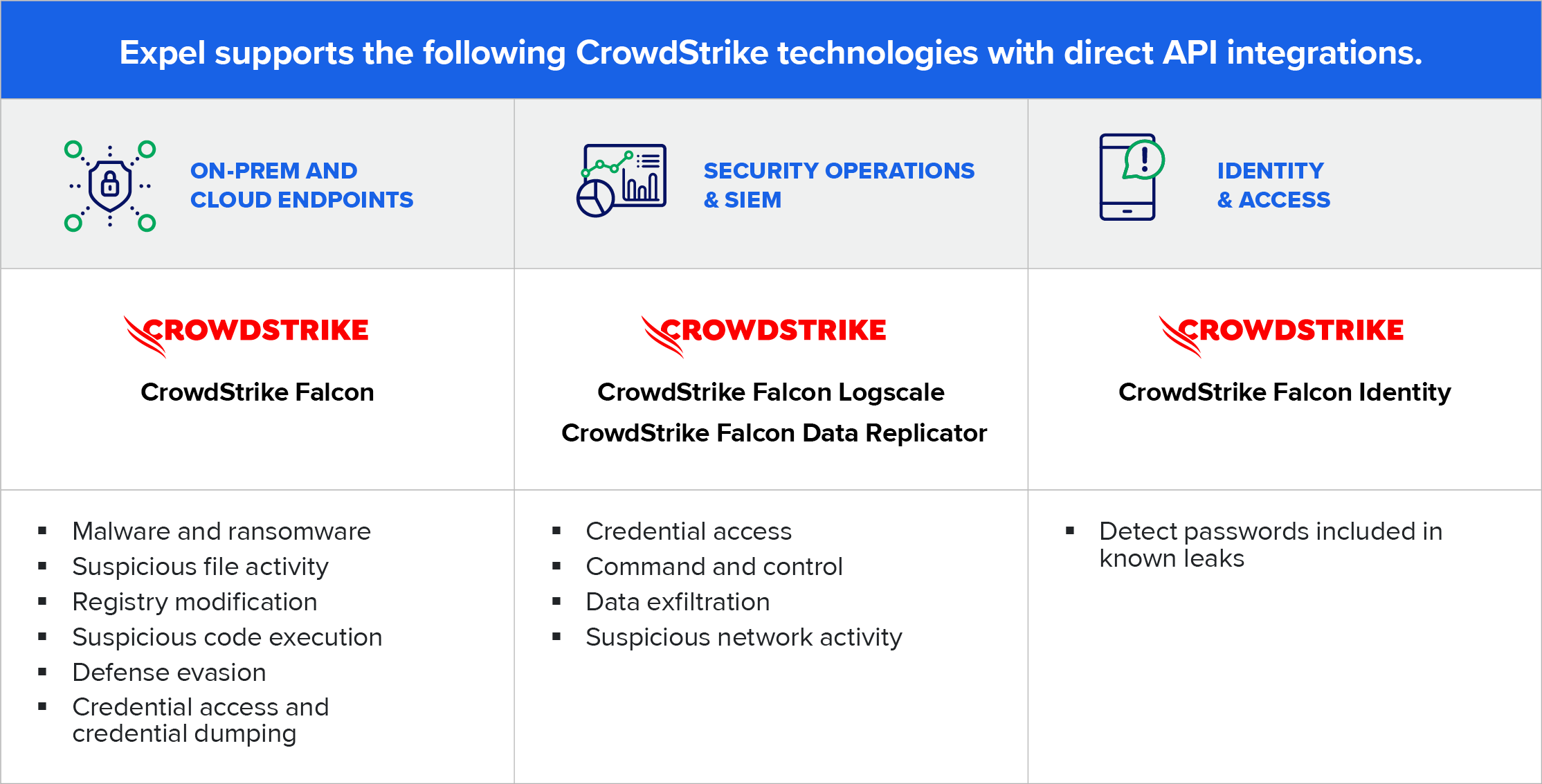
- Expel plugs into your existing CrowdStrike environment to give you expert threat detection and response, extending your team’s capabilities.
- We cut through the flood of CrowdStrike alerts by over 91% on average, freeing your team to focus on real threats.
- Our 24×7 security analysts deliver rapid investigations and remediation (17-minute MTTR for critical/high alerts), maximizing the value you get from your security tools.
As a security operations pro, you’re well aware of the battle: the alerts never stop, attacks keep getting craftier, and staying on top of it all is a constant fight. Even with a powerful platform like CrowdStrike in your arsenal, you’re likely still battling alert fatigue, dealing with staffing gaps, and worrying about what might slip through the cracks. Sound like your everyday? We get it. And that’s exactly why we built Expel.
Your CrowdStrike investment, amplified
Cybersecurity today is a tough game. We all see the relentless attacks and how they can bury even the best security teams, leading to that all-too-familiar alert fatigue—what we call ‘cyber strain.’ You’ve invested in CrowdStrike, a robust platform. But the sheer volume and cunning of today’s threats can still stretch your team thin.
This is where a managed detection and response (MDR) partner can make a real difference. Think of Expel as a vital layer of extra protection for your CrowdStrike environment. We help you make sense of incoming alerts and connect the dots across your identity, SaaS, and cloud environments—not just your endpoints. By bringing our own unique detection methods and fresh threat intelligence to the table, we enhance what CrowdStrike already does so well, helping to catch and respond to threats that might otherwise go unnoticed.
Our goal at Expel is to empower your security posture, helping you truly get the most out of your current security tools. We tackle common challenges head-on and aim to prevent business interruptions. We connect directly to your CrowdStrike environment via API, which means onboarding is straightforward and fast. We’re talking about security that works on day one, often delivering real value in days, hours, or even minutes. It’s about transforming complexity into clarity.
Always-on monitoring: eyes on your CrowdStrike environment
With Expel, you get 24×7 coverage across your endpoints, cloud, and more. And here’s a key point: we operate with full transparency. You’ll always know what we’re doing. Our expert security team, combined with our AI and automation-powered Expel Workbench™ platform, delivers tangible results: an average 17-minute mean time to remediate (MTTR) for critical and high alerts. This means faster action when it counts.
Here’s how we act as a true partner in monitoring your CrowdStrike investments:
- We ingest and normalize native alerts from all your security tools and cloud environments. Then, we enrich them with our own proprietary detection rules, which are constantly refined and aligned with the MITRE ATT&CK framework. This approach helps us focus on actual adversary tactics, catching threats early in their lifecycle.
- Our security analysts are always on duty. They don’t just pass alerts along; they thoroughly investigate, correlate data across your entire technology stack, and provide clear, actionable remediation guidance. We can even take containment actions when appropriate. Plus, we constantly feed threat intelligence from our entire customer base—what we see, you learn from—and external sources back into your environment. This helps us refine alerts, cut down on noise, and extract maximum security insights. Thanks to our built-in AI and automation, we’re able to reduce the noise from your CrowdStrike alerts by over 91% on average. This is about getting you to focus on what matters.
Staying in your console: the power of CrowdStrike Falcon status syncing
We know that constantly jumping between different security consoles is a productivity killer. It’s a major headache and a drain on your team’s valuable time. That’s why we recently enhanced our MDR service to sync Expel alert statuses directly into your CrowdStrike Falcon console.
So what does this mean for your team? When an Expel analyst triages an alert, investigates it, or takes an action related to your CrowdStrike environment, you’ll see that status reflected right there in your CrowdStrike Falcon interface. You no longer have to switch platforms to understand what’s happening or what’s been done. This direct synchronization provides immediate, transparent visibility. It helps your team stay informed and efficient, freeing them up for more strategic tasks instead of chasing administrative loose ends. It’s about right-sizing solutions for your team’s workflow.
Ultimately, Expel acts as a partner in your security journey. We help you maximize your CrowdStrike investment, allowing your team to truly focus on what matters most: proactive security and strategic initiatives, rather than getting buried in the daily alert avalanche. It’s security that’s built by security people, tailored to your needs.
Ready to learn more?
If you’re looking to get more out of your CrowdStrike security investment and finally get some peace of mind, it might be time to consider Expel MDR.