EXPEL MANAGED DETECTION AND RESPONSE (MDR)
The leader in managed detection and response services
MDR services that safeguard your cloud, Kubernetes, endpoints, SaaS environments, and more
Your managed detection and response challenges
Your security operations center (SOC) needs answers fast, but there are too many alerts, no context, no transparency into your tech, and you never have enough security experts to keep up, let alone measure anything or build resilience.
TOP-TIER MDR provider
Tech-driven managed detection and response services
Expel Managed Detection and Response (Expel MDR) is the industry-leading MDR service provider that delivers rapid detection and response, and helps you build cyber resilience.
Expel MDR quickly detects advanced threats across your tech (endpoint, cloud, Kubernetes, SaaS, network, SIEM, email, identity, and more) and human expertise collaborates with your team to verify the threat, take critical remediation actions, and provide a detailed report of what happened, where, when, and why in real-time.
Expel’s approach to MDR
WHAT YOU GET
Expel MDR key capabilities

24×7 SOC monitoring: Real-time alert investigation and triage with direct SOC-to-customer incident communications
AI and automation-powered detection coverage: Detection, context, tuning, prioritization, and correlation
Human-led Expel remediation guidance and response: Remediation and resilience recommendations

Threat research: Threat bulletins and on-demand investigations

Platform and technology: Detection, context, tuning, prioritization and correlation—powered by Expel Workbench™ automation and AI

Metrics and reporting: Detailed status and visibility on every alert plus reporting on how you’re improving over time

SIEM coverage: SIEM utilization for investigative context, out of the box rule coverage and more
Concierge service delivery: Complete partnership from onboarding to ongoing reviews
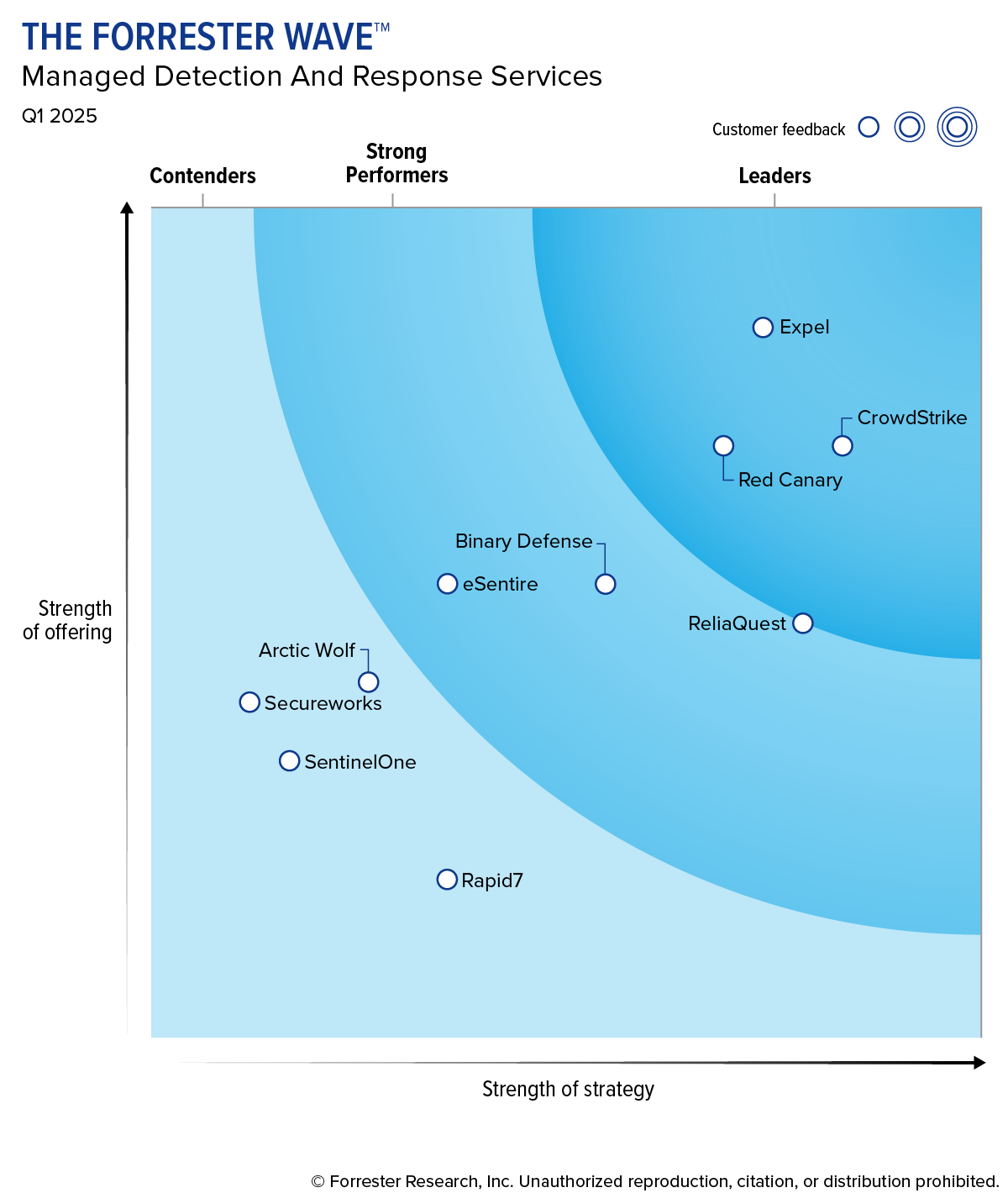
Analyst Report
Expel named a Leader in the Forrester Wave™ MDR services, Q1 2025
CUSTOMER TESTIMONIALS
90% of customers agree Expel MDR has improved their ability to identify security threats and risks*

An MDR can work alongside an internal team, becoming a trusted partner who speaks our language and allows us to focus on securing our infrastructure instead of chasing after the small stuff. Expel has become that extension of our team, making my team’s job easier.
See the story