MDR · 10 MIN READ · RAY PUGH AND CHRISTINE BILLIE · DEC 16, 2024 · TAGS: Phishing / Vulnerability management
Originally posted in November 2023
TL;DR
- We’re updating this blog—which we also freshened up last year—to keep you educated on the latest and greatest holiday scams our SOC is seeing
- Keep an eye out for these scams to keep your holidays Grinch-free
- Instead of battling bad actors, spend your holidays drinking eggnog, wrapping gifts, and watching holiday movies (Die Hard, anyone?)
Joe Who writes a technical how-to, when an email pings with a header that sings:
HUGE HOLIDAY DEALS FOR YOU AT WHOMART! DISCOUNTS AND STEALS FOR YOUR SHOPPING CART!
WhoMart?! he gasps. Oh, that’ll do. His wife—the beautiful Bobbie Soo Who—loves it, and their daughter does, too. He thinks of the things, all 30% off! Kittles and cubbles and barking grumpheloffs. He’ll grab that coupon, yes he will. It’s shopping season in Joyous Whoville!
The email embeds a 2-D code! It’s black and it’s white and it’s in QR mode! He focuses and clicks, then clicks it again. This will be the best holiday there ever has been!
High above Whoville in an LED-lit cave, an evil green phisher smiles a wicked green grin. There’ll be no joy in Whoville this year. There’ll be no roast beast or holiday cheer, all thanks to Joe Who, who’s doomed his career.
[Ahem. Okay, enough of that silliness.]
Our security operations center (SOC) has seen a decrease (but not disappearance) in QR code abuse lately.
In this Grinchy attack tactic, an email mentions something like a security or benefits update—or in Joe Who’s case, a holiday shopping deal—and then directs the user to a QR code link for more detail. When users then visit the website, they’re presented with a login page controlled by the attacker. And mayhem ensues.
So while this tactic isn’t as popular as it once was, it’s important to be vigilant, and treat QR codes with the same suspicion you treat unsolicited URLs. We recommend never scanning a code unless it’s received through a trusted, verified source. And if you’re using QR codes in your communications with employees, let them know to expect them.
We’re also seeing a new attack type increase in popularity this holiday season—and it’s called subscription bombing. In this type of attack, the Grinch leverages a phishing-as-a-service (PhaaS) platform to sign up an unsuspecting Who for a variety of free newsletters and mailing lists. These lists alone are harmless, but the result is an avalanche of verification and confirmation emails that overwhelm the Who in question.
The goal of this attack is multi-pronged and continuously evolving, but here’s what we know right now:
- Subscription bombs, when spread across multiple users at an org, work as an email denial of service (DoS), with the intent of overwhelming mail servers and users.
- This is often used to distract users from seeing or receiving legitimate notifications for high-risk activity, like bank transfers or non-local banking activity (aka creating a needle in a haystack).
- More recently, we’ve also seen this type of attack as a precursor to ransomware.
As attacks refine and rethink their attack strategies, subscription bombing has caught the eye of ransomware groups like Black Basta. They’ve adapted it to their needs, and will deploy mass subscriptions signups to overwhelm recipients at targeted orgs, and then pretend to be from IT to help with mailbox recovery.
This social engineering causes victims to willingly hand over remote access to their systems, so the ransomware groups can then deploy malicious software from there to further their lateral movement.
To save Christmas from Grinchy subscription bombs, you should:
- Leverage your security email gateways (SEGs) to reduce unwanted noise by raising spam filter tolerances.
- Consider rate-limiting emails, so you pause delivery if a user passes a certain threshold of new messages in a set time period.
- Deploy updated awareness training on subscription bombing, and remind people how to properly connect with IT for support.
Of course, subscription bombing isn’t the only trick in the Grinch’s bag. Here are some other things to beware of.
Fake shipping notifications
Holiday Grinches often send fake shipping notifications posing as legitimate retailers, hoping to trick recipients into providing personal information like card numbers, login credentials, or other details.
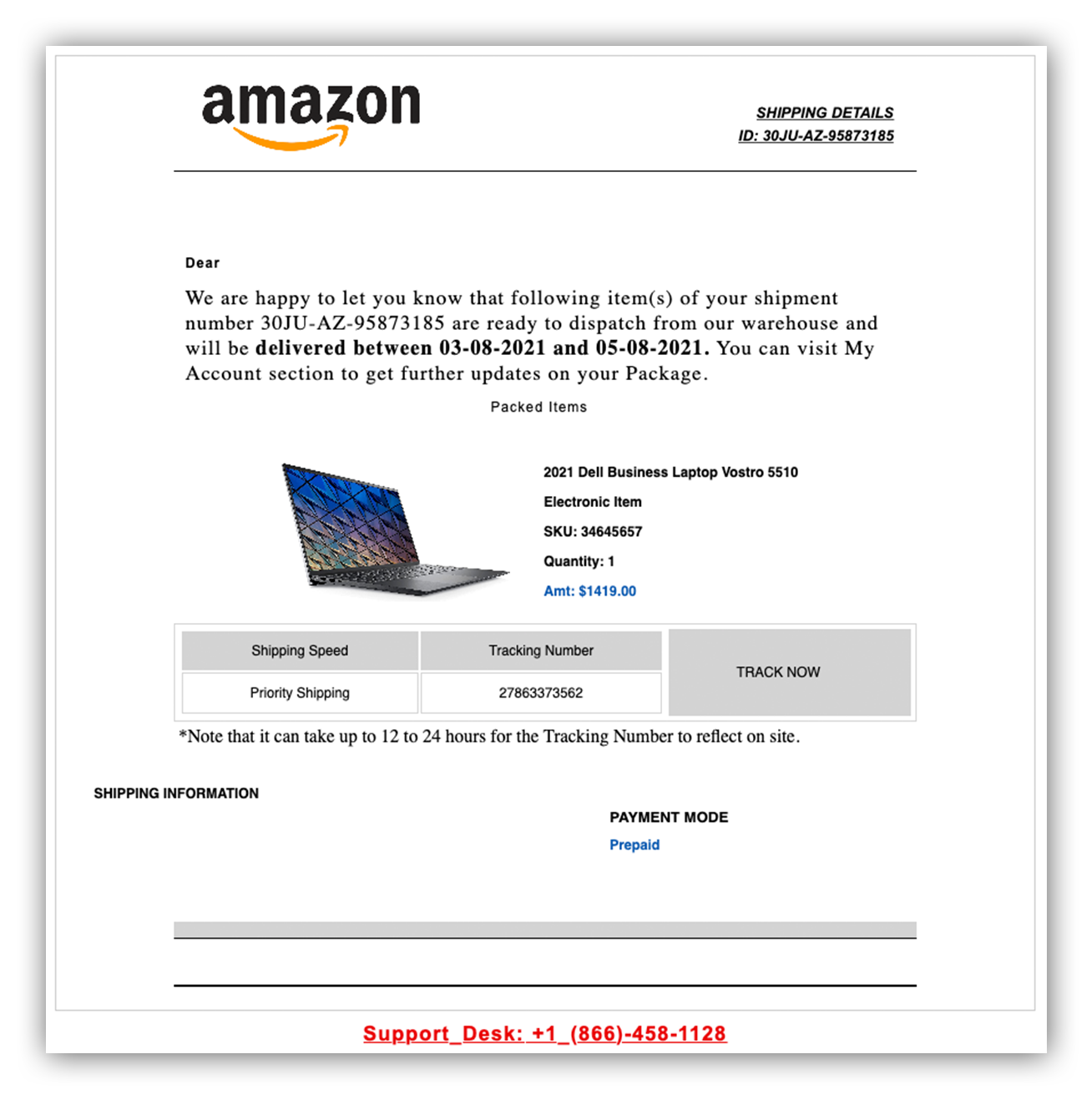
Consider this fake Amazon notification, which claimed an order was on its way to the recipient.
Fake Amazon shipping notification email
The attacker’s goal is to make the recipient think this is an actual order incorrectly placed through their account (or that maybe their account was hacked), with the large dollar amount (over $1,400 in this case) causing recipients to fear getting stuck with the bill for an item they didn’t order.
There are no clickable links in the email, which steers the reader to the “Support Desk” phone number listed in bright red at the bottom.
Our Grinchy sender hopes recipients will call that number to dispute the order, then poses as customer service on the phone to ask for “necessary account information” to help the recipient sort out the issue. If successful, this type of scam would result in the attacker obtaining account credentials, credit card numbers, or other sensitive personal information from the concerned recipient.
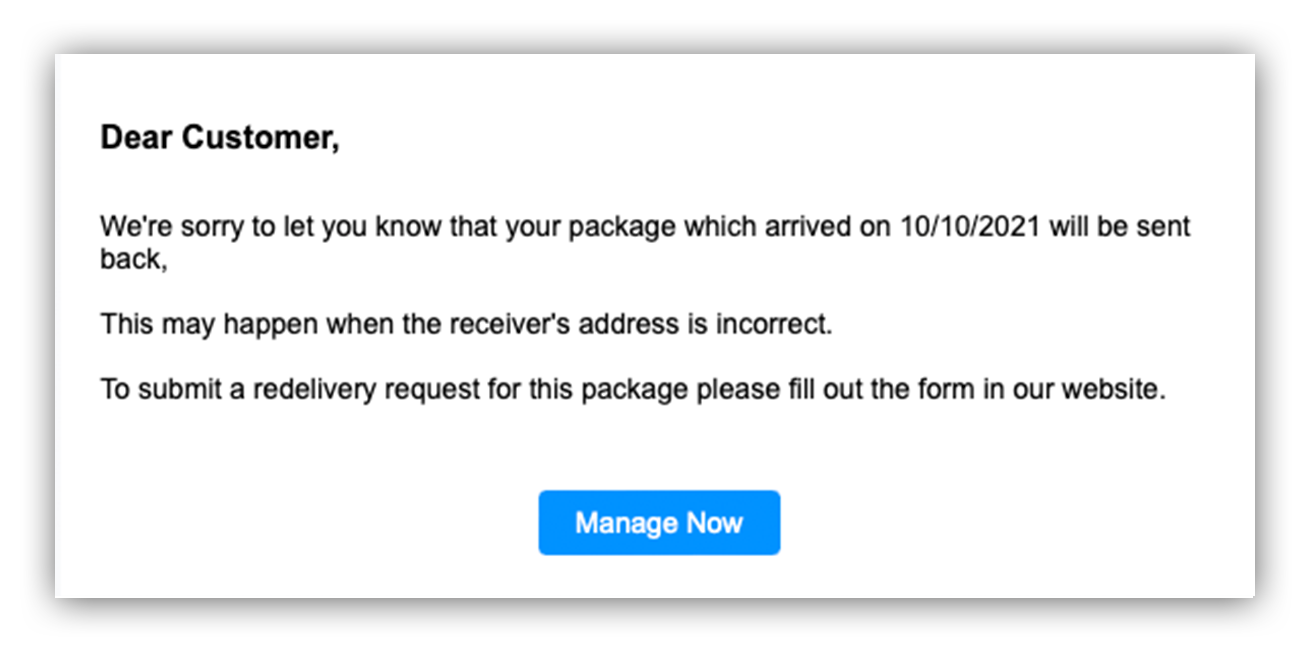
Fake shipping notices are a common attacker tactic—see another example below where a notice prompted the recipient to click a link and provide personal information to reschedule a “canceled” delivery.
Fake shipping notification email
The holiday season, when online shopping peaks, is a perfect time for would-be Grinches to raise their odds for success with these tactics.
How to avoid getting Grinched
Got an email about an order or delivery you didn’t place, or receiving shipping confirmations that look sketchy?
Here are some things you can do:
- Double-check the email address the shipping/delivery notice came from. Does it look legitimate? Does it match other shipping confirmation emails you’ve previously received from the same company for orders you placed? If not—it’s likely a scam.
- Check the email for errors—is the company’s name or other text misspelled? Is the language odd or stilted? These could be signs that the email isn’t legitimate, since companies go to great lengths to make sure their emails are error-free.
- If you have any suspicions that an email might not be legit, don’t click any links or call the phone number provided in the email—and definitely don’t give away any personal information. Instead, look up the verified customer service number for that company online and go through their legitimate support center to investigate the order or delivery. If they can’t find it, it’s a good sign it was a scam.
That’s not Santa—that’s the Grinch! (aka CEO impersonation)
The TL;DR for this one: unless it’s a regular part of your job, it’s probably safe to assume your bosses won’t ask you to do their holiday shopping.
We see many campaigns in our SOC every year where Grinches dress up like Santa and try to rope employees into helping them steal all the gifts (or gift cards, in this case).
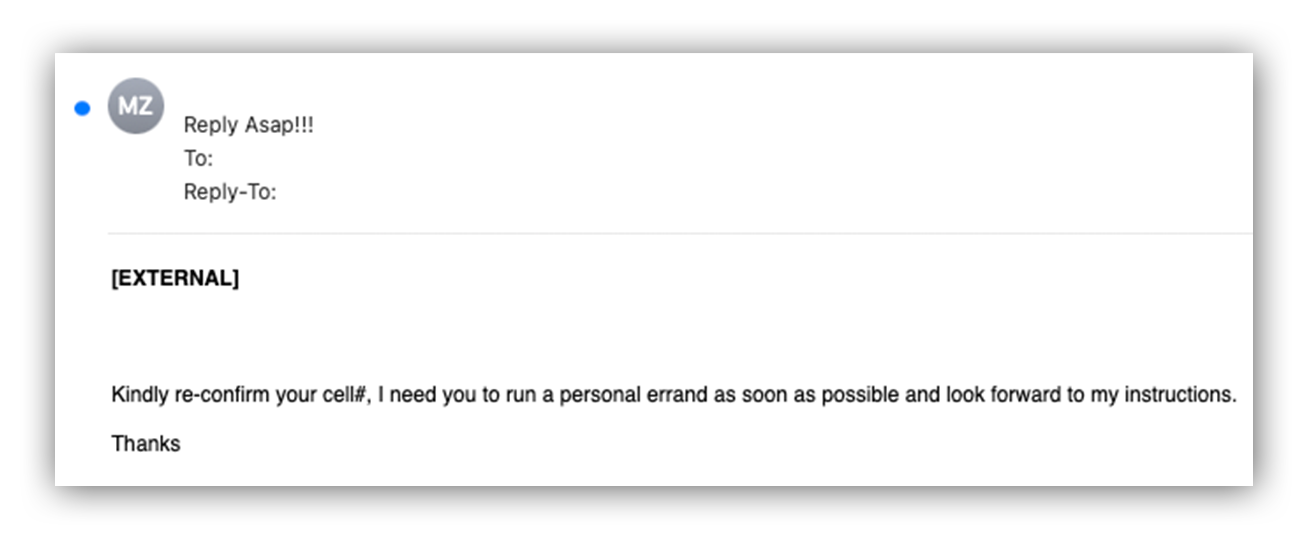
For example, in the email below, our Grinch created an email address imitating that of the company’s CEO and targeted a company employee, asking to speak offline about a “personal errand.”
CEO impersonation email request
Attackers often like to move the conversation away from email to lower the chance of discovery. Asking for cell phone numbers allows them to use calls or texting instead, which is more personal and unmonitored.
We’ve seen similar emails with language like:
- “Send me your cell phone number for an urgent task”
- “Kindly reconfirm your cell phone #, I need a task done immediately”
- “Please kindly resend your cell phone number to me”
Our gift-stealing Grinches usually ask their victims to purchase gift cards and send pictures of the redemption codes. Communicating by text/smartphone makes receiving that info quick, easy, accessible, and fairly anonymous. Victims are then out the money they spent on the gift cards with little recourse to get it back.
Attackers often use publicly-available information—like org charts—on a company’s website, or networking sites like LinkedIn to perform reconnaissance and target individuals who are newer to the company (and likely eager to impress their boss).
Which means that we frequently see interns, new graduates, and other new hires targeted in these scams.
So what can you do to keep the cyber Grinches from looking like this?
How to avoid getting Grinched
- If you receive an unexpected email from your boss asking you to contact them offline or purchase things for them that aren’t part of your regular responsibilities, first: don’t respond or give them your number.
- Second, contact your boss through another channel of communication, like your company’s instant messaging app, a new email to their verified company email address, or a phone call if you have their number. Confirm whether they sent the request. If not, it was likely a scam and you should report it to your company’s IT/security team.
- If the person reaching out isn’t someone you normally talk to, find someone in your network who can reach them through legitimate channels.
Click this link to see your Whobilation invite! (aka credential harvesting through phishing)
The hustle and bustle of the holiday season is perfect timing for another Grinchy favorite—catching busy Whos off-guard with phishing emails posing as legitimate business activities to harvest recipients’ login credentials.
A common tactic is for attackers to send an email pretending to share a legit business document (an invoice that needs signing, a contract, etc.) through a file-sharing application like DocuSign, Microsoft OneDrive, or Microsoft Office365.
The link in the phishing email then takes the recipient to a credential harvesting portal posing as a login page for one of those file-sharing services. When the recipient enters login info to access the document, the attacker captures that information and can then use it to access that recipient’s inbox (and potentially other parts of an org’s systems and applications if business email credentials are captured).
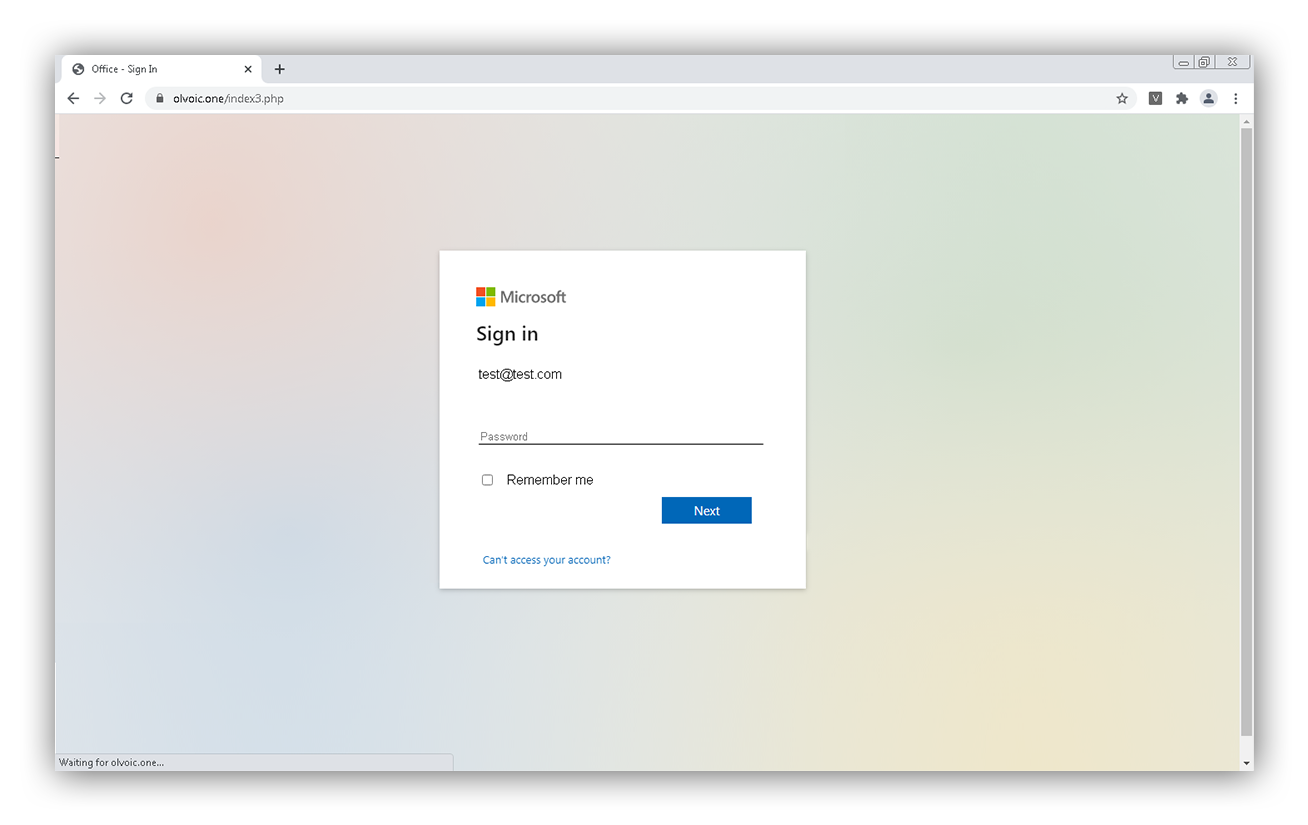
Below is an example of a fake login portal we’ve seen. There are often subtle differences (like typos, missing or different images, abnormal language) between these fake portals and the real login pages, but attackers hope busy employees won’t stop and notice these abnormalities.
Credential harvesting page posing as a Microsoft login page
This page may look legit at first glance, but the URL in the browser shows that this is definitely not a Microsoft-owned page.
Another common tactic Grinches use to collect credentials is sending recipients a PDF file to download (again, posing as a legitimate business document like an invoice or contract). Sometimes PDF, ZIP, and other files attached to phishing emails are password protected to circumvent companies’ security tech. The attacker then includes the password in the body of the email, allowing victims to open the document and interact with whatever‘s inside. This is also a common method for attackers to insert malware onto targets’ computers.
Once a Grinch has stolen recipient credentials and gained access to their inbox, they typically look for emails about invoices or other financial information to insert themselves into the conversation and attempt to divert payments to a different account they’ve set up.
In one example, we saw an attacker successfully divert payment for a person’s African safari vacation into the attacker’s account.
These phishing emails target our inclination to respond promptly to communications from co-workers, vendors, or clients if we think action is required. Subject line keywords that promote action or a sense of urgency are favorites for attackers because they prompt people to click without taking as much time to think.
How to avoid getting Grinched
- If you receive an email link to access a file, or an attached file that you aren’t anticipating, don’t click any links or open any files right away. First, double-check the sender—is this someone you know? Is their email address legitimate? If not, it could be a phishing email.
- If you find yourself on the login page for a file-sharing service, check if there’s anything off. Are there any typos? Images that won’t load? Oddly-written text or descriptions? Look at the URL—does it seem right? If you regularly use this service for work or personal file sharing, does this login page match what you usually see? If the answer to any of these questions is no, don’t put your information in—it could be a credential harvesting site posing as a login page.
- If a suspected malicious email is sent to your work account, report it to your company’s security/IT team so they can check if the same phishing campaign targeted other employees and if any accounts were compromised.
While you order your Roast Beast delivery…(aka the most important thing to do while online shopping this season)
We’ve covered some of the top scams you should keep an eye out for in your inbox this holiday season. But what about while you’re hunkered down in front of your internet browser at midnight on December 23 with a double espresso, noise-canceling headphones, and your credit cards doing your last-minute shopping?
Our most important tip—don’t reuse passwords. This will help protect you from credential stuffing attacks.
Credential stuffing is a type of cyberattack where Grinches take one set of stolen login credentials (for example, if your username and password to a site were leaked in a data breach and can now be found on the dark web), then use automation to try them across a variety of sites or applications.
It’s possible attackers will try to compromise online retailers’ systems this holiday season to access credentials for their users’ accounts, either by taking advantage of vulnerabilities in a site’s security or, more commonly, through credential harvesting like we discussed above.
If successful, it’s easy for the attackers to then use the same credentials they obtained at other retailers or institutions, like financial providers. This can allow them to place fraudulent orders, steal credit card information stored on retailers’ sites, or access their victims’ financial and email accounts (where wire fraud and other financial crimes are their targets).
As you register for accounts while online shopping this season, use unique, strong passwords (or better yet, passphrases) for each site. This helps mitigate the impact if one of your accounts is compromised by keeping your other accounts secure.
How to avoid getting Grinched
- Use different passwords for each of your accounts, particularly accounts that provide access to sensitive or personal information (like financial accounts, credit card information, or your address).
- Using a centralized password manager allows you to simply and securely store unique, complex passwords for all your accounts.
- Use multi-factor authentication (MFA) on all of your accounts. MFA requires a second verification step beyond your login info to access your account. So even if an attacker gets your credentials, MFA will help prevent unauthorized access to your account until you can reset the password. Most sites and apps have an option to enable MFA for logins to your account, often with customizable preferences.
Wrapping it all up
Remember:
- Check senders’ email addresses if an email is remotely suspicious or unexpected.
- Don’t click links or open attachments from senders you don’t recognize or aren’t expecting.
- If you click a link in an email, check the URL it brings you to—does that URL look legitimate for that company? If not, don’t put in any personal information.
- Look for abnormalities in emails or login pages that might indicate they’re fake (for example: typos, missing or unloaded images, oddly-written language, or anything else that differs from your typical experience with that site/provider).
- Don’t provide personal information to anyone claiming to be customer service over the phone unless you personally called that company’s verified customer service number.
- Double-check unusual requests from your boss through another communication channel—not just by hitting reply.
- Report anything suspicious in your work accounts to your company’s security/IT team so they can investigate and look for other instances at your org.
- Use unique passwords for each account you create.
Joe Who didn’t get fired, after all. His company used Expel, but it was still a close call. His boss came around with bonuses and well-wishing, and Joe works happily with Expel Managed Phishing.
Happy holidays, and let us know if you have comments or questions.