Table of Contents
If your security operations center (SOC) is struggling to keep up with alerts, experiencing high analyst turnover, missing critical threats, or facing mounting backlogs of unresolved incidents, your SOC is likely overwhelmed. These warning signs indicate your team lacks the resources, coverage, or capacity to effectively protect your organization from cyber threats—a dangerous situation that leaves security gaps attackers can exploit.
An overwhelmed SOC isn’t just an operational inconvenience—it’s a serious security risk. When your analysts are drowning in alerts, working excessive overtime, or leaving for less stressful positions, threats slip through undetected and incidents go unresolved. Understanding the warning signs helps you recognize when your SOC needs help before a breach occurs.
Below, we’ll explore the key indicators your SOC is overwhelmed, what normal operations should look like, and what you can do to address the problem before it compromises your security posture.
What happens when a SOC is understaffed?
When a SOC lacks adequate staffing, the consequences cascade through every aspect of security operations, creating vulnerabilities attackers can exploit.
Alert fatigue becomes the norm. Without enough analysts to handle the volume of security alerts, your team starts taking shortcuts. They spend less time investigating each alert, miss important context, and eventually become desensitized to warnings. Critical threats get classified as false positives simply because no one has time to investigate properly.
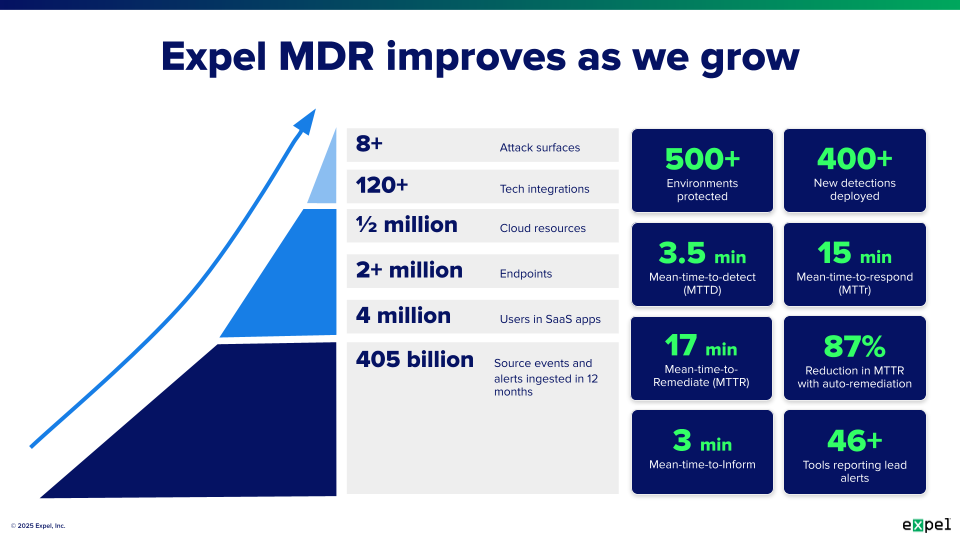
Response times increase dramatically. Understaffed SOC teams can’t respond to incidents as quickly as necessary. What should be a 30-minute containment action stretches to hours or days because analysts are juggling multiple simultaneous incidents. Meanwhile, industry-leading MDR providers like Expel maintain a 17-minute mean time to respond on high and critical incidents. Every minute of delay gives attackers more time to move laterally through your network, exfiltrate data, or deploy ransomware.
Coverage gaps emerge. True 24×7 security operations require at least eight to ten full-time analysts working in shifts. Understaffed teams often resort to on-call rotations, leaving nights and weekends with minimal or no coverage. Sophisticated attackers know this and deliberately strike during off-hours when they’re less likely to be detected.
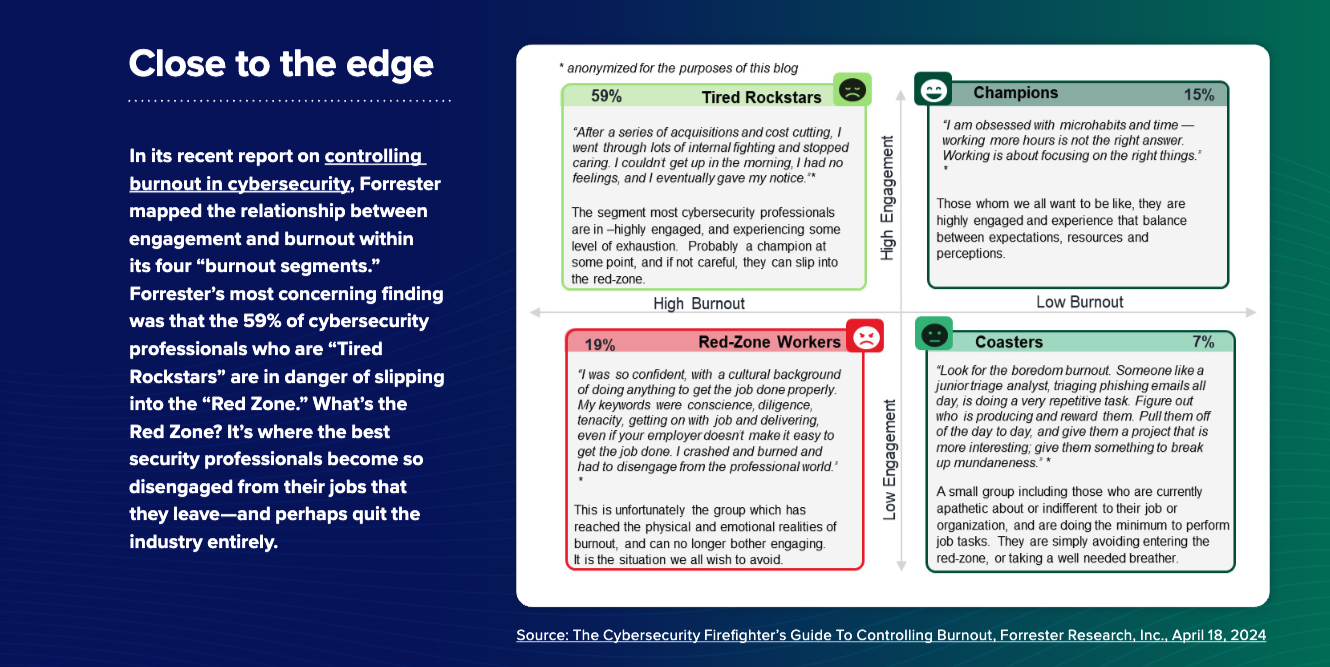
Burnout accelerates turnover. Security analysts facing overwhelming workloads, constant pressure, and impossible expectations burn out quickly. When they leave, you lose institutional knowledge and spend months recruiting and training replacements—during which time your SOC becomes even more understaffed. This creates a vicious cycle that’s difficult to break.
Strategic initiatives stall. An overwhelmed SOC has no capacity for proactive security improvements. Threat hunting, security architecture reviews, and process optimization get postponed indefinitely because the team is consumed by reactive alert triage and incident response.
Compliance requirements slip. Many regulatory frameworks require timely incident response and continuous monitoring. Understaffed SOCs struggle to meet these obligations, putting your organization at risk of compliance violations and potential fines.
The most dangerous consequence: threats go undetected. When your SOC is overwhelmed, sophisticated attacks requiring careful investigation and analysis simply aren’t caught until it’s too late.
How many security analysts do I need?
The number of security analysts your SOC needs depends on several factors, but there are industry benchmarks that provide useful guidance.
Minimum for 24×7 coverage: To maintain true round-the-clock security operations, you need at least eight to ten full-time analysts. This accounts for three eight-hour shifts per day, plus coverage for vacations, sick days, training, and inevitable turnover. Many organizations underestimate this requirement and try to maintain 24×7 operations with fewer analysts, leading to burnout and coverage gaps.
Role specialization matters: Effective SOCs need different skill levels. You’ll need tier-one analysts for alert triage, tier-two analysts for investigations, tier-three specialists for complex forensics, and threat hunters for proactive detection. Each role requires different expertise and compensation levels.
Organization size considerations: Industry guidelines suggest approximately one security analyst per 1,000 employees as a rough baseline, though this varies significantly based on your industry, threat profile, and technology complexity. Healthcare organizations and financial institutions typically require higher ratios due to regulatory requirements and elevated threat levels.
Technology stack complexity: Organizations with diverse, complex technology environments—multiple cloud providers, legacy systems, IoT devices, and specialized applications—need more analysts to monitor and protect all these attack surfaces effectively.
Alert volume drives staffing: If your security tools generate thousands of alerts daily, you need enough analysts to triage them properly. A single analyst can typically handle 20-30 alerts per shift if they’re investigating thoroughly, though this number varies based on alert quality and complexity.
The talent shortage reality: Even if you determine you need ten analysts, recruiting and retaining qualified security professionals is extremely challenging. Competition for talent is fierce, salaries are high, and turnover rates in security operations run 15-25% annually.
This is why many organizations turn to MDR services. Rather than trying to hire, train, and retain a full SOC team, they gain access to experienced analysts through a subscription service providing equivalent or better coverage at a fraction of the cost.
What’s a normal alert volume for a SOC?
Alert volume varies dramatically based on your organization’s size, security tools, and tuning maturity—but understanding what’s normal helps you recognize when your SOC is facing unreasonable demands.
Typical enterprise alert volumes: Mid-sized organizations (1,000-5,000 employees) commonly see 1,000-5,000 security alerts daily across all their tools. Larger enterprises may see 10,000+ alerts per day. However, the vast majority—often 90-95%—are false positives or low-severity events that don’t require immediate action.
The false positive problem: Poorly tuned security tools generate enormous amounts of noise. If your SIEM, EDR, and other security platforms aren’t properly configured for your environment, they’ll flag normal business activities as suspicious. Your analysts waste time investigating benign events instead of focusing on real threats.
What actually needs investigation: Of those thousands of daily alerts, typically only 50-200 require human investigation. Even fewer—perhaps 5-20—represent genuine security incidents requiring response. The challenge is efficiently separating signal from noise.
Alert-to-incident ratio matters: A healthy SOC should see a high alert-to-false-positive ratio, meaning most alerts get quickly dismissed after minimal review. If your team is spending substantial time investigating benign alerts, your tools need better tuning.
Volume trends over time: Alert volume shouldn’t remain constant. As your SOC matures, you should see decreasing false positives through better detection tuning and increasing efficiency in alert triage. If your alert volume keeps climbing without corresponding improvement in detection quality, something’s wrong.
Comparison to MDR providers: Mature MDR services use powerful automation to filter out noise, detecting suspicious activity and prioritizing alerts for real incidents. They achieve much higher efficiency than typical in-house SOCs because they’ve refined their detection logic across hundreds of customer environments.
If your analysts are triaging hundreds of alerts per shift with no time for investigation, or if your backlog of unreviewed alerts keeps growing, your SOC is overwhelmed by volume it can’t handle.
How do I measure SOC effectiveness?
Measuring SOC effectiveness requires looking beyond activity metrics to focus on outcomes that actually indicate security performance.
Key performance indicators that matter:
Mean time to detect (MTTD): How quickly does your SOC identify a genuine security incident after it occurs? Industry averages hover around several days or weeks, but mature security operations should detect threats within hours. If your MTTD is measured in days, you’re giving attackers too much time to cause damage.
Mean time to respond (MTTR): Once you’ve detected a threat, how long until you contain it? Delayed response times directly correlate with increased damage, giving attackers more opportunity to escalate their access. High-performing teams respond within minutes or hours, not days.
Alert closure rate: What percentage of your alerts get investigated and closed within SLA timeframes? A growing backlog of unresolved alerts indicates capacity problems.
False positive rate: What percentage of your alerts turn out to be false alarms? High false positive rates (above 90%) suggest poor tool tuning and wasted analyst effort.
Detection coverage: Are you monitoring all your critical attack surfaces—endpoints, network, cloud, email, identity systems? Gaps in coverage mean blind spots attackers can exploit.
Analyst utilization: How much time do your analysts spend on high-value activities like threat hunting and investigation versus low-value alert triage? If 80%+ of their time goes to triage, you’re not operating efficiently.
Turnover rate: Are you retaining analysts or constantly recruiting replacements? High turnover (above 20% annually) indicates organizational problems—typically overwork and burnout.
Escalation patterns: How many incidents require escalation to senior analysts or external help? Frequent escalations suggest insufficient expertise or complexity beyond your team’s capabilities.
Self-assessment framework: If you’re experiencing three or more of these warning signs, your SOC is likely overwhelmed and needs intervention:
- Mean time to respond exceeds 4 hours on critical incidents
- More than 25% of alerts go uninvestigated due to backlog
- False positive rate exceeds 90%
- Analyst turnover exceeds 20% annually
- Regular coverage gaps during nights/weekends
- No capacity for proactive threat hunting
- Compliance reporting consistently late or incomplete
- Mounting backlog of unresolved incidents
- Analysts working regular overtime to keep up
- Recent security incidents were discovered by external parties rather than your SOC
This is a sign your security operations need augmentation, additional resources, or alternative approaches like MDR to supplement your team’s capabilities.
Can automation solve SOC overload?
Automation is part of the solution but not a complete answer to SOC overload. Understanding what automation can and can’t do helps set realistic expectations.
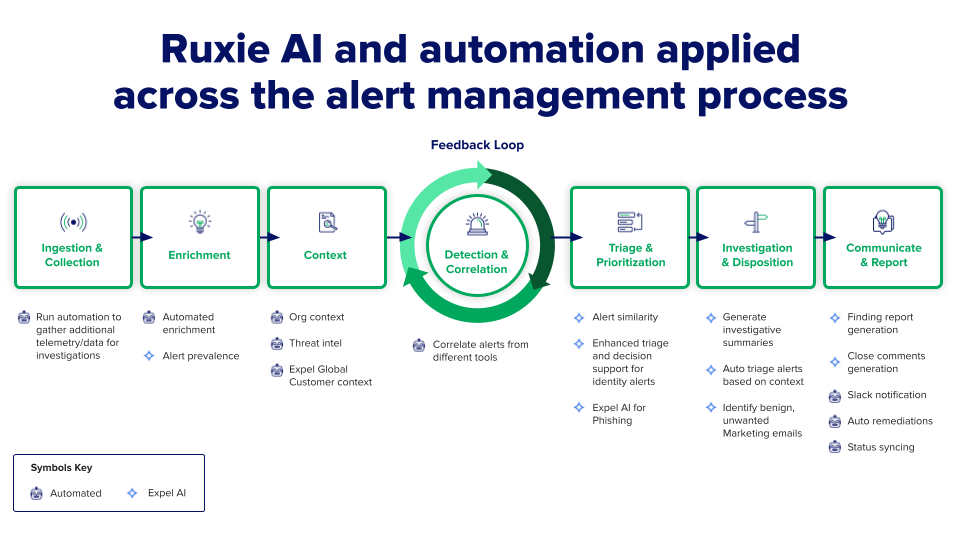
What automation does well: Security orchestration and automation platforms excel at repetitive, well-defined tasks. They can automatically enrich alerts with threat intelligence, block known-malicious IP addresses, isolate compromised endpoints, and execute standard response playbooks. This frees analysts from routine tasks to focus on complex investigations requiring human judgment.
What automation can’t replace: Human analysts provide context, intuition, and creative problem-solving automation lacks. Sophisticated attacks often involve novel techniques, legitimate tools used maliciously, or subtle behavioral anomalies requiring human expertise to recognize. Automation can assist but not replace the need for skilled security professionals.
The tuning challenge: Automation only works well when properly configured for your environment. Poorly tuned automation creates its own problems—automatically blocking legitimate business activities, contributing to missed threats, or generating new categories of false positives. Maintaining effective automation requires ongoing analyst attention.
Automation in MDR services: Leading MDR providers combine advanced automation with human expertise. Their platforms use AI and automation to filter out noise, detect suspicious activity, and prioritize alerts, while experienced analysts investigate anything requiring human judgment. This hybrid approach achieves better results than either automation or humans alone.
If your SOC is overwhelmed, implementing automation helps but won’t solve the fundamental problem if you lack adequate staffing, expertise, or coverage. Automation amplifies what your team can accomplish—it doesn’t replace the need for a properly resourced security operations capability.
Strategic considerations: Rather than trying to automate your way out of SOC overload, many organizations find partnering with an MDR provider delivers better outcomes. MDR services bring both advanced automation technology and the human expertise needed to use it effectively, providing immediate relief for overwhelmed teams.
Taking action when your SOC is overwhelmed
Recognizing your SOC is overwhelmed is the first step. Here’s what you can do about it:
Immediate relief options: If you’re experiencing a lack of coverage during nights, weekends, or holidays, consider augmenting your team with MDR services that can handle tier-one triage and initial response while your internal analysts focus on strategic priorities. This provides immediate capacity and sidesteps recruitment challenges without lengthy hiring processes.
Tune your tools: Work to reduce false positives through better detection rules and alert thresholds. Every false positive eliminated frees analyst time for real threats.
Prioritize ruthlessly: Not every alert requires immediate investigation. Establish clear prioritization criteria based on actual risk to your business and focus resources on what matters most.
Address retention: If analysts are leaving due to burnout, no amount of automation will help. Tackle overtime issues head-on, improve work-life balance, provide growth opportunities, and ensure reasonable workloads to retain talent.
The goal isn’t perfection—it’s sustainable security operations effectively protecting your organization without burning out your team. If you’re seeing multiple warning signs of SOC overload, it’s time to explore alternative approaches before the situation leads to a security incident.