Table of Contents
Deciding when to adopt managed detection and response (MDR) isn’t about checking boxes on a maturity assessment—it’s about recognizing the gap between the threats you’re facing and the resources you have to handle them. Organizations of all sizes and security maturity (and at many growth stages) levels turn to MDR when their internal teams can’t keep pace with the volume, velocity, and sophistication of modern cyber threats. Whether you’re a startup with limited security expertise or an enterprise with an established SOC that’s drowning in alerts, MDR bridges critical gaps in your security coverage.
When do I need managed detection and response?
The question isn’t necessarily “Do I need MDR?” but rather “When does MDR make the most sense for my organization?” Several clear scenarios signal it’s time to seriously consider MDR services.
You’re experiencing rapid business growth
Business expansion creates security blind spots. When your company is scaling quickly—adding new locations, onboarding hundreds of employees, or launching new product lines—your attack surface expands faster than your security team can adapt. According to Gartner, organizations should use MDR services to accelerate or augment existing security operations capabilities when growth outpaces internal resources.
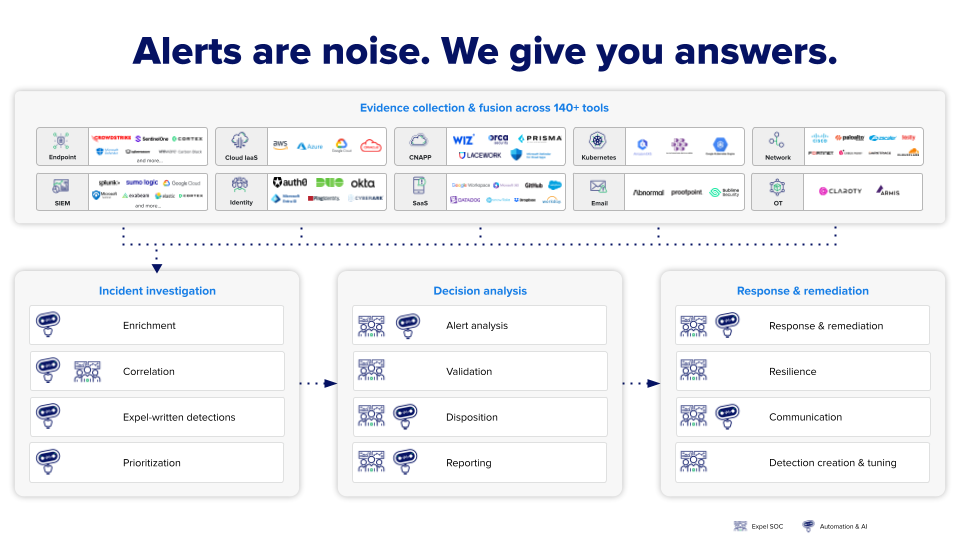
Cloud migration accelerates this challenge. Moving workloads to AWS, Azure, or Google Cloud introduces new security considerations that many traditional SOC teams aren’t equipped to handle. Expel helps organizations quickly detect advanced threats across endpoints, cloud, Kubernetes, SaaS, network, SIEM, email, and identity platforms—providing comprehensive coverage as your technology environment expands.
Your security team is overwhelmed
Security teams face significant challenges—too many alerts, no context, insufficient coverage and transparency into their technology, and never enough security experts to keep up. If your analysts are drowning in false positives, struggling to distinguish genuine threats from noise, or spending more time managing tools than investigating incidents, you’ve hit a critical tipping point.
Alert fatigue isn’t just inconvenient—it’s dangerous. When your team is overwhelmed by thousands of alerts daily, critical threats slip through while analysts burn out chasing false positives. MDR providers filter through this noise to deliver high-fidelity alerts that actually matter. Expel’s approach reduces alert noise significantly, with customers reporting dramatic decreases in false positive rates—from over 99% down to below 10%.
You’re facing compliance requirements
Regulatory frameworks increasingly mandate 24×7 security monitoring and documented incident response capabilities. Whether you’re subject to PCI DSS, HIPAA, SOC 2, or industry-specific regulations, demonstrating continuous security oversight becomes non-negotiable. Building an internal SOC to meet these requirements typically costs over $1 million annually—a significant investment that many organizations simply can’t justify (let alone the stress of doing this while navigating regulatory pressure to meet compliance minimums).
MDR provides a cost-effective path to compliance. With documented monitoring, investigation procedures, and incident reports, MDR services help organizations demonstrate they’re meeting regulatory security requirements without the overhead of building and maintaining an internal SOC infrastructure.
You lack 24×7 security coverage
Cyber attackers don’t observe business hours, weekends, or holidays. If your security monitoring stops when your team goes home for the night, you’re leaving a significant window of vulnerability. The average time between initial compromise and detection—known as dwell time—gives attackers ample opportunity to move laterally, escalate privileges, and exfiltrate data.
MDR services provide continuous 24×7×365 monitoring, ensuring that threats are detected and contained regardless of when they occur. This round-the-clock protection is particularly valuable for organizations operating across multiple time zones or those without the budget to staff three full shifts of security analysts.
What are signs you need an MDR?
Beyond the broad scenarios above, several specific indicators suggest your organization would benefit from MDR right now:
Your mean time to respond is too high. If it takes your team hours or days to investigate and respond to security alerts, attackers have too much time to accomplish their objectives. Industry-leading organizations achieve mean time to respond (MTTR) measured in minutes, not hours. Expel delivers a 17-minute MTTR on high and critical incidents—dramatically faster than most internal teams can achieve.
Slow response times compound over time. Every hour a threat remains active in your environment represents additional risk of data loss, system compromise, or business disruption. If your current MTTR exceeds an hour, MDR can provide immediate improvement.
Your security tools aren’t delivering value. Many organizations invest heavily in security tools—SIEM platforms, EDR solutions, cloud security tools—only to struggle with implementation, configuration, and ongoing management. If you’ve deployed security technology but lack the expertise to properly tune it, generate meaningful detections, or respond to its alerts, you’re not getting return on your investment.
MDR providers work with your existing technology stack, maximizing the value of tools you’ve already purchased. Rather than forcing you to rip and replace your security infrastructure, quality MDR services integrate with what you have—endpoint protection, SIEM platforms, cloud security tools—and make them more effective through expert configuration and continuous tuning. The right MDR solution for you will cover your entire threat landscape as-is, and in future growth.
You can’t attract or retain security talent. The cybersecurity talent shortage is real and worsening. With hundreds of thousands of unfilled security positions and intense competition for qualified candidates, many organizations simply cannot build the teams they need. Even if you successfully hire security analysts, retaining them presents another challenge—burnout rates in security operations are notoriously high.
Organizations facing these talent challenges see significant value in managed SOC services that provide required levels of expertise, readiness, and service without the recruiting headaches. MDR gives you immediate access to a team of seasoned security professionals without the hiring, training, and retention burden.
Your industry is facing increased threat activity. Certain sectors experience heightened targeting by threat actors—healthcare, financial services, education, government, and critical infrastructure all face sophisticated, persistent attacks. If threat intelligence indicates your industry is under increased scrutiny, waiting to enhance your security posture could prove costly. M&A activity is also often a trigger for bad actors to target a specific organization.
Proactive organizations don’t wait for a breach to invest in security. MDR provides hypothesis-based threat hunting capabilities that actively search for adversaries already lurking in your environment, identifying compromises before they escalate into full-blown incidents.
Can small companies use MDR? Is my company too small for MDR?
Absolutely—and you might benefit even more than larger enterprises. The misconception that MDR is only for large organizations with complex environments couldn’t be further from the truth. Expel serves companies of all sizes, recognizing that small and mid-sized organizations often face the same sophisticated threats as Fortune 500 companies but with far fewer resources to defend against them.
Why small organizations need MDR
Small companies present attractive targets for cybercriminals precisely because they typically have weaker defenses. Attackers know that smaller organizations often lack dedicated security staff, making them easier to compromise. Additionally, small businesses often serve as stepping stones to larger targets—compromising a small vendor or partner organization can provide attackers with pathways into enterprise networks.
Resource constraints hit smaller companies harder. While an enterprise might absorb the cost of hiring multiple security analysts, a small company with 50 employees simply cannot justify the same investment. A good MDR vendor provides flexible MDR offerings to meet organizations where they are in their security maturity journey, providing accessible options regardless of company size or budget.
Flexible approaches for growing companies
Modern MDR providers structure their services to accommodate different organizational needs and budgets. Rather than one-size-fits-all packages, flexible MDR offerings provide starter packages for organizations early in their security journey, with the ability to scale over time as needs evolve.
Think of MDR as fractional security expertise. Just as companies hire fractional CFOs or part-time legal counsel, MDR provides access to world-class security operations without the cost of building a full internal team.
When is it too early for MDR?
While MDR delivers value for organizations at virtually any maturity level, certain foundational elements should be in place to maximize effectiveness. Consider whether MDR might be premature if you fall into these categories:
You have no security tools deployed. MDR works by integrating with and enhancing your existing security technology. If you haven’t yet deployed basic endpoint protection, have no visibility into your network traffic, and lack logging capabilities, you’ll need to address these foundational gaps first. That said, many MDR providers can guide you in selecting and deploying appropriate security tools as part of the engagement.
You haven’t defined basic security policies. Before outsourcing security operations, organizations should have basic security policies established—even if they’re simple. Understanding what constitutes normal versus suspicious activity in your environment requires some baseline definition of acceptable use, access controls, and data handling procedures.
You’re not ready to act on findings. MDR providers deliver alerts, recommendations, and remediation guidance—but someone must act on that information. If your organization lacks processes for responding to security incidents or lacks the authority to take systems offline when necessary, the value of MDR diminishes significantly. Gartner advises that MDR providers should deliver actionable findings that internal teams can successfully react to.
You might not need MDR if…
Consider these scenarios where MDR might not be your most pressing need:
- You’re a very small company (under 10 employees) with minimal technology infrastructure and no sensitive data—basic antivirus and security awareness training might suffice.
- You have a fully staffed, high-performing SOC that’s meeting all your security objectives with manageable workload and excellent metrics.
- You’re in a non-regulated industry with minimal threat profile and have extremely limited budget—though even here, MDR often proves more cost-effective than a breach.
That said, these exceptions are increasingly rare. Most organizations benefit from MDR capabilities regardless of size or maturity.
What if I already have a SOC?
Having an existing SOC doesn’t preclude MDR—in fact, many of the most sophisticated security programs combine internal capabilities with managed services. Think of MDR as augmentation rather than replacement.
Hybrid models work well
Many organizations adopt hybrid approaches where internal SOC teams handle certain functions while MDR providers supplement in specific areas. This might mean:
- Using MDR for after-hours coverage while your internal team handles daytime operations.
- Leveraging MDR for specialized detection coverage in cloud environments while keeping network and endpoint monitoring in-house.
- Partnering with MDR for advanced threat hunting while your team focuses on incident response and remediation.
According to Gartner, 60% of organizations will be actively using remote threat disruption and containment capabilities delivered directly by MDR providers—many of these already have internal SOCs.
Addressing SOC limitations
Even well-staffed SOCs face limitations. Your internal team might excel at responding to incidents but lack expertise in specific areas like cloud security, container security, or advanced threat hunting. MDR fills these gaps without requiring you to hire specialists in every emerging technology domain.
Additionally, MDR can relieve pressure on overworked SOC teams. If your analysts are buried in Level 1 triage work, MDR can handle the initial investigation, freeing your senior staff to focus on higher-value strategic security initiatives.
What if I already have a SIEM?
SIEM platforms are valuable security tools, but they require significant expertise to deliver value. If you’ve invested in a SIEM but struggle with configuration, detection rule development, or alert management, MDR can unlock the potential of your existing investment.
Making your SIEM more effective
MDR providers enhance SIEM platforms by providing expert detection engineering, continuous rule tuning, and 24×7 monitoring. Rather than replacing your SIEM, quality MDR services integrate with it, leveraging its data collection capabilities while adding the human expertise needed to generate actionable insights.
Many organizations deploy SIEMs but never realize their full potential because they lack the dedicated resources to write detections, tune rules, and investigate alerts. Expel’s approach includes extensive detection libraries for SIEMs, reducing the burden on internal detection engineering teams while improving coverage.
Addressing common SIEM challenges
SIEMs generate enormous volumes of alerts—many of which are false positives or low-priority events. MDR cuts through this noise using advanced correlation, context enrichment, and expert analysis. This means fewer alerts for your team to wade through and higher confidence that the alerts you do receive represent genuine threats.
Additionally, SIEM platforms often require significant ongoing maintenance, tuning, and optimization. MDR providers handle this operational burden, ensuring your SIEM remains effective as your environment evolves and new threats emerge.
How do I know if I’m ready for MDR?
Assess your readiness by asking yourself these decision-making questions:
Consider MDR if you answer “yes” to three or more:
- Does it take your team more than an hour to investigate and respond to security alerts?
- Are your security analysts spending more than 50% of their time on false positives?
- Do you lack coverage during nights, weekends, or holidays?
- Have you deployed security tools that aren’t being used to their full potential?
- Are you struggling to hire or retain qualified security talent?
- Are you facing compliance requirements for 24×7 monitoring?
- Is your business expanding faster than your security team can scale?
- Do you lack expertise in emerging areas like cloud security or container security?
- Has your industry seen increased threat activity in the past year?
- Would a security incident significantly impact your business operations or reputation?
Taking the next step
If you’ve determined MDR makes sense for your organization, Gartner recommends defining specific required outputs and goals before engaging with providers. Consider:
- What specific security outcomes are you trying to achieve?
- Which attack surfaces need the most immediate coverage?
- What metrics will you use to evaluate MDR effectiveness?
- How will MDR findings integrate with your existing incident response processes?
The cybersecurity landscape continues evolving, with threats growing more sophisticated and regulatory requirements becoming more stringent. Organizations waiting for the “perfect time” to adopt MDR often find themselves responding to incidents they could have prevented. The right time to consider MDR is when you recognize the gap between the threats you face and the capabilities you have—and for most organizations, that time is now.