Table of Contents
The main types of security operations centers are in-house SOCs, managed SOCs (or outsourced SOCs), and hybrid SOCs. Each model offers different approaches to staffing, resource allocation, and operational control, with varying levels of 24×7 coverage and security expertise. Your choice depends on factors like budget, internal resources, security maturity, and how hands-on you want to be with daily security operations.
Types of SOC: Understanding your options
When you’re building or evolving your security operations, the type of SOC you choose becomes one of your most significant decisions. It impacts everything from your annual security budget to how quickly you can respond to threats, and even how much strategic work your internal team can focus on.
There are three primary SOC structures organizations typically consider. An in-house SOC means you’re building and operating everything yourself—hiring analysts, deploying technology, and managing operations internally. A managed SOC (sometimes called an outsourced SOC or SOC-as-a-service) involves partnering with an external provider who handles security operations on your behalf. A hybrid SOC model combines both approaches, maintaining some internal capabilities while outsourcing other security functions to a managed service provider.
Each approach has distinct advantages and trade-offs in terms of cost, expertise, and operational flexibility.
In-house SOC vs. managed SOC: Key differences
The fundamental difference between an in-house SOC and a managed SOC comes down to ownership and control. With an in-house SOC, you’re responsible for recruiting security analysts, purchasing and maintaining security tools, and running round-the-clock operations. According to research, building a competent in-house SOC typically costs well over a million dollars annually—just to reach “good enough.”
A managed SOC service flips this model entirely. Instead of hiring your own team, you subscribe to a service providing experienced analysts, proven processes, and integrated technology. The managed security services provider (MSSP) handles monitoring, alert triage, threat investigation, and incident response on your behalf. You’re essentially getting a full security operations capability without the overhead of building and maintaining it yourself.
The staffing model represents one of the clearest distinctions. An internal security team requires recruiting specialized talent in a competitive market, then training and retaining those analysts through a 24×7 rotation schedule. Managed SOC services come with analysts already trained and available around the clock. These teams also benefit from cross-customer threat intelligence—when they encounter a new attack technique at one organization, they can immediately apply the knowledge across their entire customer base.
Technology ownership differs significantly too. In-house SOCs require you to license, deploy, configure, and maintain security tools like SIEM platforms, EDR solutions, and threat intelligence feeds. With managed SOC services, the provider brings their own technology stack that integrates with your environment, often through APIs rather than agents. This means you can start getting 24×7 coverage in hours rather than months.
Cost structure is another major differentiator. In-house SOCs involve fixed costs—salaries, benefits, training, infrastructure, and tool licenses—regardless of actual security activity. Managed SOC services typically operate on subscription pricing, making costs more predictable and generally lower than building equivalent in-house capabilities. The resource allocation question becomes: do you want to invest heavily in building security operations expertise, or do you want your internal team focused on strategic security priorities unique to your business?
SOC operational models: How different structures work
Beyond the basic in-house versus outsourced decision, SOC operational models vary in how they’re structured and how they deliver security capabilities. Understanding these models helps you determine which approach aligns with your organization’s needs.
The traditional in-house model operates like any other business function you build internally. You establish a security operations center—whether it’s a physical or virtual SOC—and staff it with your own security team. These analysts use your security tools to monitor environments, analyze activity, conduct triage on alerts, and respond to incidents. The advantage is complete control over operations, but you’re also responsible for every aspect of running the operation, from shift scheduling to technology maintenance to ongoing training.
The fully managed model hands over security operations to an external provider. Organizations who don’t have the time, staff, or budget to operate an in-house SOC can gain complete security operations coverage through this approach. The managed SOC provider handles everything from monitoring and detection to investigation and response, operating on a subscription basis. This model works particularly well for organizations where security isn’t a core competency and building internal expertise doesn’t make strategic sense.
A co-managed SOC model sits between these extremes. In this operational model, you maintain some internal detection and response capabilities while augmenting them with managed security services. For example, your internal team might handle security architecture and policy while the managed provider covers 24×7 monitoring and first-response activities. The co-managed approach recognizes many organizations want to keep some security functions in-house while getting expert help with the most resource-intensive operations.
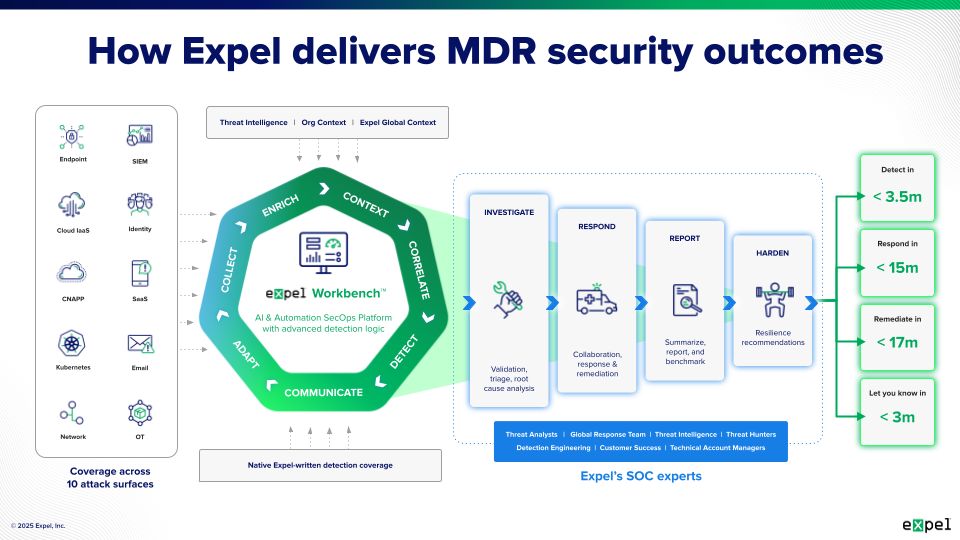
The SOC-as-a-service model deserves special mention because it represents how modern managed SOCs typically operate. Rather than traditional outsourcing where the provider takes over and you lose visibility, SOC-as-a-service provides cloud-based security operations that integrate directly with your existing technology. You maintain full visibility into what the SOC team is doing—many providers even offer real-time collaboration through tools like Slack or Teams—while they handle the heavy lifting of alert triage, threat investigation, and remediation guidance.
Virtual SOC vs. physical SOC: Location matters less than capability
The physical versus virtual SOC distinction has become less meaningful in recent years, especially following shifts toward remote work and cloud-based operations. What matters more is the capability the SOC delivers, not whether there’s a physical room with analysts and monitors.
A physical SOC is what most people picture: a centralized facility where security analysts work together, often with wall-mounted displays showing security dashboards and network activity. These command center-style operations centers were once considered essential for effective security monitoring. Organizations built dedicated spaces, invested in physical infrastructure, and required analysts to work on-site for collaboration and rapid response.
A virtual SOC operates without a centralized physical location. Analysts might work from different offices, different time zones, or from home. The SOC functions through cloud-based platforms, communication tools, and remote access to security systems. Whether the modern security operations center is a physical or virtual space, the purpose remains the same: managing monitoring tools, analyzing activity, conducting triage on alerts, collaborating on incident response, and mitigating threats.
From a practical standpoint, virtual SOCs offer several advantages. They’re more cost-effective since you’re not maintaining dedicated physical space. They provide better access to talent since you can recruit analysts regardless of location. And they’re often more resilient—there’s no single point of failure if a physical location becomes unavailable.
Managed SOC providers typically operate as virtual SOCs from the customer’s perspective. The provider might have physical operations centers where their analysts work, but your relationship with them is entirely virtual. They connect to your security tools remotely, communicate through digital channels, and deliver security operations without requiring any on-site presence.
The key question isn’t whether your SOC is physical or virtual—it’s whether the operational model provides the visibility, expertise, and 24×7 coverage your organization needs.
Hybrid SOC model: Balancing internal capabilities with managed services
The hybrid model has emerged as a popular middle ground for organizations who want some internal security operations expertise while also leveraging external resources. This approach acknowledges a practical reality: you might have strong internal security talent but struggle with round-the-clock coverage, or you might have solid detection capabilities but need help with response.
In a hybrid SOC model, you maintain certain security functions in-house while outsourcing others to managed security services. The division of responsibilities varies based on organizational needs. Some organizations keep security strategy, architecture, and policy internally while outsourcing monitoring and first-line response. Others maintain their own threat hunting and strategic analysis while using a managed provider for alert triage and routine incident handling.
According to our experience, a hybrid model works well when there’s a deep collaborative relationship between the organization’s internal security team and the managed SOC provider. The internal team focuses on security priorities unique to the business—things like application security, security architecture, or compliance requirements—while the managed team handles the resource-intensive work of 24×7 monitoring, alert investigation, and routine incident response.
Resource allocation becomes more efficient in a hybrid model. Rather than trying to build full 24×7 coverage internally—which requires hiring enough analysts to cover all shifts, weekends, and holidays—you can staff a smaller internal team to work during business hours and rely on managed services for extended coverage. This approach addresses one of the biggest challenges in security operations: maintaining continuous monitoring without burning out a limited team.
The hybrid model also provides flexibility as your security program matures. Organizations often start with a fully managed approach and gradually build internal capabilities over time, transitioning to a hybrid model as they develop expertise and resources. Conversely, some organizations begin with in-house operations but shift to hybrid models when they realize the operational burden of running 24×7 security operations.
Technology integration matters significantly in hybrid models. The managed provider needs to work with your existing security tools rather than requiring you to replace them. Modern managed SOC services connect via APIs and integrate with your current security stack—including SIEM, EDR, cloud security tools, and network monitoring—so you maintain your technology investments while gaining enhanced operational capability.
Different SOC structures: Choosing what works for your organization
Selecting the right SOC structure isn’t just about budget—it’s about matching security operations to your organization’s maturity, resources, and strategic priorities. Each structure serves different organizational contexts and constraints.
Consider an in-house SOC when security is truly core to your business operations and you have both the budget and the ability to attract specialized talent. Organizations in highly regulated industries, those handling extremely sensitive data, or companies where security is a competitive differentiator might benefit from full internal control. However, be realistic about costs. Building even a basic 24×7 capability requires significant investment in people, process, and technology, with ongoing expenses that don’t decrease over time.
A fully managed SOC makes sense when security operations aren’t your core competency, when you’re facing the challenges of hiring and retaining security talent, or when you need to get comprehensive security coverage quickly. Organizations experiencing rapid growth, those with limited security budgets, or companies who want their internal team focused on strategic work rather than alert triage often find managed services the most practical choice. The subscription model makes costs predictable, and you gain immediate access to experienced analysts who bring knowledge from protecting hundreds of other organizations.
Co-managed or hybrid structures work well for organizations with some internal security capability but recognize gaps in coverage or expertise. Maybe you have a strong internal team that can’t staff weekends. Perhaps you excel at security strategy but struggle with the operational burden of investigating alerts. Or you might need specialized expertise in areas like cloud security or threat hunting that’s difficult to hire for. The hybrid approach lets you maintain control over strategic security decisions while augmenting your capabilities where you need help most.
Virtual SOC arrangements—whether internal or managed—offer flexibility and often cost savings compared to maintaining physical operations centers. For many organizations, the question isn’t whether to go virtual or physical but rather how to structure effective security operations regardless of physical location.
When evaluating different SOC structures, consider these factors:
Staffing model implications: Can you recruit, train, and retain security analysts for 24×7 operations? What’s the local talent market like? How quickly do you need coverage?
Cost structure alignment: Do you prefer predictable subscription costs or are you comfortable with the fixed overhead of internal operations? What’s your budget for security operations over the next three-to-five years?
Expertise depth requirements: Do you need highly specialized knowledge in specific areas? Can you develop and maintain that expertise internally? How important is exposure to cross-customer threat intelligence?
Operational model preferences: How much control do you need over day-to-day operations? Are you comfortable with a collaborative partnership model? Do you want to see everything the SOC team is doing?
Technology integration: What security tools do you already have? Do you need a provider who works with your existing stack? Are you willing to adopt new technology as part of a managed service?
Many organizations find their SOC structure needs to evolve over time. You might start with a managed SOC to get quick coverage while you build internal capabilities, then transition to a hybrid model. Or you might realize running in-house operations is spreading your team too thin and decide to shift to a managed approach so your analysts can focus on more strategic work.
The “right” SOC structure is the one that delivers the security coverage you need while aligning with your resources, expertise, and business priorities. There’s no one-size-fits-all answer—what works for a financial services company might not work for a healthcare provider or a technology startup.
Frequently asked questions
What’s the difference between a managed SOC and MDR? Managed SOC services and managed detection and response (MDR) serve similar purposes but differ in scope. A managed SOC typically encompasses all security operations functions, while MDR specifically focuses on threat detection and response capabilities. MDR providers deliver remotely operated security operations that rapidly detect, analyze, investigate, and actively respond to threats. In practice, many modern managed SOC providers offer MDR as part of their services.
How much does it cost to build an in-house SOC? Building a competent in-house SOC typically costs well over a million dollars annually. Costs include analyst salaries (you need enough people to cover 24×7 shifts), security tool licenses, infrastructure, ongoing training, and management overhead. The exact amount depends on the capability level you’re trying to achieve—a basic SOC costs less than a mature operation with advanced detection and hunting capabilities. Expel’s analysis breaks down these costs in detail based on different SOC maturity levels.
Can I switch between SOC models over time? Yes, organizations frequently evolve their SOC structure as their security program matures and needs change. Many start with managed services to get quick coverage, then move to hybrid models as they build internal expertise. Others begin with in-house operations but shift to managed or hybrid approaches when operational demands become overwhelming. The key is choosing technology and processes that allow for flexibility as your program evolves.
What’s the advantage of a co-managed SOC approach? A co-managed SOC lets you maintain internal security expertise and control over strategic decisions while getting external help with resource-intensive operations like 24×7 monitoring and alert triage. This approach addresses common challenges like analyst burnout, coverage gaps during off-hours, and the difficulty of maintaining expertise across all security domains. Your internal team can focus on what’s unique to your business while the managed provider handles routine operations.
How quickly can a managed SOC start protecting my environment? Managed SOC providers that connect via APIs rather than deploying agents can often begin monitoring your environment within hours to days. According to Expel’s approach, they connect remotely to security tools you already own and start providing coverage almost immediately. This is significantly faster than building an in-house SOC, which can take months to staff, equip, and operationalize.