Security operations · 6 MIN READ · BRITTON MANAHAN · NOV 10, 2021 · TAGS: MDR
We’re often asked about the biggest threats we see across the incidents we investigate for our customers. Where should security teams focus their efforts and budgets? To answer these questions, we’re sharing monthly reports on the top attack vectors, trends and resilience recommendations identified by our Security Operations Center (SOC). Our goal is to translate the security events we’re detecting into a security strategy for your org.
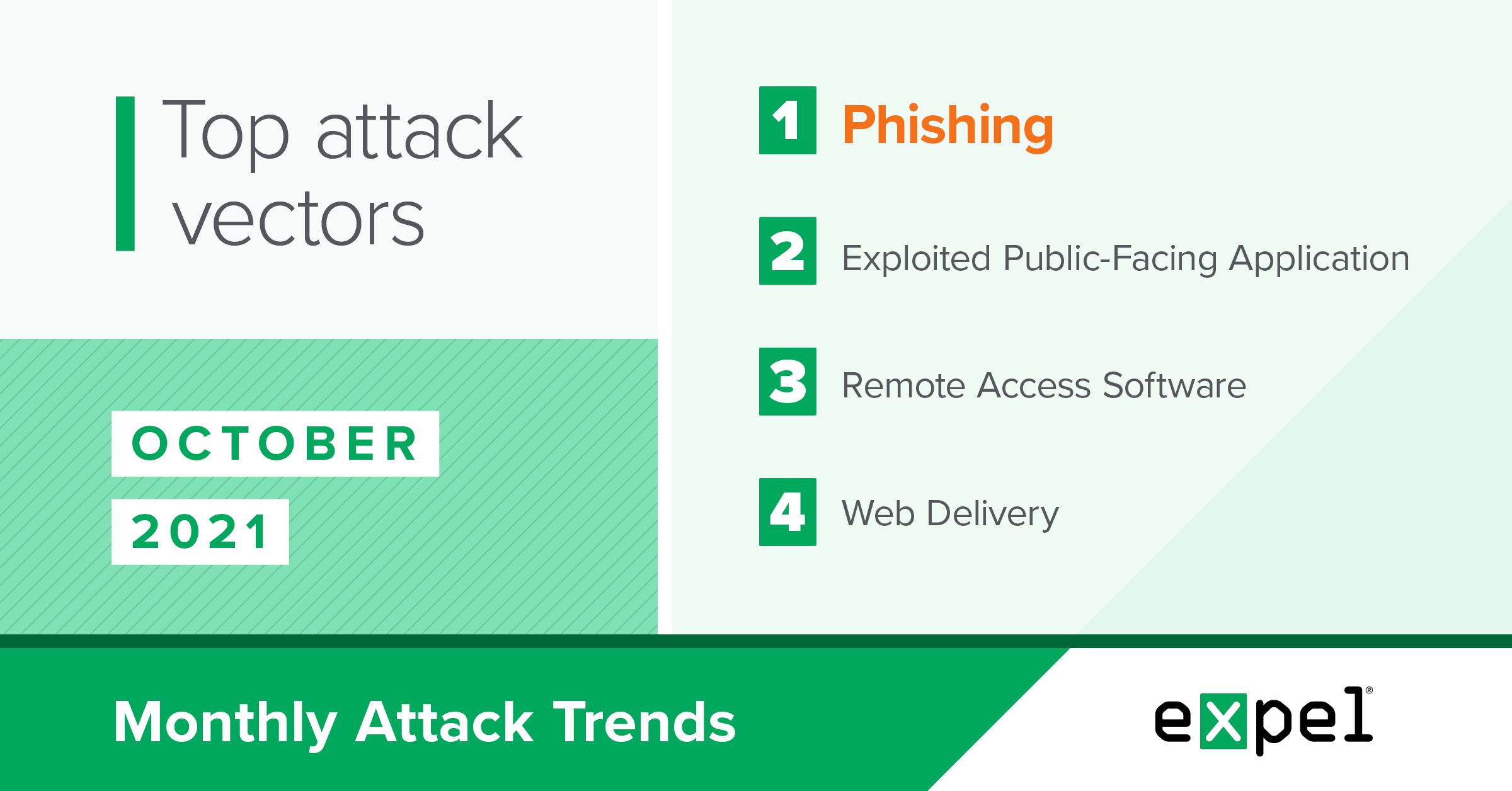
For this report, our SOC analyzed the incidents we investigated in October 2021 to determine the top attack vectors used by bad actors. In a month where we saw a wide variety of initial attack vectors, here’s what stood out:
- Voice phishing (vishing) to convince end users to install remote access software
- Cybercriminals continuing to target cryptocurrency
- A phishing incident highlighting how social engineering remains so effective for attackers
Read on to learn more and see our tips for what to do about all of the above.
Voice phishing to deploy remote access software
TL;DR: Bad actors are deploying legitimate remote access software to gain interactive access to endpoints.
In October, around three percent of the incidents we investigated involved bad actors using social engineering to manipulate end users into installing legitimate remote access software, hoping to gain an entry point. By “legitimate,” we mean software that isn’t inherently malicious but has functionality that bad actors can deploy for malicious purposes. Though not yet an alarming presence, we didn’t see any incidents of this type in September, so we’re keeping an eye out for a potential trend.
October’s incidents featured several interesting details. They each involved a Windows endpoint, which had the Remote Desktop application built-in. And rather than trying to enable or re-configure the built-in app on the Windows endpoint, the bad actors tried to install alternative remote access software, likely to bypass any security controls implemented at the network level.
Since the built-in Windows Remote Desktop application is such a well-known potential entry point for attackers, companies often have multiple security controls in place to prevent opening it up to external connections. For example, external outbound connections over port 3389, the port used by Windows Remote Desktop, are often blocked by perimeter network firewalls.
Interestingly, both of these incidents also involved vishing (voice phishing), where bad actors posing as tech support spoke to end users over the phone and instructed them to download and install the remote access software. The remote access software used in these incidents included Screen Connect, AnyDesk and TeamViewer.
Based on our investigations, it doesn’t appear the attackers were focused on lateral movement or a larger network compromise, but rather on the individual endpoints they gained access to. This aligns with a conventional Windows Tech Support scam, where scammers target random phone numbers and act as tech support services to try to make end users install a remote access application. Once these attackers gain access to a system, they’ve primarily searched common folder locations for sensitive information or for active banking sessions in the user’s web browsers.
Resilience recommendations:
- Conduct regular security awareness training for your employees, including vishing and verifying calls or download requests supposedly from company IT/tech support.
- Consider restricting the ability to install non-allowlisted applications in your environment through an endpoint detection and response (EDR) tool or built-in tools like Microsoft Applocker.
- Assess your asset inventory management to make sure all of your endpoints are accounted for and in compliance with your security standards.
Cybercriminals remain interested in cryptocurrency
TL;DR: We continued to observe a rise in malicious activity related to cryptocurrency in October using multiple initial infection vectors.
In October, half of the incident payloads we identified were found to be crypto mining software, up 11 percent from the previous month.
This continued increase in malicious crypto mining activity overlaps with the global cryptocurrency market cap setting a new record of 2.7 trillion.
In addition to exploiting public-facing vulnerabilities, bad actors also deployed crypto mining software as a web download and even a hijacked npm package. The hijacked npm package resulted from the compromise of a developer npm account for a popular JavaScript library, with this access then used to modify the library. This attack was particularly concerning because it impacted a popular and trusted programming library that was frequently downloaded during routine build and deployment processes for applications.
This type of attack is also a prime example of why layered security is so essential for cybersecurity defense. Bad actors continue to find creative ways to deliver payloads — however, in this incident, the EDR tool deployed on the endpoint quickly alerted us about the resulting mining activity after the initial compromise.
The increased monetary value of cryptocurrency is fueling not only this cryptojacking trend (which we also discussed in September), but also the trend of targeting crypto wallets. In fact, 25 percent of the malware payloads we identified in October had the ability to locate and extract information about cryptocurrency wallets. This means a grand total of 75 percent of October’s identified payloads had capabilities for generating or stealing cryptocurrency. While crypto-focused attackers have included checks for popular cryptocurrency wallets (like Metamask) in their malware for a long time, they’ve greatly increased their cryptocurrency wallet coverage to include the wide range of options that may be present on an endpoint. If an attacker can collect the private key from a cryptocurrency wallet, they can gain full access to any assets it contains.
Resilience recommendations:
- Implement network layer controls to detect and block network communications to cryptocurrency mining pools.
- Have computing resource alarms forwarded to your SIEM to alert your team of overtaxed resources deployed for cryptojacking.
- House cryptocurrency in a hardware wallet disconnected from the internet.
- Scan and identify public-facing assets using Shodan.
- Confirm your endpoint detection and response (EDR) coverage across all of your endpoints.
Phishing keeps the crown
TL;DR: Phishing continues to be the constant in the world of cybersecurity. As long as it remains so accessible and successful for attackers, it’ll stay the number one threat.
In October, 42 percent of the incidents we investigated were the result of phishing — down 19 percent from September, but still the most prevalent attack vector by far in a month when we observed a high variety of infection vectors. Microsoft Office 365 (O365) remains the primary phishing target, as all of the business email compromises (BECs) we saw this month involved the Microsoft email service.
In addition to the social engineering activity we observed for deploying remote access software, another phishing incident in October highlighted why this strategy remains so successful for attackers. This incident wasn’t particularly unique, but is a great example of the typical tactics used in a successful phishing attempt, detecting credential usage and the importance of multi-factor authentication (MFA).
The end user received an email instructing them to click a link to check an urgent voicemail. After clicking the link, the user was redirected to a credential harvesting site configured to appear like a harmless request from Microsoft to re-verify the user’s credentials before granting access to their voicemail. The good news is that when the bad actor tried to use the harvested credentials, Azure AD Identity Protection alerted us about the login attempt, which was unsuccessful thanks to MFA on the account.
Resilience recommendations:
- You know we’re going to say it — phish-resistant MFA (FIDO/webauthn) for everything and everywhere.
- Conditional access policies are a great way to help mitigate compromised logins through geo infeasibility.
- Disable legacy protocols like IMAP and POP3 (these don’t enforce MFA).
- Consider Azure AD Identity Protection to help identify suspicious mailbox logins.
Takeaways
Bad actors are using social engineering through phone calls to convince users to install remote access software and configure it as an entry point into their endpoints. This is a prime example of legitimate applications being repurposed for malicious activity, making prevention more difficult. Application allowlisting and security awareness training can be your strongest defense against this particular type of social engineering threat.
Cybercriminals also continue to target cryptocurrency as a way to maximize financial gains from their illicit activities. Cryptocurrency’s digital nature, lack of regulation and surging market cap are driving forces behind this trend. Beyond deploying malware for cryptojacking, malware with information stealing functionality are now searching endpoints for a much wider range of cryptocurrency wallets to locate private keys.
While many enterprise endpoints may not host cryptocurrency wallets, some companies have made headlines in previous months for adding cryptocurrency exposure to their balance sheets. Companies housing crypto wallets should protect these assets using a hardware wallet disconnected from the internet. And when it comes to cryptojacking, there are two essential things you should do for prevention and detection: first, make sure you don’t have gaps in your EDR deployment coverage. Next, use computing resource alarms to monitor system health and alert your team of overtaxed resources potentially deployed for cryptojacking.
Lastly, phishing and BEC remained the biggest threat and most frequent way a bad actor gained access to an environment in October, making up 42 percent of all incidents (with 100 percent of these incidents taking place in O365). Implementing phish-resistant MFA and disabling legacy authentication protocols are key steps to protect O365 accounts.
We’ll be back with insights on November’s top attack vectors. In the meantime, have questions about this month’s data or what it means for your org? Drop us a note.