Security operations · 4 MIN READ · KATE DREYER · AUG 13, 2019 · TAGS: How to / Planning / SOC / Threat hunting
This is a recap of a talk two of our Expletives gave at Carbon Black’s CB Connect in San Diego. Let us know what Qs you’ve got about threat hunting — drop us a note or message us on Twitter to chat.
So you’ve decided you want to build a threat hunting program, but where do you start?
There are several paths you can follow in building a threat hunting program. And, depending on what your hunting goals are, there are lots of options for how to hunt and what tools to use.
However, figuring out exactly what approach is going to achieve your outcomes is often challenging too, especially when there are loads of fancy new tools being marketed at you every day and security buzzwords flying at you left and right. Our goal is to help you filter out the shiny stuff and think about the brass tacks of your program—and what’s going to make it (and you) successful.
What Is Threat Hunting?
Threat hunting is the process of creating a hypothesis, gathering past data, applying filtering criteria that supports the hypothesis, and investigating the leads that you generate. It’s an important proactive way to look for attackers.
If you’ve got existing security tech, you can use that for threat hunting, or you can think about what tools you’ll need to meet the goals of a new threat hunting program. And don’t forget that using tools you already have and combining that data with other information—like open-source intelligence—is an option too. We recently put together a list of the pros and cons of using different security tech for threat hunting, which is a helpful read if you’re wondering how to use the tech you already own to conduct a hunt, as well as finding new tech that can help you in generating hypotheses for successful threat hunting.
Is Hunting Right For Your Org?
There are plenty of reasons to start a threat hunting program. The biggest perk is that, when planned out and executed well, it’ll provide you with an extra layer of security. However, like any investment it takes time and resources. And so you’ll want to consider whether it’s right for you and the business you’re protecting. Before building your own threat hunting program, consider the risks facing your organization versus your available resources.
For example, if you operate in a high-risk or highly-targeted environment—maybe you work at a financial institution, a health facility or another company that stores large amounts of sensitive information about customers—then hunting probably makes sense because there are plenty of adversaries who’ll find your organization to be an attractive target. But if your organization’s risk profile is medium- to low-risk, your time and budget might be better spent on less sophisticated threats like commodity malware. If you don’t operate in a high-risk environment, hunting might distract you from things that should probably be higher on the priority list like implementing effective anti-phishing controls.
3 Tips As You Start Building Your Own Threat Hunting Program
If you’ve determined that you do want to build a threat hunting program, there are a couple considerations to mull over before knocking on your CISO’s office door to ask for more people and budget. Think through your objectives, how you’ll report on what you find and how you’ll eventually scale your hunting program.
Here are our three must-dos before you start a threat hunting program and how you can determine what information and technology to include within yours.
Must-do 1: Know Your Threat Hunting Objectives
Before you start talking about what tech you’ll use for hunting or how many people you’ll need, figure out what you’re trying to accomplish and why.
With threat hunting, you’re assuming that something has already failed and you’ve been compromised. So as you’re defining your objectives, make sure to:
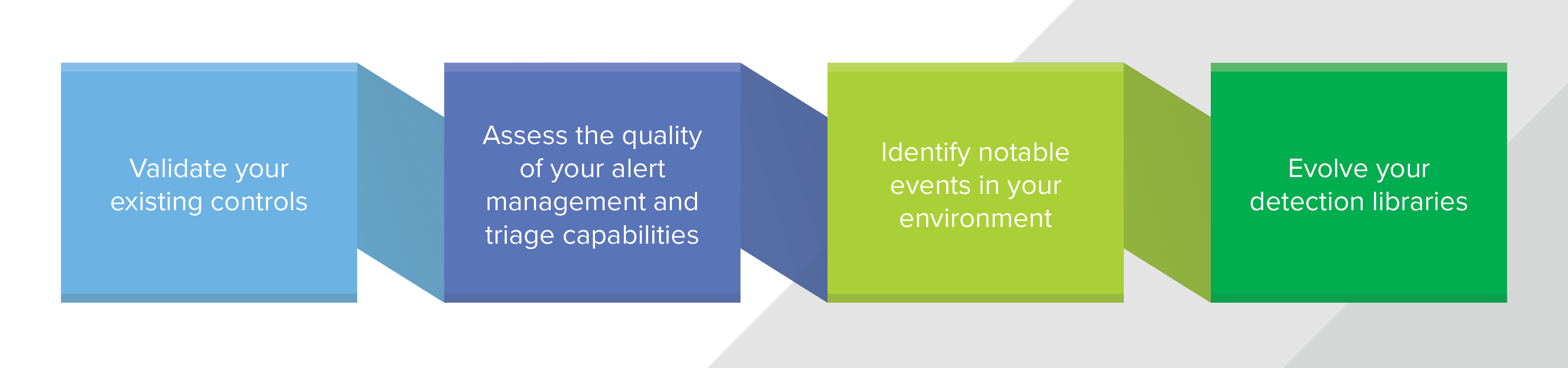
- Validate your existing controls: Your objective is to validate existing security controls. This means your hunting hypothesis should be focused on an attacker that’s already bypassed one or more of your security controls to get into your network. Where are there known (or suspected) vulnerabilities, or what controls have failed in the past?
- Assess the quality of your alert management and triage capabilities: Threat hunting is a great way to perform Quality Assurance (QA) on your alert management and triage efforts. You probably want to have someone reviewing the hunt results who didn’t spend a ton of time in the past month reviewing alerts. You’ll want to run techniques where the hypothesis is looking for activity where you would’ve expected alerts to be generated. A good example here could be looking for suspicious powershell usage.
- Identify notable events in your environment: If you’re hunting, the goal doesn’t always have to be to identify threats. Notable events are events that your hunting techniques identified that were previously unknown. You might uncover policy violations like discovering unauthorized software, or you may find activities that software or employees performed that you (or your team or customer) didn’t know about.
- Evolve your detection libraries: If you have hunting techniques in place, a long-term goal is to figure out ways to make them high enough fidelity without losing their value so that they can become detections. Similarly, if you have detections that are too prone to false positives, think about how you can build a hypothesis around them and turn them into hunting techniques.
Must-do 2: Decide How and What Information to Report On
After defining your objectives, think about how you’ll report on the findings from your hunts. Not only that, but also consider who you’re going to brief on those insights.
For example, what hunt technique are you using and why? What data did you review and what did you discover? Then talk about the outcome of your hunt, including what steps you should take—if any—to make your org more resilient in the future.
Must-do 3: Consider Long-Term Scaling of the Program
Conducting a first successful hunt is great, but how do you plan to make threat hunting part of your ongoing security practices going forward? Can you maintain an effective threat hunting program with the resources you have today or do you need new tech or more people?
Think about what scale looks like based on your goals and the business’s needs. Be prepared to have a conversation about all of your ideas on future scaling of your threat hunting program with your CISO or team lead.
Have More Questions About Threat Hunting?
To learn how Expel can help with your threat hunting program, contact us.