Table of Contents
You can define MDR, or managed detection and response, as a cybersecurity service providing organizations with 24×7 monitoring, threat detection, and incident response capabilities delivered by an external team of security experts. In simple terms, MDR is a way for companies to outsource their security operations to specialists who watch for threats around the clock, investigate suspicious activity, and take action to stop attacks before they cause damage.
Another way to define MDR is like having a professional security guard service for your digital infrastructure—except instead of patrolling a physical building, these experts are continuously monitoring your networks, endpoints, and cloud environments for signs of cyber threats. They combine advanced technology with human expertise to catch what automated tools might miss and respond faster than most in-house teams could manage on their own.
For many organizations, especially those without the resources to build and staff their own security operations center, MDR provides enterprise-level protection without the enterprise-level price tag or staffing headaches.
What is managed detection and response?
Managed detection and response is a comprehensive security service combining technology, threat intelligence, and human expertise to identify and neutralize cyber threats in real time. Unlike traditional security tools that simply alert you to potential problems, MDR services actually investigate those alerts, determine which ones represent genuine threats, and take direct action to contain and eliminate them.
The “managed” part means you’re outsourcing this critical function to a specialized provider with dedicated security analysts. The “detection” component involves continuously monitoring your environment for indicators of compromise, unusual behavior, or known attack patterns. And “response” means the team doesn’t just tell you about problems—they actively work to stop threats, contain incidents, and help you recover.
What makes MDR different from older managed security services is the emphasis on active response. Traditional managed security focused heavily on monitoring and reporting, essentially telling you “here’s what we found—now you deal with it.” Modern MDR providers take ownership of the response process, acting as an extension of your team to neutralize threats quickly.
A typical MDR service monitors multiple security layers across your organization. This includes endpoints like laptops and servers, network traffic, cloud workloads, email systems, and identity platforms. By watching all these areas simultaneously, MDR providers can spot attack patterns that might not be obvious when looking at just one security tool in isolation.
The service model usually works on a subscription basis, giving you access to a full SOC team without having to hire, train, and retain those specialists yourself. This is particularly valuable given the current cybersecurity talent shortage—skilled security analysts are expensive and hard to find, but MDR lets you benefit from their expertise without adding them to your payroll.
What does MDR mean in cybersecurity?
In the cybersecurity world, MDR represents a fundamental shift in how organizations approach threat management. The acronym stands for “managed detection and response,” but what it really means is a more proactive, outcome-focused approach to security.
Traditionally, companies bought security products—firewalls, antivirus software, intrusion detection systems—and hoped those tools would keep them safe. But modern cyber attacks are too sophisticated for tools alone. Attackers use social engineering, living-off-the-land techniques, and zero-day exploits automated systems often miss. MDR addresses this gap by putting experienced human analysts in the loop.
When security professionals talk about MDR, they’re referring to a service that provides continuous monitoring and active threat hunting across an organization’s entire environment. This isn’t just about waiting for alerts to fire—it’s about proactively searching for signs of compromise, investigating anomalies, and understanding the context behind security events.
The term also implies a partnership model. Your MDR provider becomes an extension of your security team, working closely with your IT staff to understand your unique environment, business priorities, and risk tolerance. They learn what’s normal for your organization so they can better spot what’s abnormal.
MDR fills a critical gap between prevention-focused tools and full-scale incident response services. Prevention is important, but no security is perfect—breaches happen. When they do, you need someone who can detect the intrusion quickly and respond before attackers can steal data, deploy ransomware, or cause other damage. That’s exactly what MDR delivers.
For security teams, MDR means access to capabilities they couldn’t build on their own: threat intelligence from across hundreds of customers, playbooks refined through thousands of investigations, and analysts who’ve seen every type of attack imaginable. It’s collective defense made practical.
How does managed detection and response work?
Managed detection and response operates through a combination of technology deployment, continuous monitoring, and expert analysis. Here’s how the typical MDR workflow unfolds:
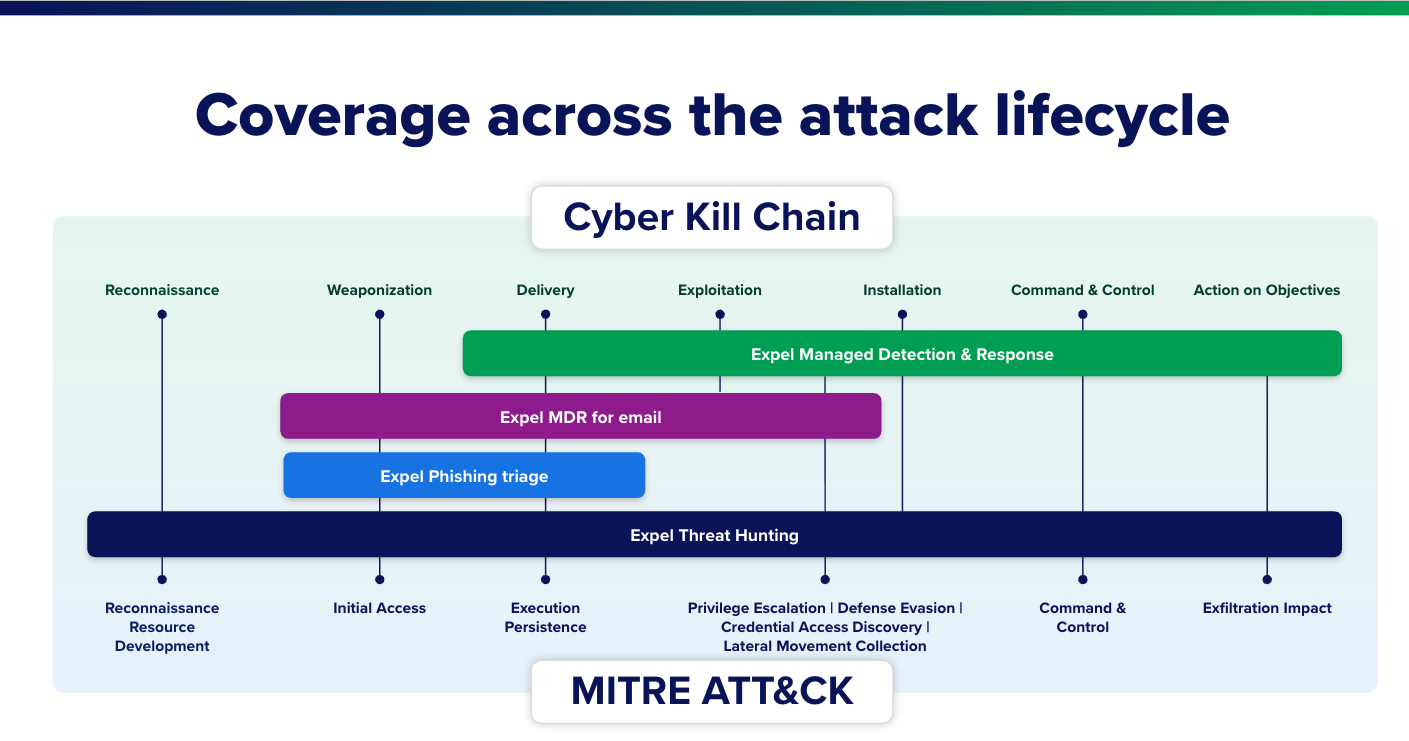
First, the MDR provider integrates with your existing security tools. This might include installing EDR (endpoint detection and response) agents on your computers and servers, connecting to your cloud platforms, integrating with your firewalls and network monitoring tools, and tapping into your email security systems. Some MDR providers like Expel don’t require any agents; they gain visibility purely through integrations like API connections. Either way, the goal is comprehensive visibility—the provider needs to see what’s happening across your entire digital infrastructure.
Once integrated, the monitoring begins. The MDR provider’s technology continuously collects security telemetry—logs, network traffic data, endpoint behavior, user activity, and more. This generates an enormous amount of information, far more than any human could manually review. Advanced analytics, machine learning models, and correlation engines process this data stream, looking for patterns to indicate potential threats.
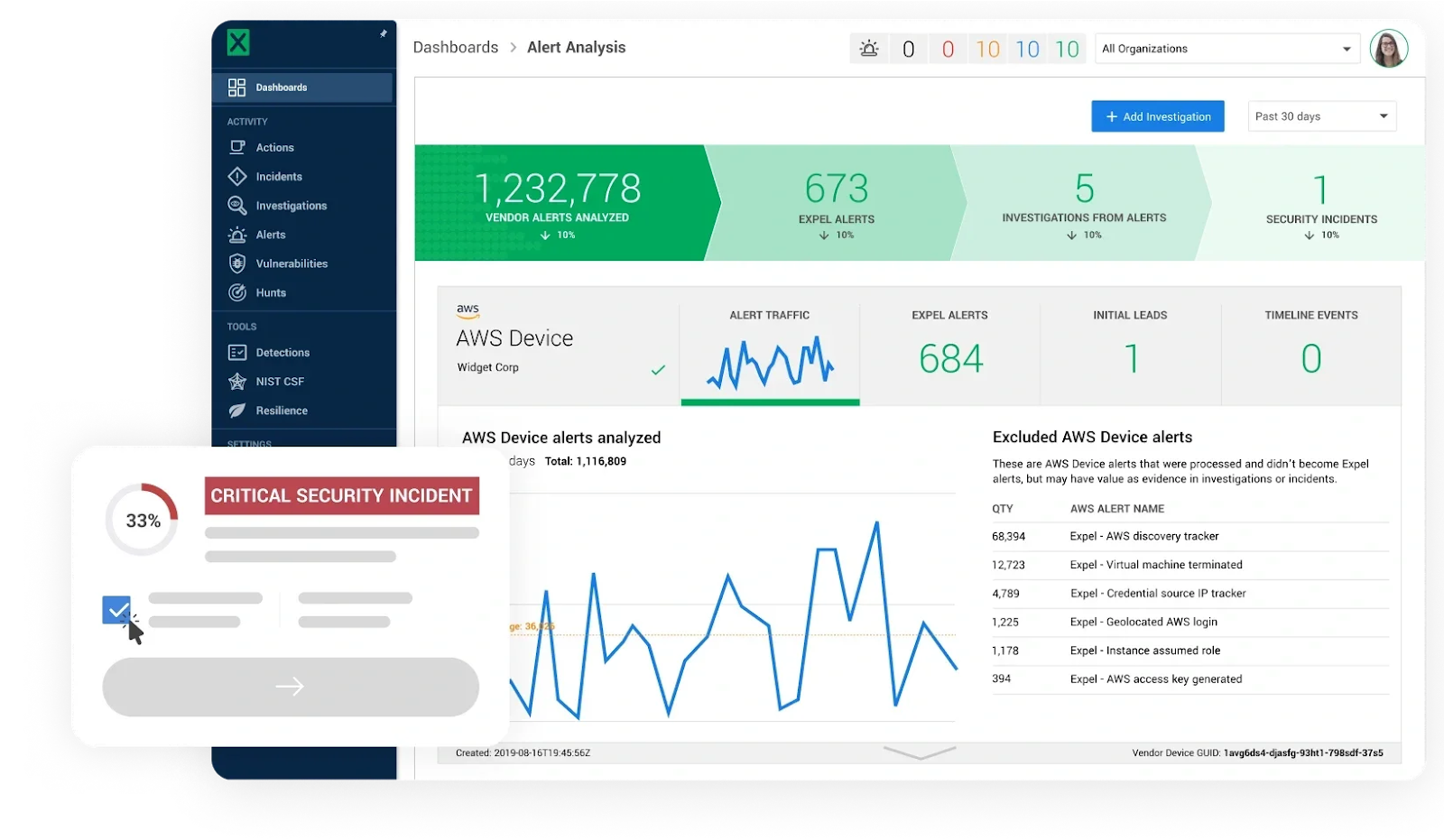
When something suspicious appears—maybe a user account is accessing files it normally doesn’t touch, or an endpoint is communicating with a known malicious IP address—the system generates an alert. An MDR like Expel actually builds custom detections to generate an alert when suspicious activities occur in sequence across different attack surfaces. These sorts of alerts limit the likelihood of false positives, since it’s not a single detection generating an alert but, rather, multiple detections happening at once. Here’s where MDR truly differentiates itself: instead of just forwarding an alert to you, the provider’s security analysts investigate it.
The analyst examines the alert in detail, gathering context from multiple sources. They look at what happened before and after the suspicious activity, check whether similar patterns are appearing elsewhere in your environment, and compare the behavior against threat intelligence databases. This investigation separates real threats from false positives—and many alerts turn out to be benign.
If the analyst determines a genuine threat exists, they move into response mode. Depending on your service agreement, this might mean isolating the affected system from the network, killing malicious processes, blocking threatening IP addresses, or disabling compromised user accounts. Some MDRs offer different auto remediation actions to help take these actions instantly or near-instantly. The goal is containment—stopping the attack from spreading while preserving evidence for further investigation.
Throughout this process, the MDR team keeps you informed. You receive notifications about confirmed incidents, what actions were taken, and what steps you need to complete. Some remediation activities require your involvement—like reimaging a compromised system or forcing a company-wide password reset—but the MDR team handles the security-specific work.
Beyond reactive response, quality MDR services include proactive threat hunting. Analysts periodically search through your environment for signs of threats that might have evaded automated detection. They develop hypotheses about how attackers might target your organization and test whether those attacks have already occurred unnoticed.
Explain MDR services
MDR services encompass several key capabilities working together to provide comprehensive security coverage. For many, these are also seen as the benefits of managed security services.
24×7 security operations: The most fundamental aspect of MDR is round-the-clock monitoring and response. Cyber attacks don’t happen only during business hours—in fact, many attackers deliberately strike on weekends and holidays when they know security teams are understaffed. MDR providers maintain follow-the-sun operations with analysts working in shifts to ensure someone is always watching your environment.
Alert triage and investigation: Modern security tools generate thousands of alerts. Most are false positives or low-severity events that don’t require immediate action. MDR analysts review these alerts, investigate the meaningful ones, and spare your team from alert fatigue. They apply their expertise to distinguish real threats from noise, dramatically reducing the volume of incidents you need to handle internally.
Incident response: When a genuine threat is detected, MDR teams spring into action. They follow established playbooks to contain the threat, eliminate the attacker’s presence, and prevent further damage. This includes technical actions like isolating infected systems, as well as coordination activities like notifying stakeholders and documenting the incident.
Threat hunting: Proactive hunting involves looking for threats automated tools missed. Hunters develop hypotheses based on the latest threat intelligence, attacker tactics, and vulnerabilities in your environment. They then search your data for evidence these attacks have occurred. This proactive approach catches sophisticated attackers who evade traditional detection methods.
Threat intelligence: MDR providers maintain extensive threat intelligence capabilities. They track emerging threats, analyze attack trends across their customer base, and incorporate this intelligence into their detection strategies. When a new ransomware variant appears or a novel attack technique emerges, MDR customers benefit from collective defense—insights from one customer’s incident help protect everyone else.
Security expertise: Perhaps the most valuable aspect of MDR services is access to experienced security professionals. These analysts have investigated thousands of incidents and understand attacker behavior intimately. They bring this expertise to your organization without you needing to recruit, hire, and retain them as employees.
Continuous improvement: Quality MDR providers regularly tune their detections based on your environment. As they learn what’s normal for your organization, they adjust thresholds, create custom detection rules, and reduce false positives. Over time, the service becomes increasingly tailored to your specific needs.
Reporting and metrics: MDR services typically include regular reporting on security events, threats detected, response actions taken, and overall security posture. These reports help leadership understand the value of the service and identify areas for improvement.
Different MDR providers structure their services differently, but these core capabilities remain consistent across quality offerings.
MDR definition for security teams
For security professionals evaluating MDR solutions, understanding the precise definition helps clarify what to expect from these services.
From a technical standpoint, MDR is a managed security service providing outsourced threat detection, investigation, validation, and response capabilities across an organization’s technology environment. It represents an evolution beyond traditional managed security service providers (MSSPs), which primarily focused on managing security devices and monitoring logs.
The defining characteristics of true MDR include:
Active response authority: Unlike services that only alert you to threats, MDR providers have the authority and capability to take direct action. They can isolate systems, block network traffic, disable accounts, and execute other containment measures without waiting for your approval for every action. This is typically governed by a response playbook you agree upon during onboarding.
Human-driven analysis: While MDR services use plenty of automation and machine learning, human analysts remain central to the process. They provide the context, intuition, and creative thinking needed to catch sophisticated attacks purely automated systems miss.
Outcome-focused service model: MDR providers are measured on outcomes—threats detected, incidents contained, time to respond—not just on activity metrics like number of logs collected or alerts generated. This aligns the provider’s incentives with your actual security needs.
Technology-agnostic approach: Quality MDR services work with your existing security stack rather than requiring you to rip and replace everything. They integrate with whatever EDR, SIEM, firewall, or cloud security tools you already use, though they may recommend specific technologies for gaps in your coverage.
Continuous improvement mindset: MDR isn’t a “set it and forget it” service. Providers continuously tune detections, update response playbooks, and adapt to changes in your environment and the threat landscape.
For security teams, MDR provides leverage. Instead of trying to staff a 24×7 security operations center internally—which requires at least eight to ten full-time analysts to maintain coverage—you gain access to an entire team for a fraction of the cost. This lets smaller security teams focus on strategic initiatives, security architecture, and risk management rather than being consumed by daily alert triage and incident response.
MDR also provides a depth of expertise that’s difficult to build internally. Your provider’s analysts investigate incidents across dozens or hundreds of customers, giving them pattern recognition abilities no single-company SOC could develop. When they encounter a novel attack technique at Customer A, they immediately know what to look for across their entire customer base, including your organization. When MDR is done right, all of these features become benefits of managed security services.
What are the benefits of managed detection and response?
Organizations adopt MDR services for numerous compelling reasons, each addressing real challenges in modern cybersecurity:
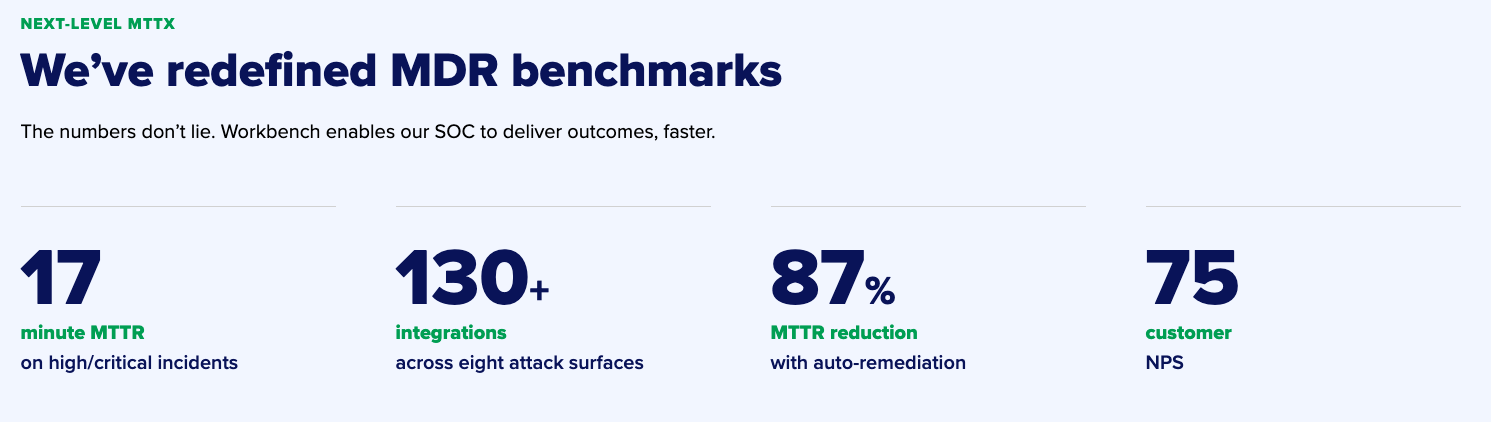
Faster threat detection: On average, attackers dwell in victim networks for weeks or months before being discovered. MDR dramatically compresses this “dwell time” by continuously monitoring for threats and proactively hunting for signs of compromise. Many MDR providers detect and contain threats within minutes or hours rather than weeks.
Reduced security team burden: Alert fatigue is real. Security teams drowning in false positives often miss real threats hidden in the noise. MDR services filter out the false alarms and escalate only validated incidents, letting your internal team focus on confirmed threats and strategic security initiatives.
Access to scarce expertise: Finding, hiring, and retaining skilled security analysts is extremely difficult and expensive. The talent shortage means many organizations can’t build the security team they need. MDR provides instant access to experienced professionals without the recruitment challenges.
Cost-effective security operations: Building an in-house SOC requires significant investment—salaries for multiple analysts, expensive security tools, training programs, and ongoing operational costs. MDR delivers similar capabilities at a fraction of the cost, typically as a predictable monthly subscription.
Improved incident response: When breaches occur, speed matters. Every minute of delay gives attackers more time to steal data or deploy ransomware. MDR teams respond immediately, often containing threats before your internal team would even become aware of them.
Better work-life balance for security staff: Running 24×7 security operations internally means on-call rotations, weekend shifts, and holiday coverage—all of which contribute to burnout. MDR lifts this burden from your team, letting them work normal hours while still maintaining round-the-clock security coverage.
Collective defense benefits: Your MDR provider sees attack patterns across many customers. When they discover a new threat technique, they immediately apply that knowledge to protect all customers. You benefit from insights derived from thousands of investigations you’ll never see directly.
Scalability and flexibility: As your organization grows or your technology footprint changes, your MDR service scales with you. Adding new cloud environments or acquiring another company doesn’t require hiring more security staff—your MDR provider expands coverage as needed.
Compliance support: Many regulations require continuous security monitoring and incident response capabilities. MDR helps satisfy these requirements by providing documented evidence of your security controls and incident handling processes.
The bottom line: MDR lets organizations achieve security outcomes that would be impossible or prohibitively expensive to deliver internally. It’s not about replacing your security team—it’s about dramatically amplifying their effectiveness.
How is MDR different from traditional security tools?
Understanding the distinction between MDR and traditional security products helps clarify why many organizations are making the shift to managed services.
Traditional security tools—firewalls, antivirus software, intrusion detection systems—are defensive technologies you deploy and operate yourself. They’re products. You buy them, install them, configure them, and monitor them with your internal staff. These tools generate alerts when they detect something suspicious, but responding to those alerts is your responsibility.
MDR, by contrast, is a service that’s sometimes enhanced by its own proprietary technology. You’re not just buying more security technology—you’re engaging a team to operate security capabilities on your behalf. When your MDR provider detects a threat, they investigate and respond to it. You’re not managing the tool; you’re receiving the outcome.
This distinction matters practically. Deploying a traditional EDR tool gives you endpoint visibility and detection capabilities, but someone on your team needs to watch the console, review alerts, investigate suspicious activity, and take response actions. If that person is on vacation, sick, or simply overwhelmed with other work, threats can slip through.
With MDR, those functions are handled by your provider’s analysts. The technology might look similar—in fact, MDRs like Expel actually utilize the tools you’re already using —but the operational model is completely different. You’re buying results, not just capabilities.
Another key difference: traditional security tools operate independently. Your firewall doesn’t talk to your endpoint protection, which doesn’t talk to your email security. Each generates its own alerts based only on what it can see. Sophisticated attacks often span multiple systems, so seeing the full picture requires correlating data from all these sources—something most organizations struggle to do effectively.
MDR providers excel at this correlation. They ingest data from all your security tools and layer on additional telemetry from sources you might not have. Their analysts view your entire environment holistically, spotting attack patterns that wouldn’t be obvious when looking at any single tool in isolation.
Finally, traditional security tools require significant expertise to use effectively. Tuning detection rules, understanding what alerts mean, and knowing how to respond to different threat types demands deep security knowledge. MDR providers bring this expertise as part of the service, so you don’t need to develop it internally.
That said, MDR doesn’t replace traditional security tools—it enhances them. You still need firewalls, endpoint protection, and other defensive technologies. MDR just ensures those tools are monitored, managed, and acted upon by experienced professionals.
Related pages
- What does “good” look like for MDR service providers?
- Why is an MDR solution?
- What is MDR in cybersecurity?
- What’s the difference between MDR and a traditional SOC?