Table of Contents
If you’re building or running a security operations center (SOC), you’ve probably noticed there’s no shortage of vendors claiming their tool is the “must-have” for your team. The reality? A modern SOC needs a carefully selected technology stack that works together to detect, investigate, and respond to threats effectively.
Let’s break down what technologies actually make a difference in a SOC environment, and how to think about building a stack that works for your team rather than against it.
What’s a SOC technology stack?
A SOC technology stack is the collection of security tools, platforms, and systems enabling your security team to monitor, detect, analyze, and respond to cyber threats. Think of it as a foundation allowing SOC analysts to do their jobs effectively.
Unlike a simple collection of point solutions, an effective technology stack for security operations has tools that integrate with each other, share data, and create a cohesive workflow. The goal isn’t to have the most tools—it’s to have the right tools working together seamlessly.
A typical SOC technology stack includes several layers: data collection and monitoring tools, threat detection and analysis platforms, incident response and orchestration systems, and threat intelligence feeds. Each layer serves a specific purpose, but the magic happens when they communicate with each other to provide context and enable rapid response.
What are good security operations center tools?
Good SOC tools share a few key characteristics: they reduce noise rather than create it, they integrate well with other security technologies, and they actually help analysts work more efficiently rather than adding to their workload.
The best security operations center tools provide high-fidelity alerts with context, not just raw data dumps. They should help your team prioritize what matters most and filter out the false positives that waste precious analyst time. Look for tools offering customizable detection rules, automated enrichment capabilities, and clear investigation workflows.
Integration capabilities are non-negotiable for modern SOC tools. Your technologies need to share data through APIs, support common standards like STIX/TAXII for threat intelligence, and work within your existing security architecture. Tools operating in silos create blind spots and slow down investigations.
User experience matters more than many vendors acknowledge. If a tool requires extensive training or has a clunky interface, your analysts will struggle to use it effectively during high-pressure incidents. The best SOC tools balance powerful capabilities with intuitive design.
What tools do SOC teams use?
SOC teams typically use a combination of tools across several categories. Let’s look at the core technologies you’ll find in most mature security operations environments.
SIEM platforms serve as the central nervous system for many SOCs. A security information and event management (SIEM) platform collects, correlates, and analyzes security data from across your environment. It aggregates logs from firewalls, endpoints, cloud services, and applications, then applies correlation rules to identify potential security incidents. Modern SIEM platforms include advanced analytics, machine learning capabilities, and built-in threat intelligence.
Endpoint detection and response (EDR) tools monitor and protect individual devices—laptops, servers, mobile devices—across your organization. EDR solutions provide visibility into endpoint activities, detect suspicious behavior, and enable rapid response to threats. They track process execution, file modifications, network connections, and registry changes to identify indicators of compromise.
Extended detection and response (XDR) platforms take endpoint protection further by correlating security data across multiple domains—endpoints, networks, cloud workloads, and email. XDR provides a unified view of threats as they move through your environment, connecting the dots between seemingly unrelated events.
Threat intelligence platforms help SOC teams stay informed about the latest threats, attack techniques, and indicators of compromise. These platforms aggregate intelligence from multiple sources, including commercial feeds, open-source intelligence, and industry sharing groups. Good threat intelligence helps analysts understand the “who” and “why” behind attacks, not just the “what.”
Network security monitoring tools provide visibility into network traffic patterns and can detect anomalous behavior, lateral movement, and data exfiltration attempts. These include network traffic analyzers, intrusion detection systems (IDS), and network detection and response (NDR) platforms.
SOAR orchestration platforms (security orchestration, automation, and response) help SOC teams automate repetitive tasks and orchestrate complex response workflows. SOAR platforms connect your security tools, automate data enrichment, and enable consistent incident response procedures.
What are essential SOC technologies?
While the specific tools vary by organization, certain technology categories are essential for an effective modern SOC. Let’s prioritize what you actually need versus what’s nice to have.
Essential core technologies include:
A SIEM platform provides the central hub for security event correlation and analysis. While there’s debate about whether SIEM is truly required (which we’ll address shortly), some form of centralized log management and correlation engine remains fundamental for most SOCs.
Endpoint protection is non-negotiable. Whether you choose traditional EDR or more advanced XDR, you need visibility into what’s happening on devices across your organization. Endpoints are where many attacks begin and where data ultimately lives.
Threat intelligence capabilities, whether through a dedicated platform or integrated into other tools, help your team understand the threat landscape and prioritize response efforts based on real-world attack trends.
Case management systems keep track of investigations, maintain audit trails, and ensure incidents are properly documented and resolved. This might be built into your SIEM, part of a SOAR platform, or a standalone system.
Important but flexible technologies include:
Network security monitoring tools provide valuable context, but the specific implementation varies based on your environment. Cloud-native organizations might prioritize cloud security tools over traditional network monitoring.
Vulnerability management platforms help identify and prioritize security weaknesses before attackers exploit them. While essential for security programs broadly, the direct SOC integration varies by organization.
Security analytics capabilities, often powered by machine learning and behavioral analysis, help identify threats evading signature-based detection. These might be standalone tools or features within your SIEM or XDR platform.
What is a security operations platform?
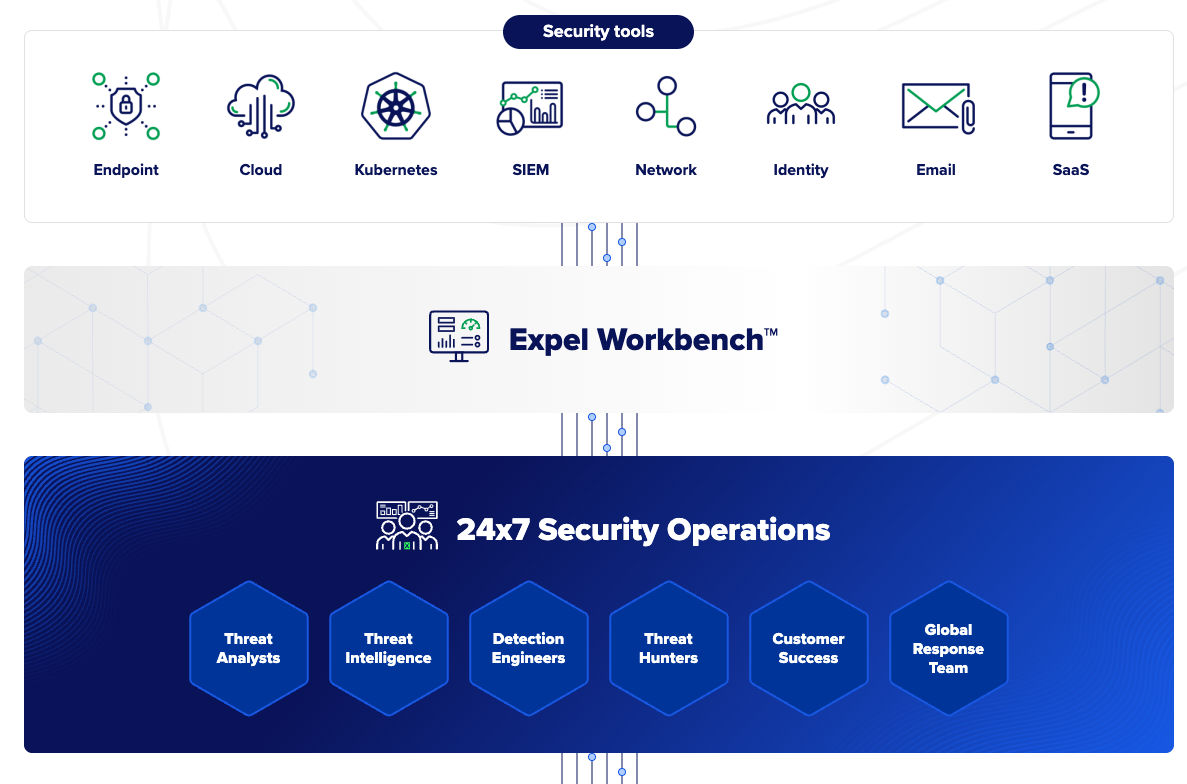
A security operations platform is an integrated system that brings together multiple security capabilities into a unified environment. Rather than managing ten separate tools with ten different interfaces, a security operations platform provides a single pane of glass for detection, investigation, and response.
Think of it as the evolution beyond traditional point solutions. Security operations platforms typically combine SIEM functionality, threat intelligence, case management, and orchestration capabilities. Some also incorporate EDR, network detection, or cloud security features.
The key advantage is integration. When your technologies share a common data model and workflow, analysts can investigate faster, correlate events more effectively, and respond more consistently. Context from threat intelligence automatically enriches security alerts. Investigation findings flow directly into case management. Response actions can be triggered across multiple tools from a single interface.
That said, “platform” doesn’t always mean a single vendor solution. Some organizations build effective security operations platforms by thoughtfully integrating best-of-breed tools through APIs and common data layers. The goal is creating a cohesive operational experience, whether it’s achieved through one vendor or many.
Is SIEM required for a SOC?
This is one of the most debated questions in security operations. The short answer: not always, but most SOCs still benefit from some form of centralized log management and correlation.
Traditional SIEM platforms have challenges—they’re often expensive, complex to manage, and can generate significant noise. Some organizations, particularly those who are cloud-native or have adopted XDR platforms, find they can operate effectively without a traditional SIEM.
However, SIEM platforms still provide several capabilities valuable for most SOCs. They offer a centralized repository for security logs required for compliance. They enable correlation across diverse data sources not covered by your XDR platform. They provide long-term data retention for historical analysis and threat hunting.
Modern security operations might use a SIEM differently than in the past. Rather than being the primary detection engine, it might serve as a data lake for threat hunting, a compliance logging solution, or a backup correlation layer for threats evading more specialized detection tools.
Some organizations are exploring alternatives like security data lakes or extended detection and response platforms incorporating traditional SIEM capabilities. The question isn’t really “do I need a SIEM?” but rather, “how do I centralize, correlate, and analyze security data effectively?”
A modern SOC needs centralized security data analysis—whether you call it SIEM, a security data lake, or something else is less important than ensuring you have the capability.
What’s the difference between EDR and XDR?
EDR (endpoint detection and response) and XDR (extended detection and response) are related but distinct technologies, which cause plenty of confusion in SOC discussions.
EDR solutions focus specifically on endpoints—laptops, servers, mobile devices. They provide deep visibility into endpoint activities, detect suspicious behavior, and enable response actions like isolating infected machines or killing malicious processes. EDR excels at understanding what’s happening on individual devices, tracking process execution, file modifications, and registry changes.
XDR platforms extend this approach beyond endpoints to include other security domains: networks, cloud infrastructure, email systems, and identity platforms. XDR correlates data across these different sources to detect attacks spanning multiple domains. For example, XDR might connect a phishing email to suspicious endpoint behavior to unusual network traffic, revealing an attack chain that wouldn’t be obvious when looking at any single data source.
Think of EDR as depth and XDR as breadth. EDR provides detailed visibility and control at the endpoint level. XDR provides broader visibility across your entire environment with correlation across different security domains.
Most organizations don’t choose between EDR and XDR—XDR platforms typically include strong endpoint capabilities (often built on EDR technology) while adding the cross-domain correlation and analysis. If you’re starting fresh, XDR might make sense. If you already have strong EDR, you might integrate it into a broader detection and response strategy through a SIEM or security operations platform.
The key is ensuring you have both endpoint visibility and the ability to correlate across your environment. Whether it comes from EDR plus SIEM, a comprehensive XDR platform, or some other combination depends on your specific needs.
How many tools does a typical SOC use?
Industry surveys suggest the average SOC uses somewhere between 20 and 75 security tools, though the wide range tells you something important: there’s no magic number.
What matters isn’t how many tools you have, but whether those tools work together effectively and whether your team can actually use them well. A SOC struggling to manage 15 poorly integrated tools isn’t going to improve by adding five more, even if vendors promise those additions will “solve” the integration problem.
A lean, effective SOC technology stack might include:
- One SIEM or security operations platform
- One EDR/XDR solution
- Threat intelligence feeds (commercial and open-source)
- Network security monitoring tools
- Cloud security tools matching your cloud providers
- Email security gateway
- SOAR platform for automation
- Case management system
- Vulnerability scanner
That’s roughly 10-15 core technologies, with additional tools for specific use cases or compliance requirements. The key is ensuring these core technologies integrate well, share data effectively, and support your team’s workflows.
More mature SOCs might add specialized tools for specific threats (like DDoS protection), dedicated threat hunting platforms, deception technologies, or industry-specific security tools. But these should be additions to a solid foundation, not band-aids for gaps in your core stack.
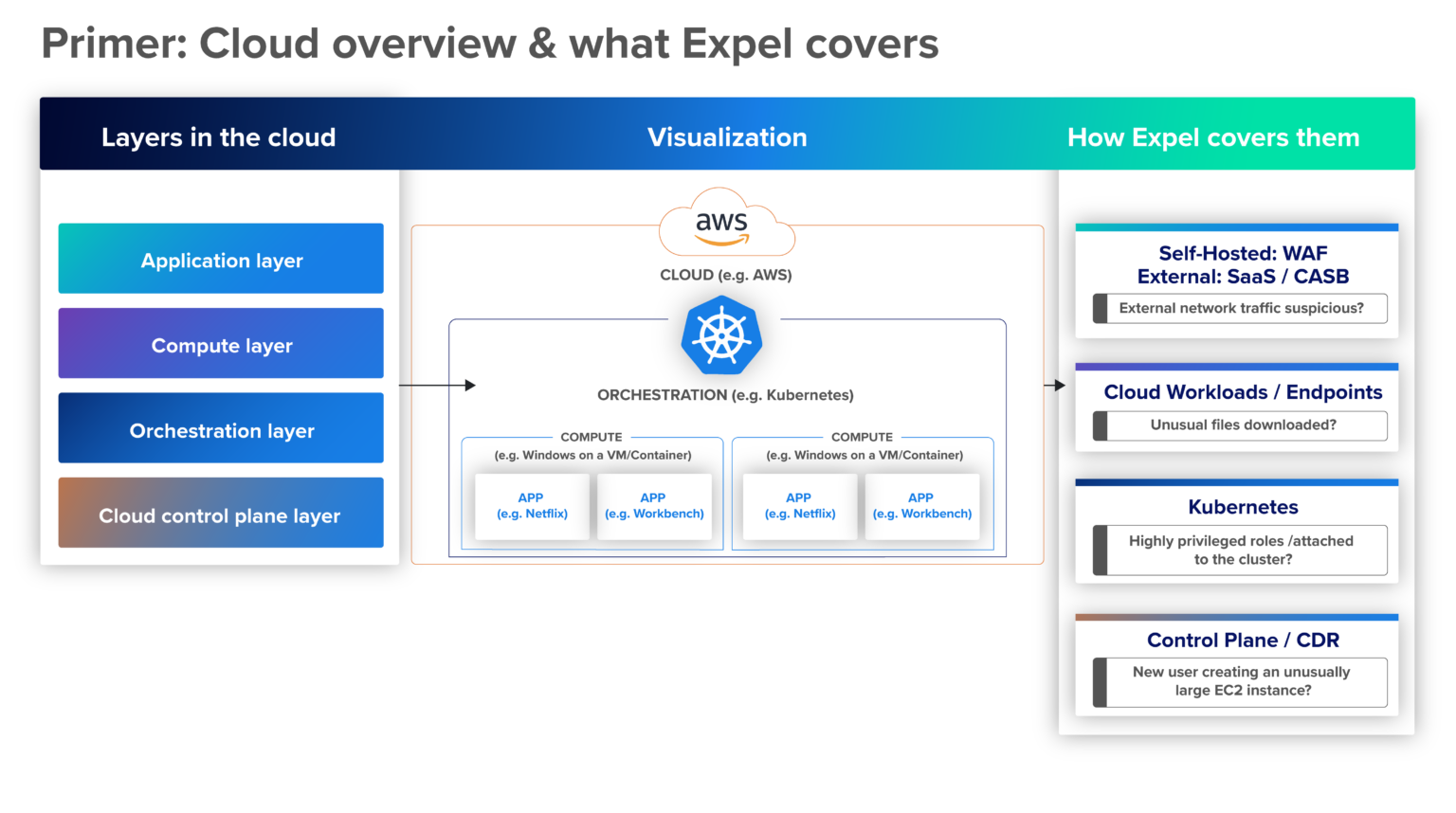
What about cloud security tools?
Cloud security tools have become essential for SOCs as organizations migrate workloads to AWS, Azure, Google Cloud, and other cloud platforms. Traditional security tools often lack visibility into cloud-native environments, creating dangerous blind spots.
Key cloud security technologies for SOCs include:
Cloud security posture management (CSPM) tools continuously assess cloud configurations against security best practices and compliance frameworks. They identify misconfigurations like overly permissive access controls, unencrypted storage, or exposed databases.
Cloud workload protection platforms (CWPP) secure cloud workloads—virtual machines, containers, serverless functions—throughout their lifecycle. They provide vulnerability management, runtime protection, and compliance monitoring for cloud-native applications.
Cloud access security brokers (CASB) provide visibility and control over cloud applications, especially SaaS services. They enforce security policies, detect anomalous usage, and protect sensitive data in cloud applications.
Many modern XDR and security operations platforms now include cloud security capabilities, reducing the need for standalone tools. However, organizations with significant cloud infrastructure often need specialized cloud security tools who provide deeper visibility than general-purpose platforms.
The integration between cloud security tools and your broader SOC technology stack is critical. Cloud security alerts should flow into your SIEM or security operations platform, cloud threat intelligence should inform endpoint and network detections, and response actions should extend to cloud workloads.
Can you have too many SOC tools?
Absolutely. Tool sprawl is one of the biggest challenges facing modern SOCs, and it actively undermines security effectiveness.
Every additional tool brings costs beyond the license price. Each tool requires configuration, tuning, and ongoing maintenance. Analysts need training. Integrations need to be built and maintained. Updates need to be tested. And most importantly, each tool generates alerts analysts must triage.
The problem compounds when tools overlap in coverage. Multiple systems detecting the same threat in slightly different ways doesn’t provide defense in depth—it creates confusion and alert fatigue. Analysts waste time correlating alerts from different tools, determining which one is most accurate, and trying to build a coherent picture of what’s actually happening.
Tool consolidation has become a major focus for SOC leaders. Rather than adding more point solutions, mature organizations look for platforms that address multiple use cases. They ruthlessly evaluate whether new tools provide genuinely new capabilities or just duplicate existing ones. They prioritize integration and automation to reduce manual work.
A good rule of thumb: before adding a new tool, ask whether the problem could be solved by better using or integrating tools you already have. Could better SIEM correlation rules replace a specialized detection tool? Could SOAR automation eliminate the need for another analyst console? Could tuning your XDR platform provide missing visibility instead of a new network monitoring tool?
A modern SOC needs focus on tool effectiveness and integration over sheer quantity. Build a solid foundation with core technologies, integrate them well, ensure your team can use them effectively, and only then consider adding specialized tools for specific gaps.