Justify may have the fame of becoming the thirteenth Triple Crown winner but in this release, we’re giving you three ways to save time. (So you can focus on what you love, even if that’s not horse races.)
- The Hyper-V Assembler is now available for you to download and install yourself.
- You can add research actions for investigations in a single click.
- Quick filters now enable you to see what alerts occurred in the last 72 hours.
New
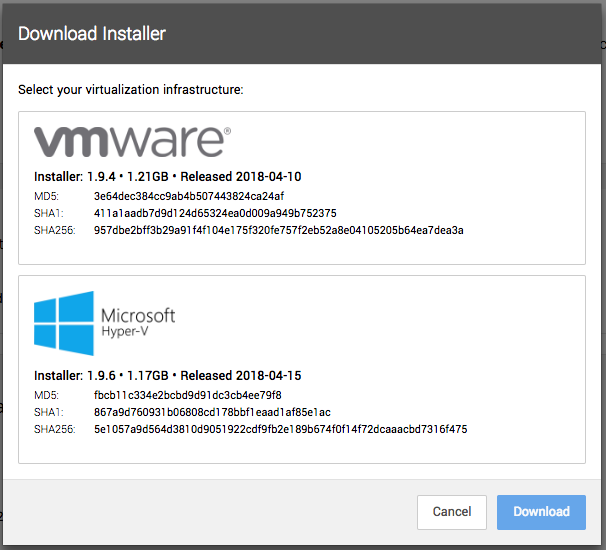
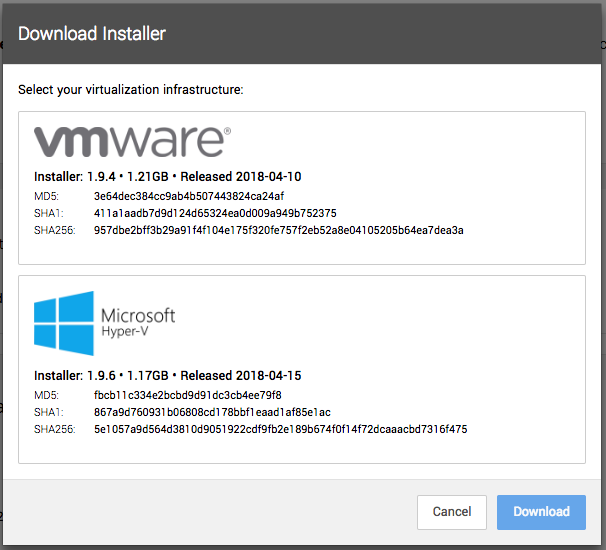
Download the Hyper-V Assembler from Workbench
At the end of April, we released a Hyper-V version of the Assembler. Now we’ve made it easier for you to download and install it yourself. In Workbench, navigate to Settings > Assemblers and click the Download button. You’ll see two options – VMware and Microsoft Hyper-V. Select the one you want to download, click the blue Download button, and you’re set!
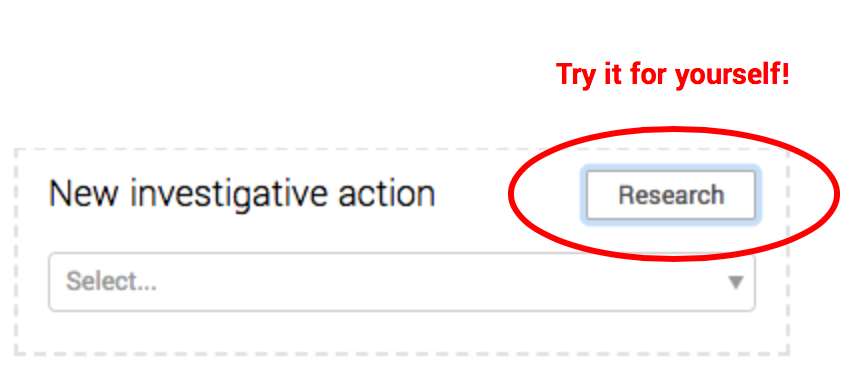
Quick-add action to speed up investigation reporting
Click, click, click. If you enjoy endless clicking as much as our analysts (which isn’t much at all), then you’ll be as happy as our analysts (high-fives all around) to hear we’ve removed a few clicks from your workflow. Now, with a single click (thanks to the new Research button), you can add a research action to the page and automatically launch a Google search for the IP, hostname, or hash you’re researching (or anything else, for that matter). This is one way we’re making sure analysts spend less time on administrative tasks and more time finding evil in your environment.
Other enhancements
- Curious what alerts occurred in the past three days? On the Alerts Grid page, we added a new quick filter so you can sort alerts by the last 72 hours.
- Want to check on the status of things? We’ve got you covered. On the Alerts page, you can now filter by All Statuses to….well, see everything, and Closed (All) to see (you guessed it) all closed alerts, regardless of the reason they were closed.
New vendor support and investigative capabilities
- If you’re using Splunk or Sumo Logic, Workbench now ingests Windows Event Logs from your SIEM. Expel will generate alerts by using custom queries to gather and normalize events of interest. If you’d like us to start monitoring this activity, you can onboard the tech yourself in the Settings > Security Devices area in Workbench or contact your engagement manager for assistance.
- We’ve also added a slew of new capabilities for FireEye HX. Analysts can now kick off requests for Agent events, Acquire file (RAW), File listing (RAW), and Registry listing (RAW) data from inside Workbench.
Other fixes (and a few odds and ends)
- We adjusted the drag-and-drop capability on the Findings page so only the heading area is active. This allows users to highlight and copy findings without accidentally reordering the report.
- Fixed an issue in the Alert Detail that made it hard to copy text out of an “info” popup.
- Fixed a problem in the Add To modal on the Alert Detail that prevented you from searching for existing incidents using just part of the incident name.
- Fixed an issue where if we had classified an incident as Threat Type: Unknown it wasn’t being counted in the Activity metrics.
- Fixed a problem on the Activity > Actions page that meant actions Assigned to me were not shown.
- Fixed a problem that prevented you from scrolling all the way down in some of the Evidence Dump windows.