MDR · 5 MIN READ · NABEEL ZAFAR AND PATRICK DUFFY · MAY 31, 2022 · TAGS: AI & automation
TL;DR
- How our two-step automated security remediation process works (with a flowchart), what we can remediate, and how we keep you in the loop.
- Who does what – Expel or you? (Hint: most of the time, you decide.)
- Our automated security remediation roadmap (Blocking command-and-control (C2) communications, cloud turnoffs, disabling/modifying AWS access keys).
- Tips on what to ask any MDR provider about automated security remediation.
“If you find a problem in our environment, how do you remediate it?”
We get that question a lot. As we should — that’s one of the most important questions to ask when you’re looking for a managed detection and response (MDR) provider.
So here’s our answer to this question.
In this blog post, we’ll share Expel’s two-step automated security remediation process, provide insight into our automated security remediation offerings, and give you a glimpse of what’s ahead on our roadmap.
Our automated security remediation process
If we identify an incident, there are two sets of actions we’ll take – while keeping you in the loop throughout the process.
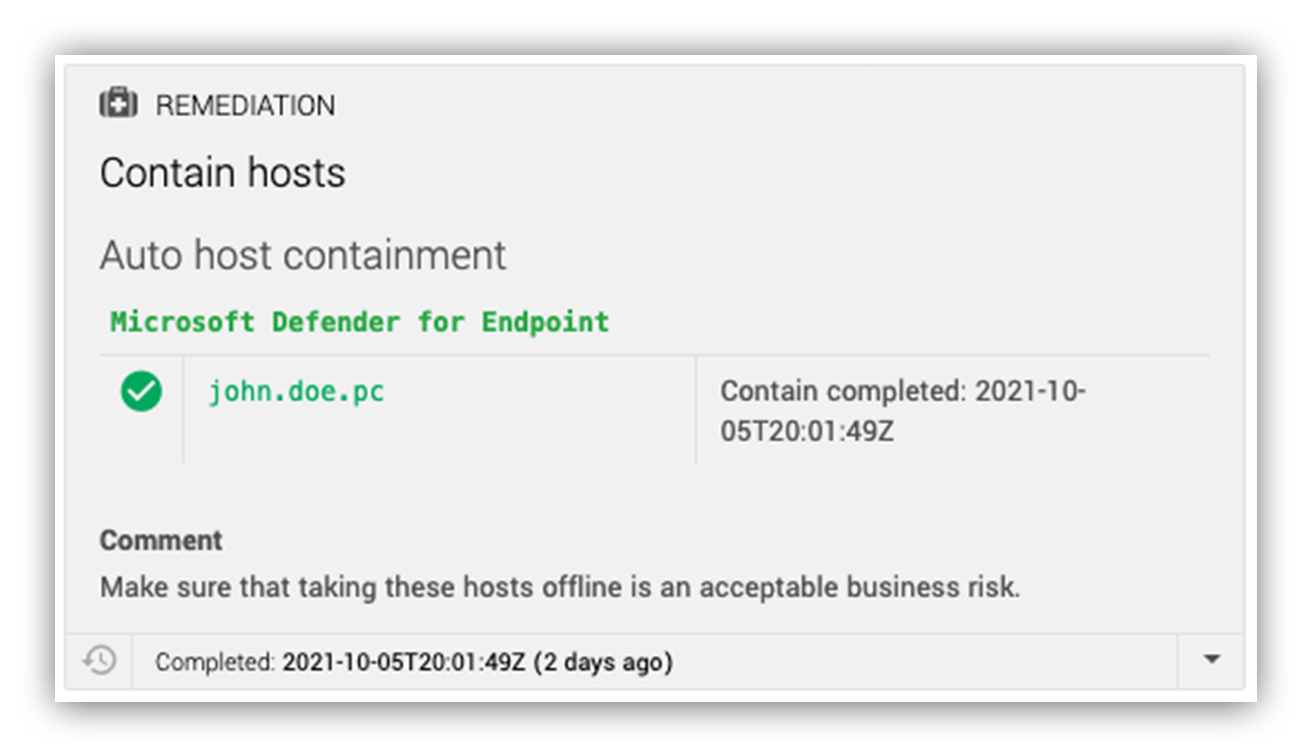
First, we’ll take approved actions on your behalf to quickly address the incident. For example, the Expel Workbench™ can automatically perform host containment, user account disablement, block known bad hashes, or remove suspicious emails when necessary during our security operations center (SOC) analysts’ investigation.
If these automated security remediation actions make sense, we quickly take first steps to contain infected hosts. This approach aligns with NIST incident response guidelines for rapid threat containment.
In the image below, you’ll see an example of what this looks like in the Expel Workbench.
Expel Workbench host containment action
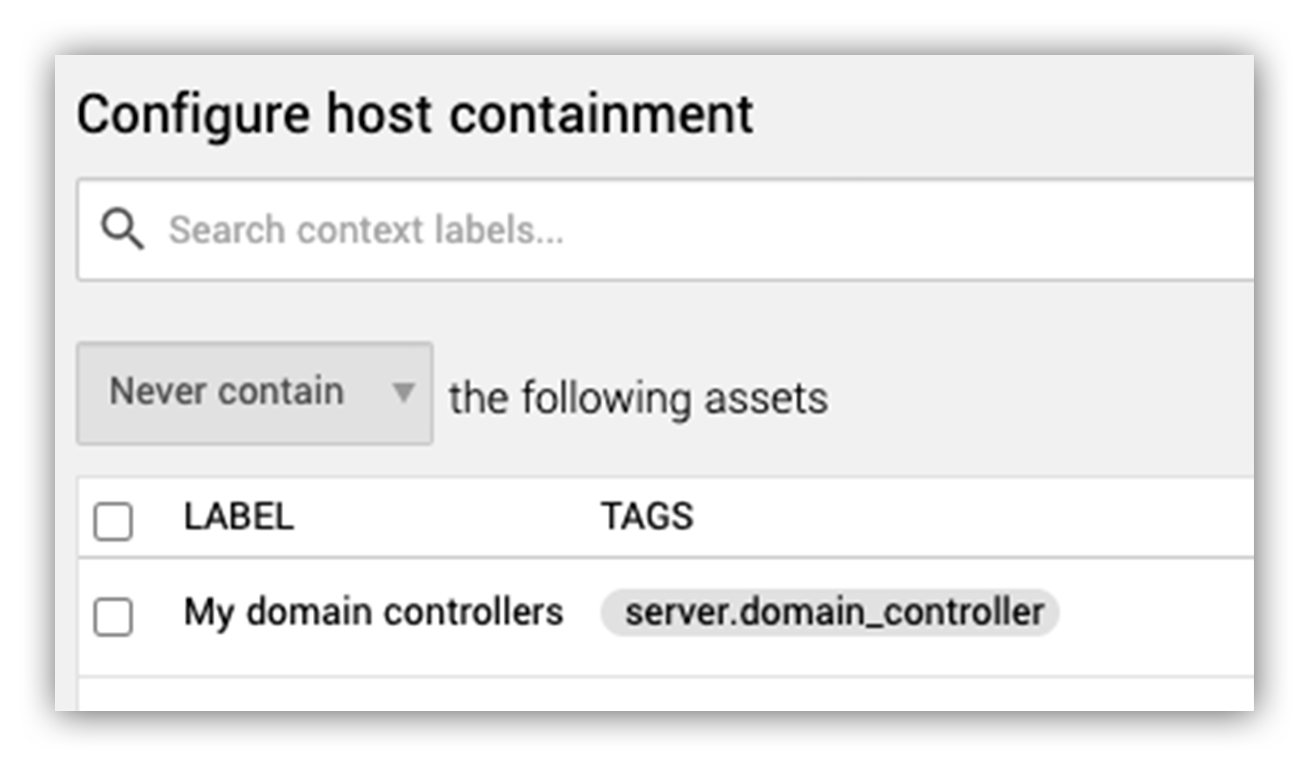
You can also customize the automated security remediation process through Workbench (see image below) by identifying hosts that you’d like us to act on — and any you don’t — for future remediation actions.
They also share updates on their activity in Workbench each step of the way.
Expel Workbench containment options
Expel supports automated security remediation for customers who have CrowdStrike, Microsoft Defender for Endpoint, SentinelOne Singularity Complete, VMware Carbon Black Cloud, VMware Carbon Black EDR, Palo Alto Cortex XDR Pro, Elastic Endpoint Security, and Cybereason.
Second, after taking automatic actions on your behalf, our SOC analysts recommend additional remediation actions in our findings report. We always communicate in plain English, so our recommendations are easy to follow and can be implemented at any level of security expertise.
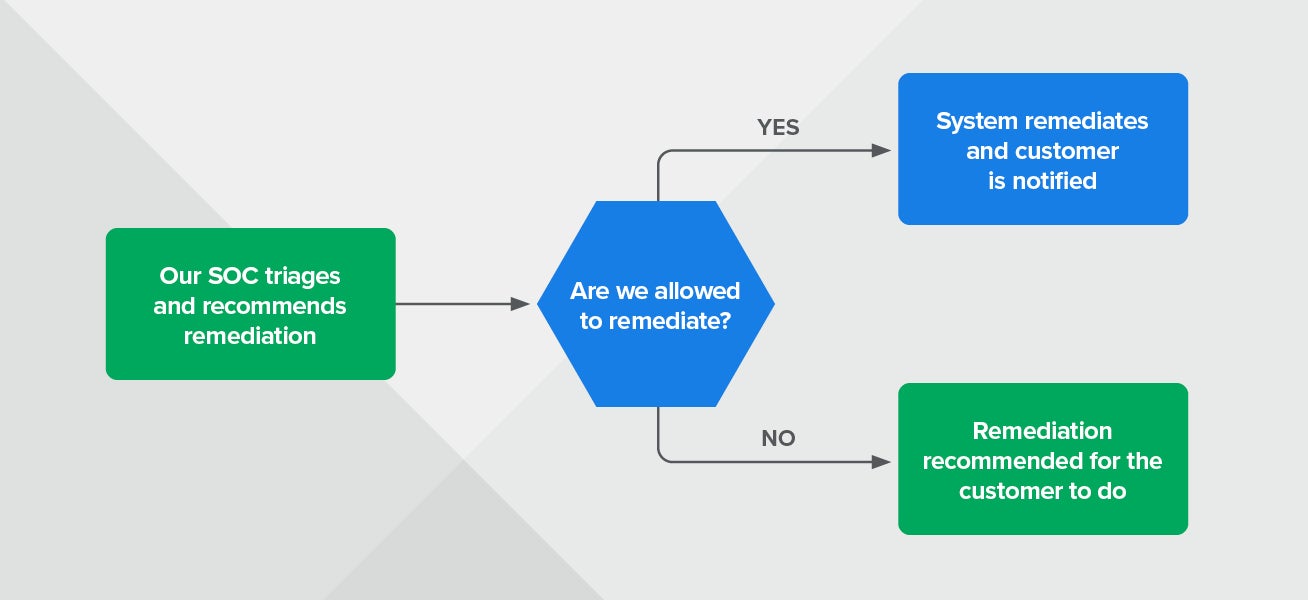
Want a 10-second overview of what our automated security remediation process looks like? We got you covered. Check out our remediation workflow in the diagram below.
Expel remediation workflow
Me or my MDR: who does what?
A lot of security practitioners who’ve purchased MDR services still want to maintain internal control of automated security remediation steps. It helps reduce business risk.
We get it.
We’ve found that our process strikes a balance between what security practitioners want to handle themselves and what they’d want their MDR to do.
But that doesn’t mean they shouldn’t look to their MDR to share their expertise.
We want your team to maximize your security and minimize incidents — and not spend a ton of time trying to figure out how to remediate. So if we spot trends in vulnerabilities or incidents across your environment, we’ll tailor resilience recommendations for how your org can fix the root cause of those issues and prevent them from needing automated security remediation time after time.
Taking steps to improve your security and keep those types of incidents from happening again helps us avoid having to call you in the middle of the night about remediation actions you need to take — right now!
What else can we auto remediate?
From business email compromise to malicious files to ransomware, we’ve got you covered. You tell us what you’d like us to remediate and which ones you’d prefer to handle.
Plus, 24×7 coverage means you have the time to plan your next steps… even if that means waiting until Monday morning.
Our approach to automated security remediation is personal to your organization and based on the frequency of threats seen in your environment. You’re in control of which users and endpoints you’d like us to immediately take offline after a compromise is confirmed, so you’re involved when you want to be — freeing up your team to focus on other security initiatives.
We have several automated security remediation steps (in addition to the ones outlined above) that consist of additional actions we can automatically take for you when responding to an incident. Modern automated incident response platforms enable these capabilities through integration with existing security tools.
Removing malicious email
- If malicious email is identified from a phishing submission, we’ll automatically remove it from users’ inboxes (and into the trash).
- Available for: Google Workspace
Blocking bad hashes
- When our analysts identify hashes to block during an incident, we create an automated security remediation action in Expel Workbench. If the hash isn’t on your “never block” list of files, Workbench adds the hash to the appropriate block list in your EDR.
- Available for: CrowdStrike, VMware Carbon Black Cloud, VMware Carbon Black Response, Microsoft Defender for Endpoint, SentinelOne Singularity Complete, Palo Alto Cortex XDR Pro and Elastic Endpoint Security.
Disabling user accounts
- Similar to host containment, Workbench will automatically disable user accounts when that automated security remediation action is added to an incident.
- Available for: Microsoft Defender for Endpoint, Microsoft Office 365, Microsoft Azure Identity Protection, Microsoft Active Directory, Microsoft Azure Log Analytics, and Microsoft Azure, Google Workspace, Okta, Github, and Duo.
Coming soon: advanced automated security remediation
We’ve talked you through our automated security remediation process today. But we’re constantly improving what we can do for our customers. So we have several new automated security remediation steps in the works on our roadmap. They consist of additional actions we’ll be able to automatically take for you while responding to an incident.
By taking critical, first steps to contain an incident, we decrease your remediation time even further — lifting more weight off your shoulders.
Here’s what’s next in the pipeline, prioritized based on how often we take certain remediation actions across our customer base and the level of risk each presents for our customers.
Blocking command-and-control (C2) communications
- When our SOC identifies C2 communications during an incident, we’ll automatically block them upon creation of an automated security remediation action in Workbench.
- Available for: Palo Alto Networks, Cisco Umbrella
Cloud turn-offs
- If a cloud instance is identified as compromised during an incident, we’ll automatically shut down the VM or EC2 through our automated security remediation workflow.
- Available for: AWS EC2 turn-off, Azure VM turn-off
Disabling/modifying AWS access keys
- If an AWS access key is identified as compromised during an incident, we’ll automatically disable/modify that key when an automated security remediation action is created.
- Available for: AWS
Best practices for automated security remediation
Understanding how automated security remediation fits into broader cybersecurity frameworks is crucial. Organizations should ensure their remediation processes follow established standards and integrate with existing SOAR (Security Orchestration, Automation, and Response) platforms for comprehensive incident management.
For more detailed information about specific automated security remediation capabilities, explore our comprehensive guides:
- Automated process termination for threat containment
- Registry key deletion for malware persistence removal
- Complete guide to automated security remediation
Final tips for evaluating automated security remediation
We wanted to end this post with some parting thoughts and tips for those currently looking for an MDR provider.
When you’re evaluating MDR providers, make sure you understand how their automated security remediation process works. Will they reduce risk quickly enough to protect your org? What will they do for you when it comes time to remediate an incident vs. what will you be asked to do?
Learn about their incident reporting and communication process to know when and how they’ll reach you during an investigation. And make sure you also know how they’ll walk you through automated security remediation.
Key questions to ask potential MDR providers about automated security remediation:
- How quickly can your automated security remediation responses be deployed?
- What level of customization do you offer for automated security remediation actions?
- How do you ensure automated security remediation actions don’t disrupt business operations?
- What reporting and audit capabilities do you provide for automated security remediation activities?
For more insights on automated remediation benefits and customization options, check out our detailed analysis.
Have any questions? Let’s chat!
Related automated security remediation resources
Explore more about automated security remediation and incident response: