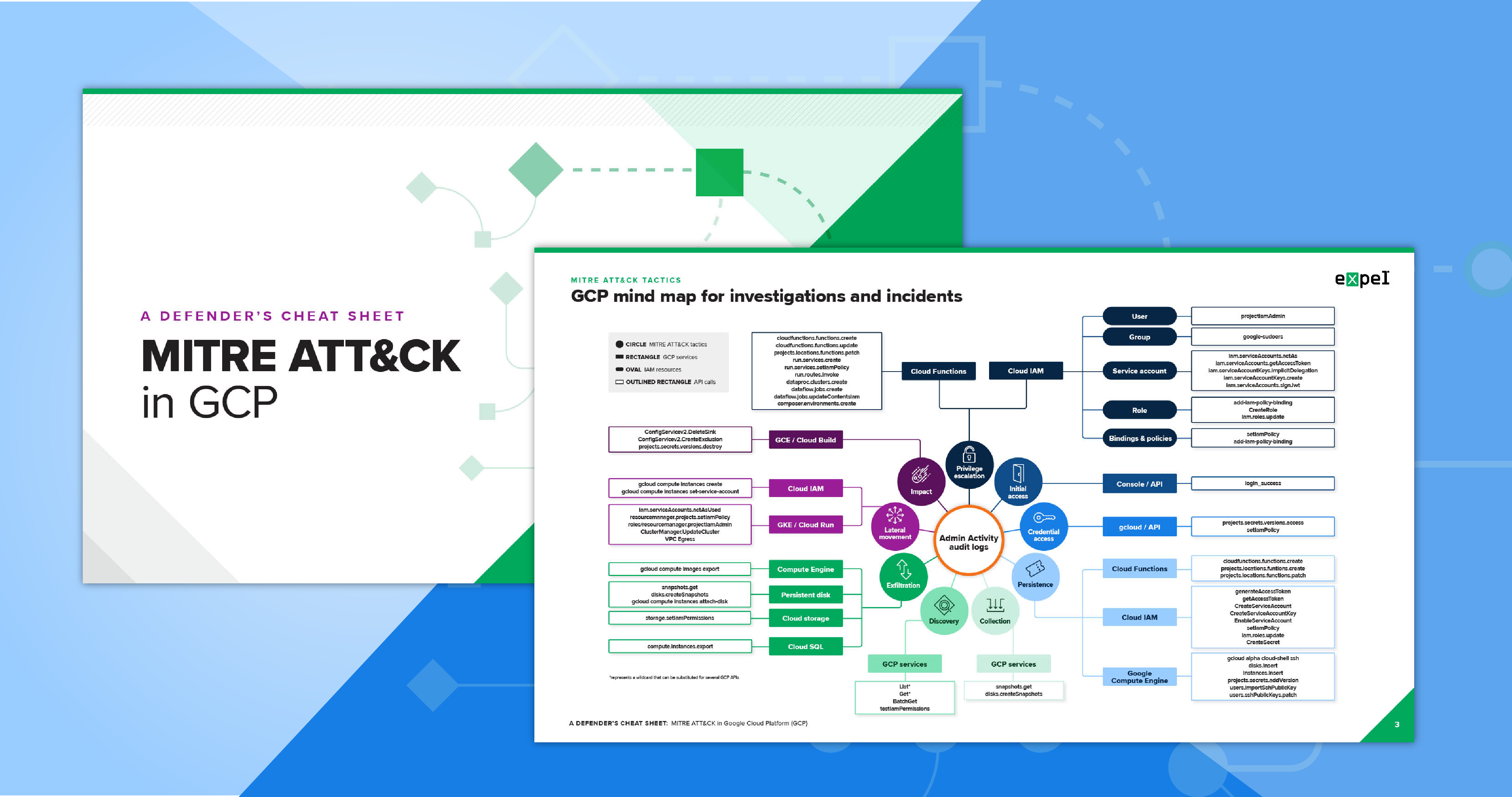
MITRE ATT&CK in GCP: Expel Mind Map Kit
Take the guesswork out of cloud investigations
Google Cloud Platform (GCP) and MITRE ATT&CK tactics – you’ve got those down.
But how does the classic MITRE ATT&CK framework map to the hundreds of services a crafty attacker might use to infiltrate in GCP?
Insert our mind map kit – a bundle of resources to help you identify potential attacks and map them to MITRE ATT&CK tactics.
You can even use it to identify risky activity and behaviors that can indicate compromise and require remediation.
When you download this kit, you’ll get:
- The GCP mind map which connects GCP and MITRE ATT&CK tactics
- A defender’s cheat sheet to serve as a guide for how to use the mind map and to better understand the tactics, techniques, and API calls that could be involved in an attack
- An editable mind map you can customize for your own SOC analysts to use during their investigations